Cybersecurity Risk Assessment
Dr. Greg Bernstein
December 3rd, 2021
Risk Assessment and Management
References 1
(ISC)2 CISSP Certified Information Systems Security Professional Official Study Guide, 8th Edition by Darril Gibson; James M Stewart; Mike Chapple Published by Sybex, 2018. “CISSP Study Guide”, Chapter 2.
NIST Special Publication 800-30Revision 1. Guide for ConductingRisk Assessments. Good free source for definitions of terms and concepts. Does not include quantitative risk assessment.
NIST Special Publication 800-37 Revision 2 Risk Management Framework forInformation Systems and OrganizationsA System Life Cycle Approach for Security and Privacy. Policy document example not needed to be read for this class.
References 2
- CIS Risk Assessment Method (RAM) v2.0 for CIS Controls v8 CIS RAM v2.0 document can be downloaded for free. This is a practical approach to cybersecurity risk that works in conjunction with the CIS controls.
- Duty of Care Risk Analysis (DoCRA) Home Page
- DoCRA Draft Standard
Risk
From the CISSP Study Guide
Security is aimed at preventing loss or disclosure of data while sustaining authorized access. The possibility that something could happen to damage, destroy, or disclose data or other resources is known as risk.
My take ⇒ Something bad can happen
Risk Management
From the CISSP Study Guide
Risk management is a detailed process of identifying factors that could damage or disclose data, evaluating those factors in light of data value and countermeasure cost, and implementing cost-effective solutions for mitigating or reducing risk. The overall process of risk management is used to develop and implement information security strategies.
Asset
From the CISSP Study Guide
An asset is anything within an environment that should be protected. It is anything used in a business process or task. It can be a computer file, a network service, a system resource, a process, a program, a product, an IT infrastructure, a database, a hardware device, intellectual property, …
Asset Valuation
From the CISSP Study Guide
Asset valuation is a dollar value assigned to an asset based on actual cost and nonmonetary expenses. These can include costs to develop, maintain, administer, advertise, support, repair, and replace an asset; they can also include more elusive values, such as public confidence, industry support, productivity enhancement, knowledge equity, and ownership benefits.
Threat
From the CISSP Study Guide
Any potential occurrence that may cause an undesirable or unwanted outcome for an organization or for a specific asset is a threat. Threats are any action or inaction that could cause damage, destruction, alteration, loss, or disclosure of assets or that could block access to or prevent maintenance of assets. Threats can be large or small and result in large or small consequences. They can be intentional or accidental. They can originate from people, organizations, hardware, networks, structures, or nature.
Threat Agent
From the CISSP Study Guide
Threat agents intentionally exploit vulnerabilities. Threat agents are usually people, but they could also be programs, hardware, or systems.
Threat Event
From the CISSP Study Guide
Threat events are accidental and intentional exploitations of vulnerabilities. They can also be natural or man-made. Threat events include fire, earthquake, flood, system failure, human error (due to a lack of training or ignorance), and power outage.
Vulnerability
From the CISSP Study Guide
The weakness in an asset or the absence or the weakness of a safeguard or countermeasure is a vulnerability.
In other words, a vulnerability is a flaw, loophole, oversight, error, limitation, frailty, or susceptibility in the IT infrastructure or any other aspect of an organization. If a vulnerability is exploited, loss or damage to assets can occur.
Exposure
From the CISSP Study Guide
Exposure is being susceptible to asset loss because of a threat; there is the possibility that a vulnerability can or will be exploited by a threat agent or event.
Quantifying Risk
From the CISSP Study Guide
Risk is the possibility or likelihood that a threat will exploit a vulnerability to cause harm to an asset. It is an assessment of probability, possibility, or chance. The more likely it is that a threat event will occur, the greater the risk. Every instance of exposure is a risk. When written as a formula, risk can be defined as follows:
\[risk = threat * vulnerability\]
Safeguards
A safeguard, security control, or countermeasure is anything that removes or reduces a vulnerability or protects against one or more specific threats. A safeguard can be installing a software patch, making a configuration change, hiring security guards, altering the infrastructure, modifying processes, improving the security policy, training personnel more effectively, electrifying a perimeter fence, installing lights, and so on… Safeguards are the only means by which risk is mitigated or removed.
