Security Controls
Dr. Greg Bernstein
November 15th, 2021
Security Controls
References
Security and Privacy Controls for Information Systems and Organizations, NIST Special Publication 800-53 Revision 5 September 2020.
The 20 CIS Controls & Resources Practical Guide from the Center for Internet Security.
Security Controls Definition
Security controls are the safeguards or countermeasures employed within a system or an organization to protect the confidentiality, integrity, and availability of the system and its information and to manage information security risk.
General Types
- Physical: doors with locks, barbed wire fences, moats with alligators, draw bridges, etc…
- Technical: network firewalls, passwords, ACLs, cryptography, etc…
- Administrative: policies (more later)
NIST Catalog of Controls (SP800-53) 1
Security and Privacy Controls for Information Systems and Organizations, NIST Special Publication 800-53 Revision 5 September 2020.
Controls can be viewed as descriptions of the safeguards and protection capabilities appropriate for achieving the particular security and privacy objectives of the organization and reflecting the protection needs of organizational stakeholders. Controls are selected and implemented by the organization in order to satisfy the system requirements. Controls can include administrative, technical, and physical aspects.
NIST Catalog of Controls (SP800-53) 2
Security and privacy controls described in this publication have a well-defined organization and structure. For ease of use in the security and privacy control selection and specification process, controls are organized into 20 families. Each family contains controls that are related to the specific topic of the family.
NIST Control Families (SP800-53) 1
| Family | Family |
|---|---|
| Access Control | Physical and Environmental Protection |
| Awareness and Training | Planning |
| Audit and Accountability | Program Management |
NIST Control Families (SP800-53) 2
| Family | Family |
|---|---|
| Assessment, Authorization, and Monitoring | Personnel Security |
| Configuration Management | PII Processing and Transparency |
| Contingency Planning | Risk Assessment |
NIST Control Families (SP800-53) 3
| Family | Family |
|---|---|
| Identification and Authentication | System and Services Acquisition |
| Incident Response | System and Communications Protection |
| Maintenance | System and Information Integrity |
| Media Protection | Supply Chain Risk Management |
Center for Internet Security Controls
Why CIS Control List
NIST SP 800-53r5: “provides a catalog of security and privacy controls for information systems and organizations”. Very well defined and comprehensive, but long 483 pages and not prioritized.
“The CIS Controls™ are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks.”
CIS Controls A
Inventory and Control of Hardware Assets
Inventory and Control of Software Assets
Data Protection
CIS Controls B
Secure Configuration of Enterprise Assets and Software More
Account Management
Access Control Management
CIS Controls C
Continuous Vulnerability Management More
Audit Log Management More
Email, Web Browser, and Protections
CIS Controls D
Malware Defenses
Data Recovery
Network Infrastructure Management
CIS Controls E
Network Monitoring and Defense
Security Awareness and Skills Training
Service Provider Management
CIS Controls F
Application Software Security
Incident Response and Management
Penetration Testing
Continuous Vulnerability Management: What
From CIS Vulnerability Management
Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers.
Continuous Vulnerability Management: Why
From CIS Vulnerability Management
Cyber defenders must operate in a constant stream of new information: software updates, patches, security advisories, threat bulletins, etc. Understanding and managing vulnerabilities has become a continuous activity, requiring significant time, attention, and resources.
Attackers have access to the same information and can take advantage of gaps between the appearance of new knowledge and remediation.
Continuous Vulnerability Management: How
From CIS Vulnerability Management
Utilize an up-to-date SCAP-compliant vulnerability scanning tool to automatically scan all systems on the network on a weekly or more frequent basis to identify all potential vulnerabilities on the organization’s systems.
Deploy automated software update tools in order to ensure that the operating systems are running the most recent security updates provided by the software vendor.
Security Content Automation Protocol (SCAP)
From Wikipedia: SCAP
The Security Content Automation Protocol (SCAP) is a method for using specific standards to enable automated vulnerability management, measurement, and policy compliance evaluation of systems deployed in an organization, including e.g., FISMA (Federal Information Security Management Act, 2002) compliance. The National Vulnerability Database (NVD) is the U.S. government content repository for SCAP. An example of an implementation of SCAP is OpenSCAP.
