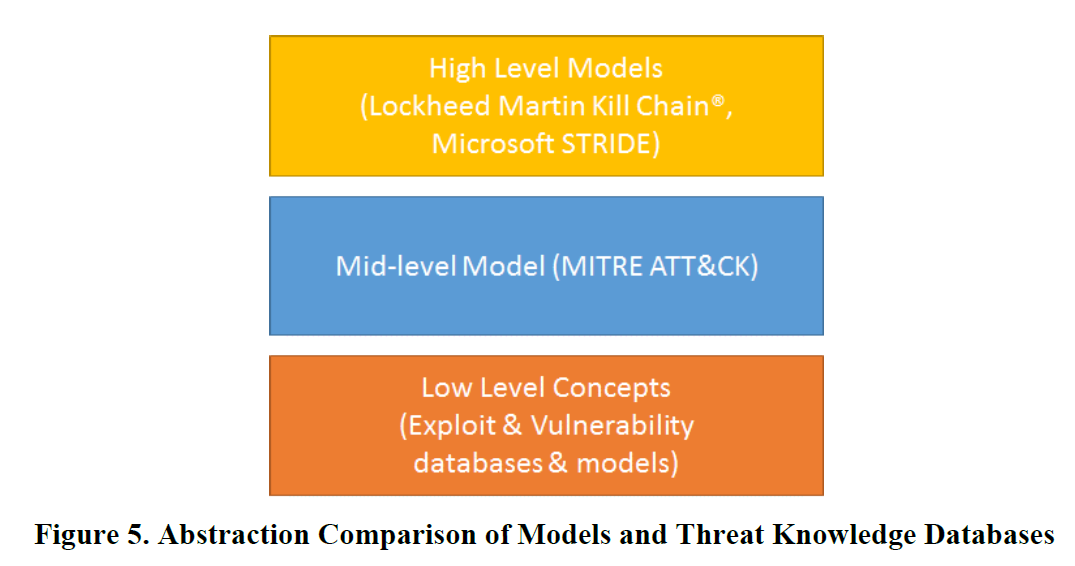
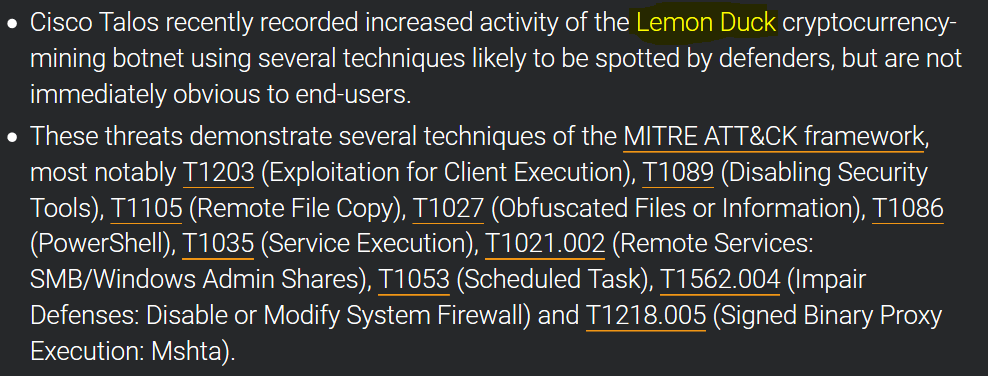
What is it?
From MITRE ATT&CK®: Design and Philosophy
MITRE ATT&CK is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s attack lifecycle and the platforms they are known to target. ATT&CK focuses on how external adversaries compromise and operate within computer information networks.
Main use cases
ATT&CK = Adversary Tactics, Techniques and Common Knowledge
- threat intelligence: What TTPs have been used against organizations like yours
- detection and analytics: Use to look for suspicious behaviors
- adversary emulation and red teaming: Mimic adversary’s TTPs when testing
- assessment and engineering
ATT&CK Tactics 1
From Enterprise Tactics Page
Reconnaissance: The adversary is trying to gather information they can use to plan future operations.
Resource Development: The adversary is trying to establish resources they can use to support operations.
Initial Access: The adversary is trying to get into your network.
Execution: The adversary is trying to run malicious code.
ATT&CK Tactics 2
From Enterprise Tactics Page
Persistence: The adversary is trying to maintain their foothold.
Privilege Escalation: The adversary is trying to gain higher-level permissions.
Defense Evasion: The adversary is trying to avoid being detected.
Credential Access: The adversary is trying to steal account names and passwords.
ATT&CK Tactics 3
From Enterprise Tactics Page
Discovery: The adversary is trying to figure out your environment.
Lateral Movement: The adversary is trying to move through your environment.
Collection: The adversary is trying to gather data of interest to their goal.
Command and Control: The adversary is trying to communicate with compromised systems to control them.
ATT&CK Tactics 4
From Enterprise Tactics Page
Exfiltration: The adversary is trying to steal data.
Impact: The adversary is trying to manipulate, interrupt, or destroy your systems and data.
