Malware
Dr. Greg Bernstein
March 11th, 2021
Malware
References
Ori Or-Meir, Nir Nissim, Yuval Elovici, and Lior Rokach. 2019. Dynamic Malware Analysis in the Modern Era—A State of the Art Survey. ACM Comput. Surv. 52, 5, Article 88 (October 2019), 48 pages. “Survey”: Read sections 1-4 (pages 1-18) open access
Wenke Lee Georgia Institute of Technology, Malware and Attack Technologies Knowledge Area, Issue 1.0, October 2019 PDF
Wikipedia: Malware, Wikipedia: Computer Virus, Wikipedia: Ransomware
Recent Research
Amir Afianian, Salman Niksefat, Babak Sadeghiyan, and David Baptiste. 2019. Malware Dynamic Analysis Evasion Techniques: A Survey. ACM Comput. Surv. 52, 6, Article 126 (January 2020), 28 pages.
Hamidreza Alimardani and Mohammed Nazeh. 2018. A Taxonomy on Recent Mobile Malware: Features, Analysis Methods, and Detection Techniques. In Proceedings of the 2018 International Conference on E-business and Mobile Commerce (ICEMC ’18). Association for Computing Machinery, New York, NY, USA, 44–49.
Alexei Bulazel and Bülent Yener. 2017. A Survey On Automated Dynamic Malware Analysis Evasion and Counter-Evasion: PC, Mobile, and Web. In Proceedings of the 1st Reversing and Offensive-oriented Trends Symposium (ROOTS). Association for Computing Machinery, New York, NY, USA, Article 2, 1–21.
Definition: Malware
From Wikipedia: Malware
Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network (by contrast, software that causes unintentional harm due to some deficiency is typically described as a software bug).
Enhanced Malware Definition
From Survey
Malware is code running on a computerized system whose presence or behavior the system administrators are unaware of; were the system administrators aware of the code and its behavior, they would not permit it to run.
Malware compromises the confidentiality, integrity or the availability of the system by exploiting existing vulnerabilities in a system or by creating new ones.
Common Malware Types 1
These are common designations of malware with links to Wikipedia:
Common Malware Types 2
Application Types
- Spyware
- Ransomware
- Wiper
- Adware advertising
- Scareware social engineering attack vector
Viruses, Worms, and Trojans
Definition: Computer Virus
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be “infected” with a computer virus. Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage.
Definition: Computer Worm
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behavior will continue.
Virus Parts
From Wikipedia: Computer Virus
Infection mechanism (also called ‘infection vector’): This is how the virus spreads or propagates. A virus typically has a search routine, which locates new files or new disks for infection.
Trigger: Also known as a logic bomb, this determines the event or condition for the malicious “payload” to be activated or delivered
Payload : The “payload” is the actual body or data which carries out the malicious purpose of the virus.
Virus Phases 1
From Wikipedia: Computer Virus
Dormant phase: The virus program is idle during this stage. The virus program has managed to access the target user’s computer or software, but during this stage, the virus does not take any action.
Propagation phase: The virus starts propagating, which is multiplying and replicating itself. The virus places a copy of itself into other programs or into certain system areas on the disk. The copy may not be identical to the propagating version; viruses often “morph” or change to evade detection by IT professionals and anti-virus software.
Virus Phases 2
From Wikipedia: Computer Virus
Triggering phase: A dormant virus moves into this phase when it is activated, and will now perform the function for which it was intended.
Execution phase: This is the actual work of the virus, where the “payload” will be released.
Virus Infection Targets
From Wikipedia: Computer Virus
- binary executables: such as .EXE or .COM files, DLL, shared libraries
- data files: such as Microsoft Word documents or PDF files
- boot sector: of the host’s hard drives
Definition: Trojan Horse
From Trojan horse
In computing, a Trojan horse is any malware which misleads users of its true intent. Trojans are generally spread by some form of social engineering, for example where a user is duped into executing an email attachment disguised to appear not suspicious, or by clicking on some fake advertisement on social media or anywhere else. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller which can then have unauthorized access to the affected computer.
Trojan Horse Properties
From Trojan horse
Trojans may allow an attacker to access users’ personal information such as banking information, passwords, or personal identity. It can also delete a user’s files or infect other devices connected to the network. Ransomwares attacks are often carried out using a trojan.
Unlike computer viruses, worms, and rogue security software, trojanss generally do not attempt to inject themselves into other files or otherwise propagate themselves.
