Phishing
Dr. Greg Bernstein
October 1st, 2021
Phishing
Phishing Definition
From Wikipedia: Phishing
Phishing is the fraudulent attempt to obtain sensitive information or data, such as usernames, passwords and credit card details or other sensitive details, by impersonating oneself as a trustworthy entity in a digital communication. Typically carried out by email spoofing, instant messaging, and text messaging, phishing often directs users to enter personal information at a fake website which matches the look and feel of the legitimate site.
Types of Phishing
From Wikipedia: Phishing
- Spear phishing – Targeting specific individuals
- Whaling – targeting high value individuals
- Catphishing and catfishing – related to fraud in social networks and romance
- Voice phishing (vishing) – via voice technologies
- SMS phishing (Smishing) – via texts
Phishing Resources
- General definition Wikipedia: Phishing
- FTC How to recognize and avoid phishing scams
- The Anti Phishing Working Group is the international coalition unifying the global response to cybercrime across industry, government and law-enforcement sectors and NGO communities. See their latest reports
Phishing Additional and Technical Resources
Key Ingredients of a Phishing Attack
- Email with a lure: An subject line designed to get you to open rather than discard the email. Sender is frequently impersonated
- Email content with hook link: More coercion to get you to click a link in the email.
- Phishing website: A site designed to impersonate another site with the goal of stealing your credentials or other information.
Sophisticated Examples
We all receive junk email however as students or professors we are not subject to the more sophisticated phishing attacks. To see examples of more sophisticated phishing attacks see Credential Harvesting at Scale Without Malware by Palo Alto NEtworks, September 30th, 2021.
Business Email Compromise (BEC) 1
From Attackers in Executive Clothing - BEC continues to separate orgs from their money), June 2021
In today’s world of threat research, the focus tends to be on the overtly malicious practice of distributing and installing malware on end systems. But this is far from the complete picture of what threats organizations face. One of the most, if not the most, costly is something far less sophisticated: Business Email Compromise (BEC). BEC can take a wide array of different forms, but its goal is relatively simple — trick an unsuspecting user into giving them something.
Business Email Compromise (BEC) 2
From Attackers in Executive Clothing - BEC continues to separate orgs from their money), June 2021
Looking at conservative estimates, business email compromise losses are in the billions, with the FBI stating in 2020 alone the loses approached $1.8 Billion. This is an extremely lucrative enterprise with a low barrier to entry. Other forms of cybercrime are tougher to enter because the actor needs to source the malware they are going to distribute and have enough knowledge to set up and run the associated infrastructure — or at the very least, pay someone who does.
Phishing Prevention
Technical Means
- Threat Sharing
- Email Filtering
- IPS
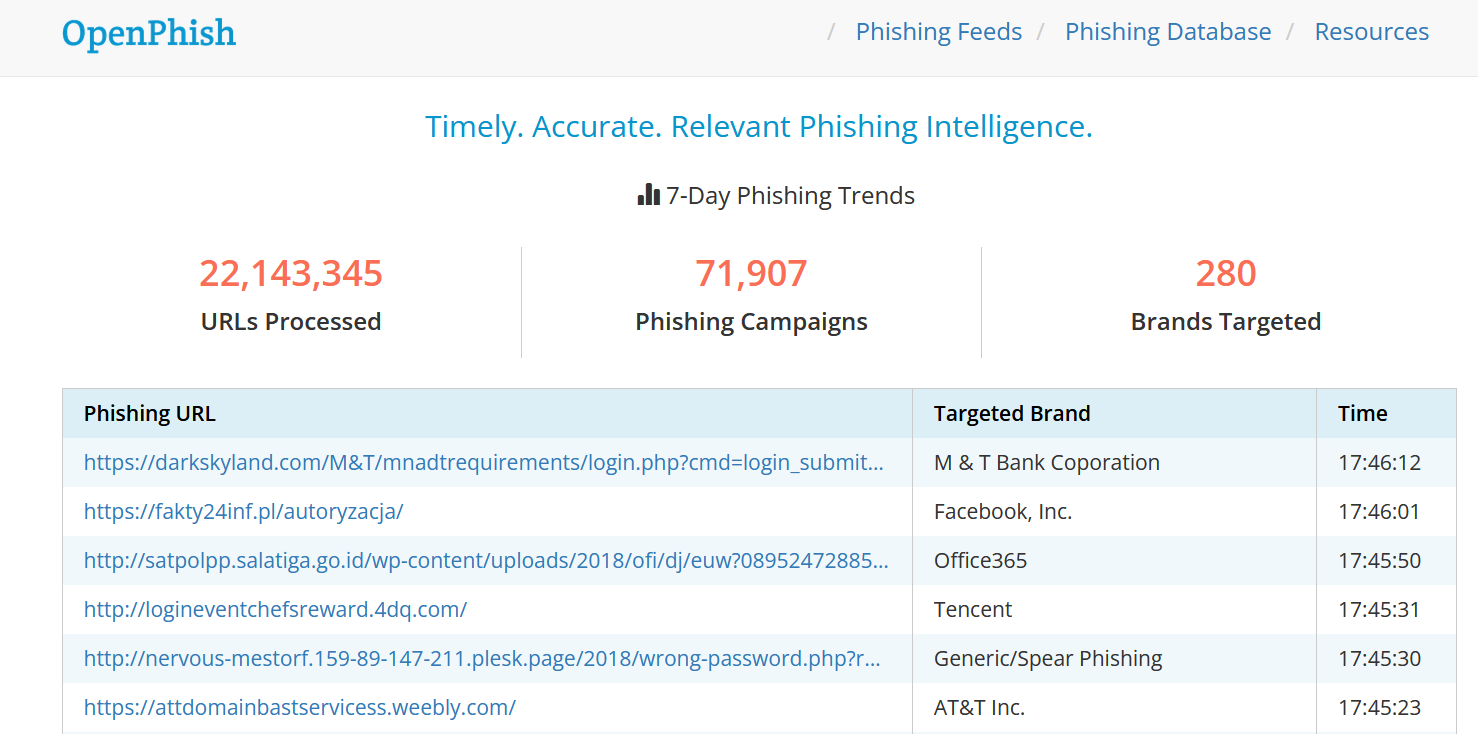
Sharing Phishing Intelligence
From OpenPhish latest phishing URLs