Elements of Risk
From the CISSP Study Guide

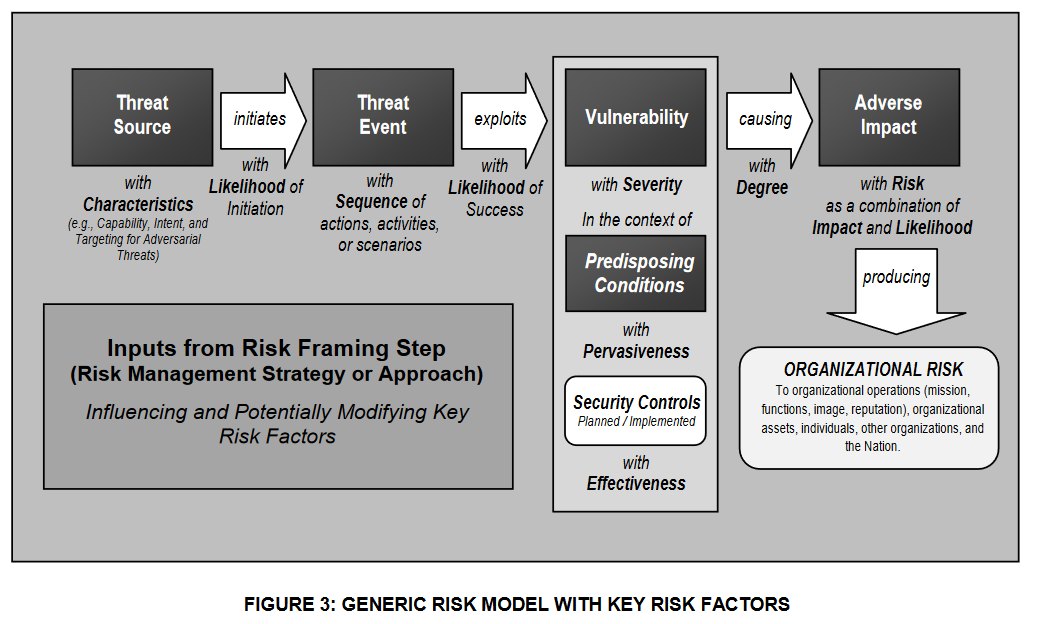
NIST Risk Model
From NIST SP800-30rev1
Duty of Care Risk Analysis (DoCRA)
Let’s get legal
From DoCRA Standard Draft
As organizations engage in public life they offer benefits to themselves and others, but they also pose potential harm. Legal authorities and the public hold those organizations accountable for balancing benefit and harm using concepts such as “reasonableness,” “duty of care,” and “due care.” Duty of Care Risk Analysis helps organizations determine whether they apply safeguards that appropriately protect others from harm while presenting a reasonable burden to themselves.
DoCRA Principles
From CIS RAMv2.0, a summary of the DoCRA draft standard
- Risk analysis must consider the interests of all parties that may be harmed by the risk.
- Risks must be reduced to a level that would not require a remedy to any party.
- Safeguards must not be more burdensome than the risks they protect against.
remedy: a way of finding a solution using the law
DoCRA Practices 1
From CIS RAMv2.0, a summary of the DoCRA draft standard
- Risk analysis considers the likelihood that threats could create magnitudes of impact.
- Tolerance thresholds are stated in plain language and are applied to each factor in a risk analysis.
- Impact and likelihood scores have a qualitative component that concisely states the concerns of interested parties, authorities, and the assessing organization.
DoCRA Practices 2
From CIS RAMv2.0, a summary of the DoCRA draft standard
- Impact and likelihood scores are derived by a quantitative calculation that permits comparability among all evaluated risks, safeguards, and against risk acceptance criteria.
- Impact definitions ensure that the magnitude of harm to one party is equated with the magnitude of harm to others.
- Impact definitions should have an explicit boundary between those magnitudes that would be acceptable to all parties and those that would not be.
DoCRA Practices 3
From CIS RAMv2.0, a summary of the DoCRA draft standard
- Impact definitions address; the organization’s mission or utility to explain why the organization and others engage risk, the organization’s self-interested objectives, and the organization’s obligations to protect others from harm.
- Risk analysis relies on a standard of care to analyze current controls and recommended safeguards.
DoCRA Practices 4
From CIS RAMv2.0, a summary of the DoCRA draft standard
- Risk is analyzed by subject matter experts who use evidence to evaluate risks and safeguards.