SCAP Components
From Wikipedia: SCAP, SCAP is built on previous standards
- Common Vulnerabilities and Exposures (CVE)
- Common Platform Enumeration (CPE)
- Common Vulnerability Scoring System (CVSS)
- Extensible Configuration Checklist Description Format (XCCDF)
- And more…
SCAP Compliant Scanners
- Commercial from: Joval, Rapid7, ThreatGuard, IBM, MicroSoft, Tenable (Nessus)
- Open Source: OpenSCAP (mostly Linux)
Secure Configuration: What
Establish, implement, and actively manage (track, report on, correct) the security configuration of mobile devices, laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
Secure Configuration: Why 1
As delivered by manufacturers and resellers, the default configurations for operating systems and applications are normally geared towards ease-of-deployment and ease-of-use – not security. Basic controls, open services and ports, default accounts or passwords, older (vulnerable) protocols, preinstallation of unneeded software; all can be exploitable in their default state.
Secure Configuration: Why 2
Developing configuration settings with good security properties is a complex task beyond the ability of individual users, requiring analysis of potentially hundreds or thousands of options in order to make good choices. Even if a strong initial configuration is developed and installed, it must be continually managed to avoid security “decay” as software is updated or patched, new security vulnerabilities are reported, and configurations are “tweaked” to allow the installation of new software or support new operational requirements. If not, attackers will find opportunities to exploit both network accessible services and client software.