Email Filtering (MTAs)
Commercial services for email filtering SpamHaus
DNS Block Lists
From Understanding DNSBL Filtering
A DNSBL (commonly known as a ‘Blocklist") is a database that is queried in realtime by Internet mail servers for the purpose of obtaining an opinion on the origin of incoming email. The role of a DNSBL such as Spamhaus’ SBL/XBL/PBL Advisory system is to provide an opinion, to anyone who asks, on whether a particular IP Address meets Spamhaus’ own policy for acceptance of inbound email.
Postfix Junk Control
From Features
Spam Filter
The purpose of a spam filter is to reduce the amount of incoming spam, or junk mail, that reaches user’s mailboxes. Spam filters accomplish this by applying spam detection rules–which consider a variety of factors such as the server that sent the message, the message content, and so forth–to incoming mail. If a message’s “spam level” reaches a certain threshold, it is marked and treated as spam.
Spam filters can also be applied to outgoing mail. This can be useful if a user’s mail account is compromised, to reduce the amount of spam that can be sent using your mail server.
SpamAssassin is a popular open source spam filter.
Limits of Email Filtering
If an email account of one of your associates, boss, professor, etc… gets compromised, will email filtering prevent malicious emails from that compromised account?
Social Engineering Additional Materials
Definition
From Framework-Definition
“Any act that influences a person to take an action that may or may not be in their best interest”.
Why Social Engineering?
From Framework-Why
Malicious actors know it could take hours, weeks, or even months to successfully brute force their way into a network to steal credentials. However, with social engineering tactics, those very same credentials can be stolen in just a matter of minutes.
Common Attacks
From Framework-Common attacks all involve impersonation
- Customer Service: Phone and Email
- Delivery Service
- Phone
- Tech Support
The Human Element
- Psychology – how the mind works
- Influence Tactics, Manipulation
- Pretexting, etc…
Fraud
Extra Fraud Materials
Sponsored Content: Last Week Tonight with John Oliver (HBO) Real news or an advertisement, a very deceptive technique. Caution strong language.
Investment Fraud
From Cyber Fraud
Online Investment Newsletters – While legitimate online newsletters may contain valuable information, others are tools for fraud.
Online Bulletin Boards – Online bulletin boards are a way for investors to share information. While some messages may be true, many turn out to be bogus – or even scams.
Investment Spam
Pump and Dump – Generally the end goal of all the above
Fraudulent Investment Newsletters
From Cyber Fraud
Some companies pay online newsletters to “tout” or recommend their stocks. Touting isn’t illegal as long as the newsletters disclose who paid them, how much they’re getting paid, and the form of the payment, usually cash or stock. But fraudsters often lie about the payments they receive and their track records in recommending stocks.
Frauds in Discussion Groups
From Cyber Fraud
Fraudsters may use online discussions to pump up a company or pretend to reveal “inside” information about upcoming announcements, new products, or lucrative contracts.