- Risk assessments cannot evaluate all foreseeable risks. Therefore, risk assessments re-occur to identify and address more risks over time.
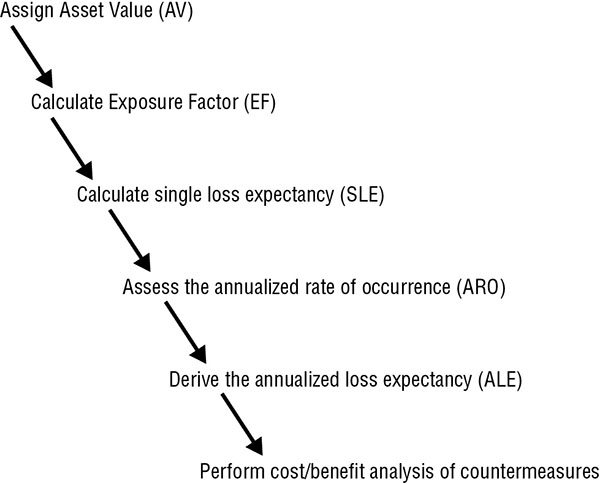
Quantitative Risk Analysis
The Steps
From the CISSP Study Guide
Inventory assets, and assign a value (asset value, or AV).
Research each asset, and produce a list of all possible threats of each individual asset. For each listed threat, calculate the exposure factor (EF) and single loss expectancy (SLE).
Perform a threat analysis to calculate the likelihood of each threat being realized within a single year—that is, the annualized rate of occurrence (ARO).
The Steps - continued
From the CISSP Study Guide
Derive the overall loss potential per threat by calculating the annualized loss expectancy (ALE).
Research countermeasures for each threat, and then calculate the changes to ARO and ALE based on an applied countermeasure.
Perform a cost/benefit analysis of each countermeasure for each threat for each asset. Select the most appropriate response to each threat.
Quantitative Risk Flow
Reality Check 1
- Seriously Professor you are going to do all these steps?
- There are a lot of “research” steps here, who has time?
- Have you ever done anything like this in your entire career
Reality Check 2
- In a large company or insurance firm you may be part of a team conducting this analysis
- You may only be ask to perform a subset of these steps
- You may get (buy, be given) “research” results to use for certain steps
My Experience 1
Example threats in terms of frequency of occurrence (guess my assets):
- Burnout
- Backhoes
- Anchor Drags
- Tornado, Hurricanes, Earthquakes
My Experience 2
My customers asset: fiber optic based communication networks
- Most frequent threat: laser transmitter burnout
- Backhoe (construction equipment), Ship anchors cutting fiber optic cables
My Experience 3
For important network hardware suppliers (like the company I was at) are required to compute reliability information based on establish failure rates for devices.
We then offer many different safeguards (in networking these are known as protection and restoration schemes) each with different advantages and costs.
Dealing with Risk
Approaches
From the CISSP Study Guide
- Reduce or mitigate
- Assign or transfer
- Accept
- Deter
- Avoid
- Reject or ignore
Risk Mitigation
From the CISSP Study Guide
Risk mitigation is the implementation of safeguards and countermeasures to eliminate vulnerabilities or block threats. Picking the most cost-effective or beneficial countermeasure is part of risk management, but it is not an element of risk assessment. In fact, countermeasure selection is a post-risk-assessment or post-risk-analysis activity.
Risk Assignment
From the CISSP Study Guide
Assigning risk or transferring risk is the placement of the cost of loss a risk represents onto another entity or organization. Purchasing insurance and outsourcing are common forms of assigning or transferring risk.
Risk Acceptance
From the CISSP Study Guide
Accepting risk, risk tolerance, or acceptance of risk is the result after a cost/benefit analysis shows countermeasure costs would outweigh the possible cost of loss due to a risk. It also means that management has agreed to accept the consequences and the loss if the risk is realized.
Danger!
Risk Avoidance
From the CISSP Study Guide
Risk avoidance is the process of selecting alternate options or activities that have less associated risk than the default, common, expedient, or cheap option.
Risk Rejection
From the CISSP Study Guide
A final but unacceptable possible response to risk is to reject risk or ignore risk. Denying that a risk exists and hoping that it will never be realized are not valid or prudent due-care responses to risk.
This Class
- Risk Mitigation
- Risk Avoidance