Secure Configuration: How
Maintain documented, standard security configuration standards for all authorized operating systems and software.
Utilize a Security Content Automation Protocol (SCAP) compliant configuration monitoring system to verify all security configuration elements, catalog approved exceptions, and alert when unauthorized changes occur.
Secure Configurations: Where
The National Checklist Program (NCP), defined by the NIST SP 800-70, is the U.S. government repository of publicly available security checklists (or benchmarks) that provide detailed low level guidance on setting the security configuration of operating systems and applications.
Secure Configurations: Formats
- Prose – instructions on how to configure securely
- The Extensible Configuration Checklist Description Format (XCCDF) is an XML format specifying security checklists, benchmarks and configuration documentation. XCCDF development is being pursued by NIST, the NSA, The MITRE Corporation, and the US Department of Homeland Security. XCCDF is intended to serve as a replacement for the security hardening and analysis documentation written in prose. XCCDF is used by the Security Content Automation Protocol.
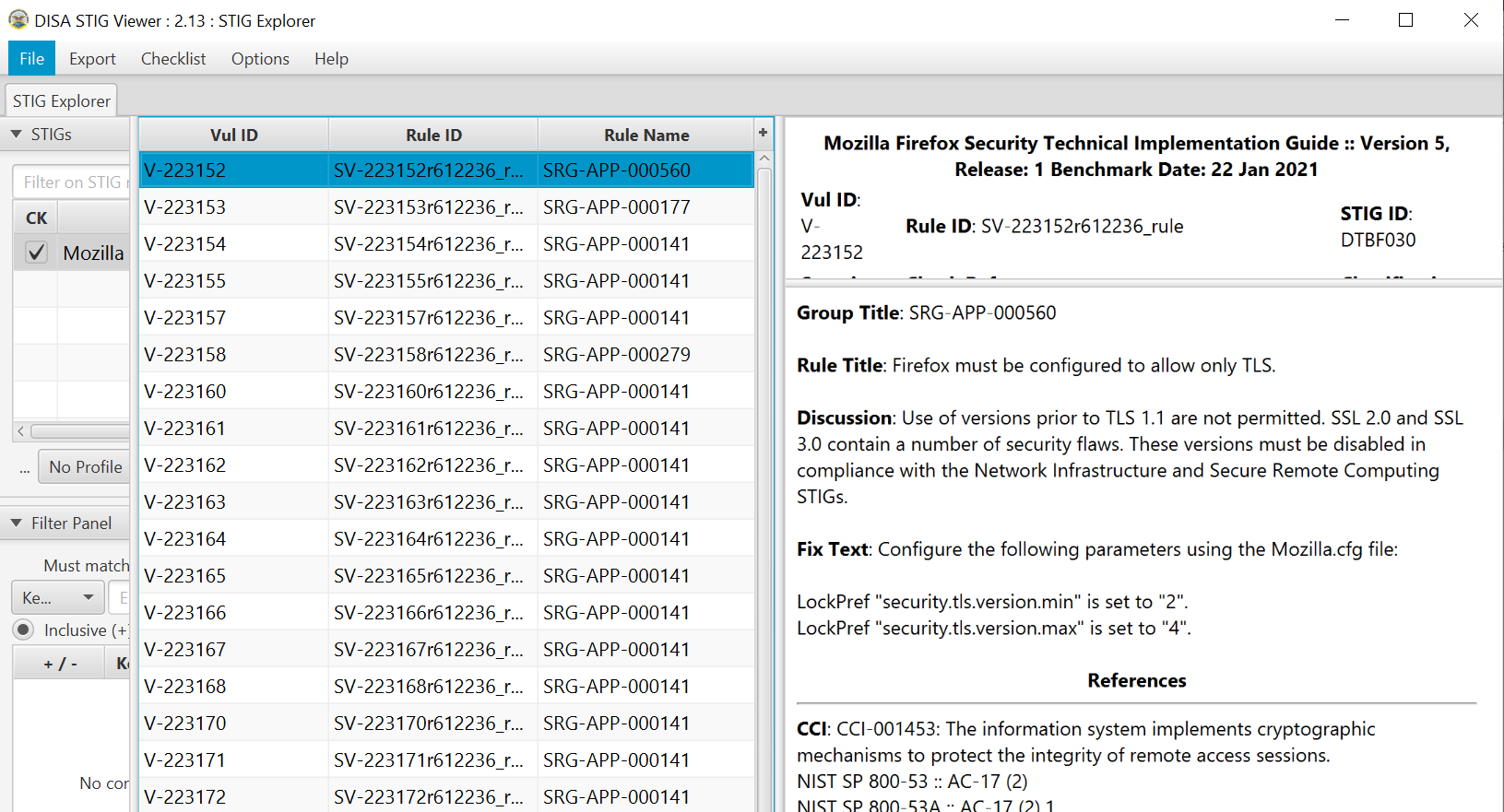
Checklist Example FireFox
Firefox rules in STIG (Security Technical Implementation Guide) viewer, XCCDF format
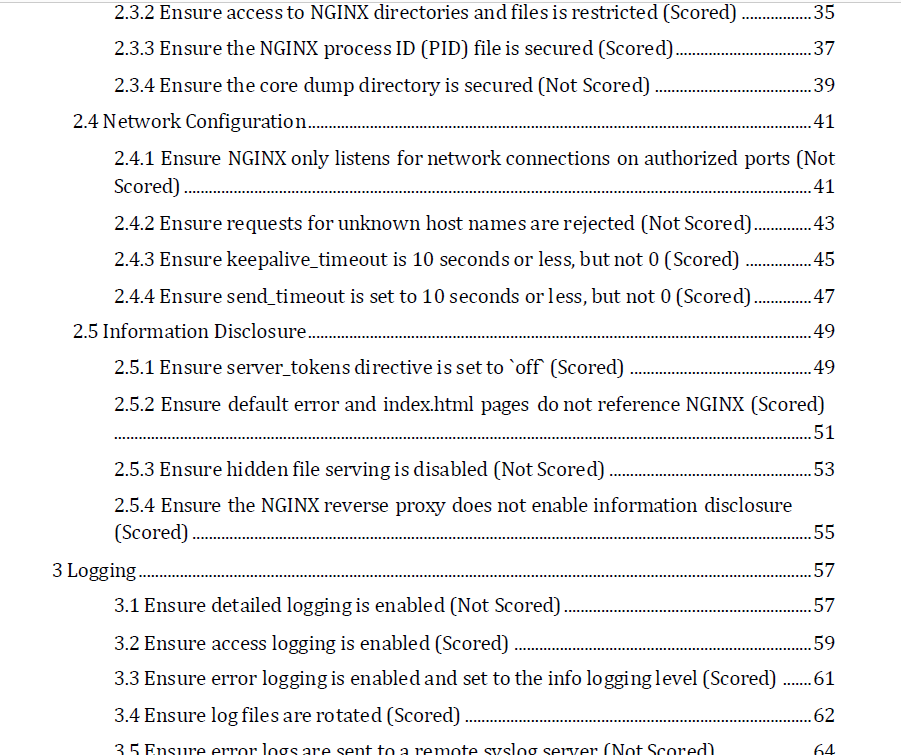
Checklist Example NGINX
Portion of a CIS Benchmark for the NGINX webserver (132 pages total)
Audit Logs: What
From CIS Audi Logs
Collect, manage, and analyze audit logs of events that could help detect, understand, or recover from an attack.