Trojan Variant: Dropper
From Wikipedia: Dropper
A dropper is a kind of Trojan that has been designed to “install” some sort of malware (virus, backdoor, etc.) to a target system. The malware code can be contained within the dropper (single-stage) in such a way as to avoid detection by virus scanners or the dropper may download the malware to the target machine once activated (two stage).
See also Malware spotlight: Droppers
Backdoors
Definition: Backdoor
From Wikipedia: Backdoors
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), etc. Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information.
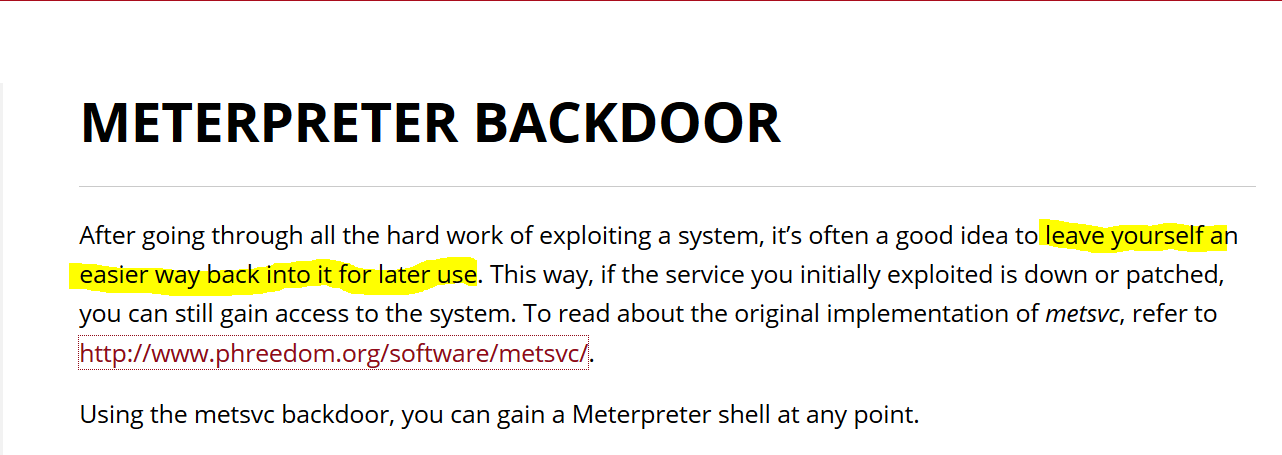
Example: Metasploit Backdoor
From Meterpreter backdoor
Example: Cobaltstrike Beacon
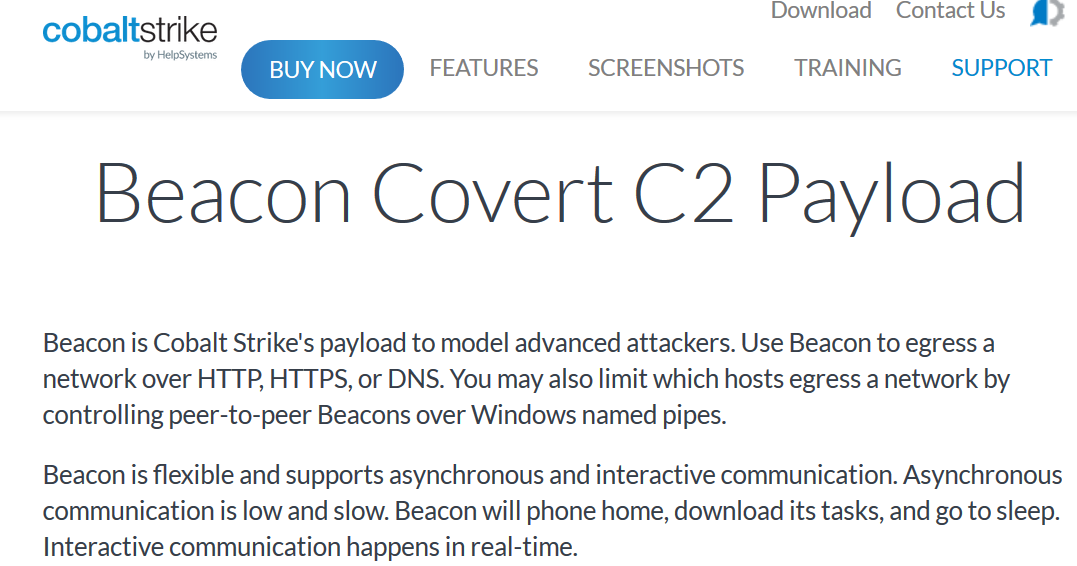
Remote Access Trojans
From Wikipedia: Remote Desktop Software –RAT
A remote access trojan (RAT, sometimes called creepware) is a type of malware that controls a system through a remote network connection. While desktop sharing and remote administration have many legal uses, “RAT” connotes criminal or malicious activity.