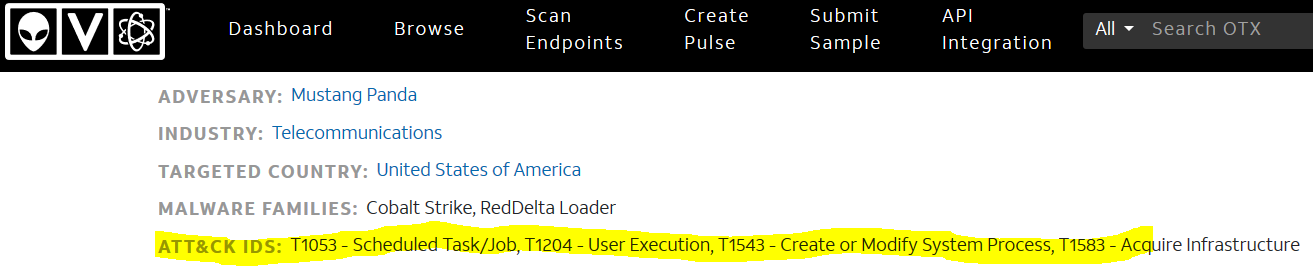
Example Use #1B
Portion of STIX file from Operation Dianxun - CN espionage campaign targeting telecommunication companies - AlienVault
{
"type": "attack-pattern",
"spec_version": "2.1",
"id": "attack-pattern--85e864e1-5dd0-4065-964d-05df90defd98",
"created": "2021-03-16T17:09:49.252Z",
"modified": "2021-03-16T17:09:49.252Z",
"name": "Scheduled Task/Job",
"description": "Adversaries may abuse task scheduling functionality to facilitate initial or recurring execution of malicious code. Utilities exist within all major operating systems to schedule programs or scripts to be executed at a specified date and time. A task can also be scheduled on a remote system, provided the proper authentication is met (ex: RPC and file and printer sharing in Windows environments). Scheduling a task on a remote system typically requires being a member of an admin or otherwise privileged group on the remote system.(Citation: TechNet Task Scheduler Security)\n\nAdversaries may use task scheduling to execute programs at system startup or on a scheduled basis for persistence. These mechanisms can also be abused to run a process under the context of a specified account (such as one with elevated permissions/privileges).",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"external_references": [
{
"source_name": "mitre-attack",
"url": "https://attack.mitre.org/techniques/T1053",
"external_id": "T1053"
},
{
"source_name": "capec",
"url": "https://capec.mitre.org/data/definitions/557.html",
"external_id": "CAPEC-557"
},
{
"source_name": "TechNet Task Scheduler Security",
"description": "Microsoft. (2005, January 21). Task Scheduler and security. Retrieved June 8, 2016.",
"url": "https://technet.microsoft.com/en-us/library/cc785125.aspx"
}
]
},
Example Use 1C Threat Actor
Portion of STIX file from Operation Dianxun - CN espionage campaign targeting telecommunication companies - AlienVault
{
"type": "threat-actor",
"spec_version": "2.1",
"id": "threat-actor--a243e69e-c2fe-4b1b-bedf-493b30198c86",
"created": "2021-03-16T17:09:49.252Z",
"modified": "2021-03-16T17:09:49.252Z",
"name": "Mustang Panda",
"description": "This threat actor targets nongovernmental organizations using Mongolian-themed lures for espionage purposes.\nIn April 2017, CrowdStrike Falcon Intelligence observed a previously unattributed actor group with a Chinese nexus targeting a U.S.-based think tank. Further analysis revealed a wider campaign with unique tactics, techniques, and procedures (TTPs). This adversary targets non-governmental organizations (NGOs) in general, but uses Mongolian language decoys and themes, suggesting this actor has a specific focus on gathering intelligence on Mongolia. These campaigns involve the use of shared malware like Poison Ivy or PlugX.\nRecently, Falcon Intelligence observed new activity from MUSTANG PANDA, using a unique infection chain to target likely Mongolia-based victims. This newly observed activity uses a series of redirections and fileless, malicious implementations of legitimate tools to gain access to the targeted systems. Additionally, MUSTANG PANDA actors reused previously-observed legitimate domains to host files.",
"aliases": [
"BRONZE PRESIDENT",
"HoneyMyte",
"Red Lich"
],
"labels": [
"activist"
],
"external_references": [
{
"source_name": "MISP Threat Actor list",
"url": "https://www.cfr.org/interactive/cyber-operations/mustang-panda"
},
{
"source_name": "MISP Threat Actor list",
"url": "https://www.crowdstrike.com/blog/meet-crowdstrikes-adversary-of-the-month-for-june-mustang-panda/"
},
{
"source_name": "MISP Threat Actor list",
"url": "https://go.crowdstrike.com/rs/281-OBQ-266/images/Report2020CrowdStrikeGlobalThreatReport.pdf"
},
{
"source_name": "MISP Threat Actor list",
"url": "https://www.secureworks.com/research/threat-profiles/bronze-president"
}
]
},