Audit Logs: Why 1
From CIS Audit Logs
Deficiencies in security logging and analysis allow attackers to hide their location, malicious software, and activities on victim machines. Even if the victims know that their systems have been compromised, without protected and complete logging records they are blind to the details of the attack and to subsequent actions taken by the attackers. Without solid audit logs, an attack may go unnoticed indefinitely and the particular damages done may be irreversible.
Audit Logs: Why 2
From CIS Audit Logs
Sometimes logging records are the only evidence of a successful attack. Many organizations keep audit records for compliance purposes, but attackers rely on the fact that such organizations rarely look at the audit logs, and they do not know that their systems have been compromised. Because of poor or nonexistent log analysis processes, attackers sometimes control victim machines for months or years without anyone in the target organization knowing, even though the evidence of the attack has been recorded in unexamined log files.
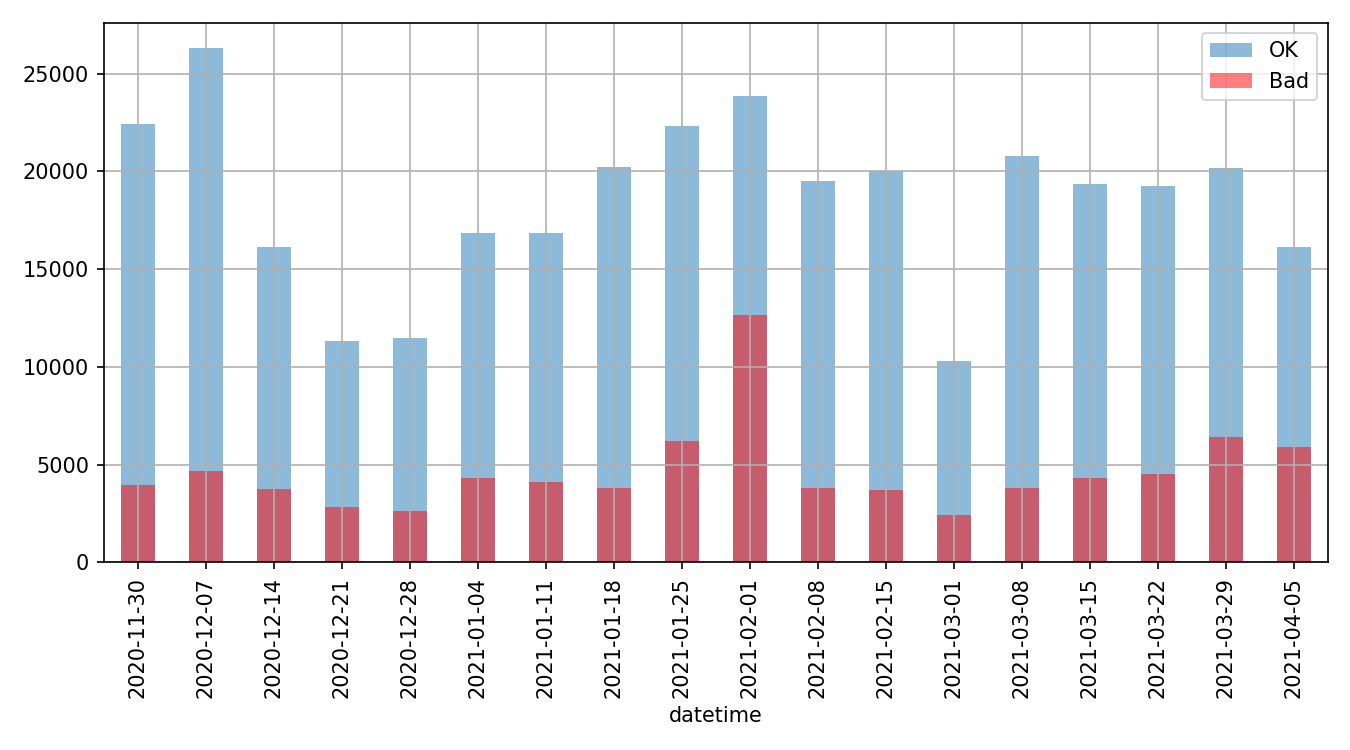
Web Site Log Example 1
Weekly visit counts success and failures
Web Site Log Example 2
From where? “Good” document requests only
United States 51927 Germany 10452 France 7296
Netherlands 5191 Singapore 5172 India 3747