You may never know for certain who you’re dealing with, or whether they’re credible, because many sites allow users to hide their identity behind multiple aliases. People claiming to be unbiased observers may actually be insiders, large shareholders, or paid promoters. One person can easily create the illusion of widespread interest in a small, thinly traded stock by posting numerous messages under various aliases.
Investment Spam
From Cyber Fraud
With a bulk e-mail program, spammers can send personalized messages to millions of people at once for much less than the cost of cold calling or traditional mail. Many scams, including advance fee frauds, use spam to reach potential victims.
Pump and Dump Schemes 1
From Cyber Fraud
“Pump and dump” schemes have two parts. In the first, promoters try to boost the price of a stock with false or misleading statements about the company. Once the stock price has been pumped up, fraudsters move on to the second part, where they seek to profit by selling their own holdings of the stock, dumping shares into the market.
Pump and Dump Schemes 2
From Cyber Fraud
These schemes often occur on the Internet where it is common to see messages urging readers to buy a stock quickly. Often, the promoters will claim to have “inside” information about a development that will be positive for the stock. After these fraudsters dump their shares and stop hyping the stock, the price typically falls, and investors lose their money.
Online Shopping Fraud
From the text
- Failure to send the merchandise
- Sending something of lesser value than advertised
- Failure to deliver in a timely manner
- Failure to disclose all relevant information about a product or terms of the sale
Auction Fraud
Shill bidding: This occurs when fraudulent sellers (or their “shills”) bid on the seller’s items to drive up the price.
Bid shielding: This occurs when fraudulent buyers submit very high bids to discourage other bidders from competing for the same item. The fake buyers then retract their bids so that people they know can get the item at a lower price.
Bid siphoning: This occurs when con artists lure bidders off legitimate auction sites by offering to sell the “same” item at a lower price. Their intent is to trick consumers into sending money without proffering the item. By going offsite, buyers lose any protections the original site may provide, such as insurance, feedback forms, or guarantees.
Charity/Disaster Fraud 1
From FBI: Charity and Disaster Fraud
Charity fraud schemes seek donations for organizations that do little or no work—instead, the money goes to the fake charity’s creator.
While these scams can happen at any time, they are especially prevalent after high-profile disasters. Criminals often use tragedies to exploit you and others who want to help.
Charity fraud scams can come to you in many forms: emails, social media posts, crowdfunding platforms, cold calls, etc. Always use caution and do your research when you’re looking to donate to charitable causes.
Charity Fraud 2
From FBI: Charity and Disaster Fraud
After a natural disaster or other emergency, unethical contractors and other scammers may commit insurance fraud, re-victimizing people whose homes or businesses have been damaged. Sometimes these fraudsters even pretend to be affiliated with the government, when they are not. If you need any post-disaster repairs, do your research before hiring any contractor.
Identity Theft/Fraud
From DOJ: Identity Theft
Identity theft and identity fraud are terms used to refer to all types of crime in which someone wrongfully obtains and uses another person’s personal data in some way that involves fraud or deception, typically for economic gain.
Why Steal an Identity?
- Run up debts under someone elses name/id
- Commit crimes, such as automobile violations, in someone elses name
- Gain benefits due to someone else
New or Old?
- New or old?
- Cyber enabled or cyber dependent?
Dark Patterns
Dark Patterns Additional Materials
- Opinion: Stopping the Manipulation Machines, Greg Bensinger, April 30, 2021. Very good overview of dark patterns with current examples.
- Dark Patterns at Scale: Findings from a Crawl of 11K Shopping Websites
- Dark Patterns (www.darkpatterns.org)
- Dark Patterns Tip Line, has a good list of seven dark patterns with explanations at Harms
- Cookie monsters: why your browsing history could mean rip-off prices, December 2016.
DarkPatterns: Definition
From DarkPatterns.org
Dark Patterns are tricks used in websites and apps that make you do things that you didn’t mean to, like buying or signing up for something.
DarkPatterns: How
From DarkPatterns.org
When you use websites and apps, you don’t read every word on every page - you skim read and make assumptions. If a company wants to trick you into doing something, they can take advantage of this by making a page look like it is saying one thing when it is in fact saying another.
Harms of Dark Patterns 1
From Dark Pattern Tipline: Harms
- Denied Choice
- Experienced Discrimination
- Felt Shamed
- Felt Tricked
Harms of Dark Patterns 2
From Dark Pattern Tipline: Harms
- Lost Money
- Lost Privacy
- Wasted Time
Types of Dark Patterns 1
- Trick questions
- Sneak into Basket
- Roach Motel
- Privacy Zuckering
- Price Comparison Prevention
Types of Dark Patterns 2
- Misdirection
- Hidden Costs
- Bait and Switch
- Confirm Shaming
Social Engineering