China 3744 Russia 1992 Canada 1928
Luxembourg 741 Pakistan 671 United Kingdom 495
Taiwan 462 Turkey 442 Czechia 381
Ireland 311 Israel 301 Finland 271
South Korea 231 Ukraine 229 Vietnam 224
Japan 211 Romania 204 Hong Kong 203
Spain 199 Norway 188 Poland 182
Thailand 170 Sweden 138 Philippines 129
Iran 128 Italy 118 Belgium 113
Australia 108 Brazil 98 Bangladesh 96
Malaysia 95 Greece 92 Egypt 88
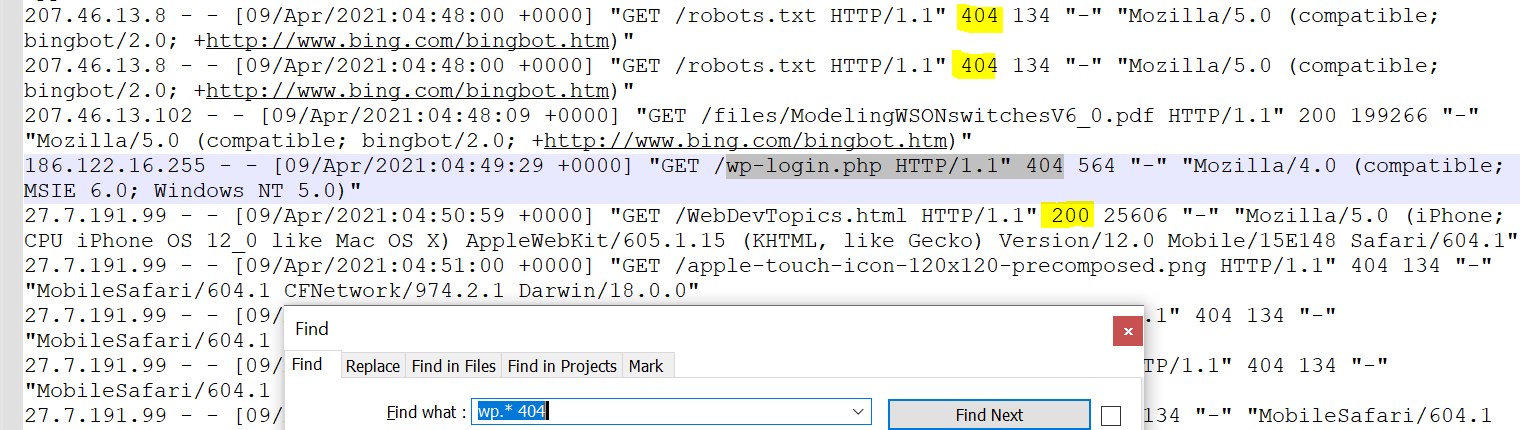
Indonesia 86Web Site Log Example 3
Raw log examination
Recent Developments: OSCAL
OSCAL Definition/What
From NIST: OSCAL, Apri 2021
NIST, in collaboration with industry, is developing the Open Security Controls Assessment Language (OSCAL). OSCAL is a set of formats expressed in XML, JSON, and YAML. These formats provide machine-readable representations of control catalogs, control baselines, system security plans, and assessment plans and results.
OSCAL Why?
From NIST: OSCAL, Control-based information expressed using OSCAL formats allows you to:
- Easily access control information from security and privacy control catalogs
- Establish and share machine-readable control baselines
- Maintain and share actionable, up-to-date information about how controls are implemented in your systems
- Automate the monitoring and assessment of your system control implementation effectiveness*