See also Remote Access Trojans Explained plus 11 Best RAT Software, Scanners, & Detection Tools
Example RAT: DarkComet
From Wikipedia:DarkComet
Spy Functions: Webcam Capture, Sound Capture, Remote Desktop, Keylogger
Network Functions: Active Ports, Network Shares, Server Socks5, LAN Computers, Net Gateway, IP Scanner, Url Download, Browse Page, Redirect IP/Port, WiFi Access Points
Computer Power: Poweroff, Shutdown, Restart, Logoff
Server Actions: Lock Computer, Restart Server, Close Server, Uninstall Server, Upload and Execute, Remote Edit Service
PoetRAT
PoetRAT: Malware targeting public and private sector in Azerbaijan evolves, October 2020, “leverages malicious Microsoft Word documents alleged to be from the Azerbaijan government”

CRAT
CRAT wants to plunder your endpoints, November 2020, “The RAT consists of multiple obfuscation techniques to hide strings, API names, command and control (C2) URLs and instrumental functions, along with static detection evasion. The attack also employs a multitude of anti-infection checks to evade sandbox based detection systems.”

Oblique RAT
ObliqueRAT returns with new campaign using hijacked websites, March 2021, “utilizes malicious Microsoft Office documents (maldocs) to spread the remote access trojan (RAT) ObliqueRAT”

Other Malware
Definition: Spyware
From Spyware
Spyware describes software with malicious behavior that aims to gather information about a person or organization and send such information to another entity in a way that harms the user; for example by violating their privacy or endangering their device’s security. This behavior may be present in malware as well as in legitimate software. Websites may engage in spyware behaviors like web tracking. Hardware devices may also be affected
Spyware Example: Masslogger
TALOS: Masslogger, February, 2021, “designed to retrieve and exfiltrate user credentials from multiple sources such as Microsoft Outlook, Google Chrome and instant messengers”

Definition: Rootkit
From Wikipedia: Rootkit
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software. The term rootkit is a compound of “root” (the traditional name of the privileged account on Unix-like operating systems) and the word “kit” (which refers to the software components that implement the tool). The term “rootkit” has negative connotations through its association with malware.
Definition: Adware
From Wikipedia: Adware
Adware is software that generates revenue for its developer by automatically generating online advertisements in the user interface of the software or on a screen presented to the user during the installation process. The software may generate two types of revenue: one is for the display of the advertisement and another on a “pay-per-click” basis, if the user clicks on the advertisement. Some advertisements also act as spyware, collecting and reporting data about the user, to be sold or used for targeted advertising or user profiling.
Definition: Ransomware
Ransomware is a type of malware from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. It encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them. Recovering the files without the decryption key is an intractable problem – and difficult to trace digital currencies such as paysafecard or Bitcoin and other cryptocurrencies are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
See also Cryptovirology
Ransomware Updates
Ransomware Statistics, Trends and Facts for 2020 and BeyondUpdated November 2020
Ransomware 2020: Attack Trends Affecting Organizations Worldwide Updated October 2020
Ransomware Facts, Trends & Statistics for 2021 February 2021
Definition: Scareware
From Wikipedia: Scareware
Scareware is a form of malware which uses social engineering to cause shock, anxiety, or the perception of a threat in order to manipulate users into buying unwanted software. Scareware is part of a class of malicious software that includes rogue security software, ransomware and other scam software that tricks users into believing their computer is infected with a virus, then suggests that they download and pay for software to remove it. Usually the virus isn’t real and the software is non-functional or malware itself.
Definition: Cryptominer
From Survey
Cryptominers use any available computing power of the victim to mine cryptocurrencies for the attacker. The victims bear the brunt of the increased electricity costs and performance deterioration, while the attacker makes all the profit. This is a fairly new attack that has been on the rise since 2017; reportedly, almost 90% of recent malware attacks are cryptominers. This trend is explained by the fact that mining cryptocurrencies yields great profits to attackers while requiring minimal effort.
Cryptominer Example
Lemon Duck brings cryptocurrency miners back into the spotlight, October 2020, “has a cryptocurrency mining payload that steals computer resources to mine the Monero virtual currency. The actor employs various methods to spread across the network, like sending infected RTF files using email, psexec, WMI and SMB exploits”

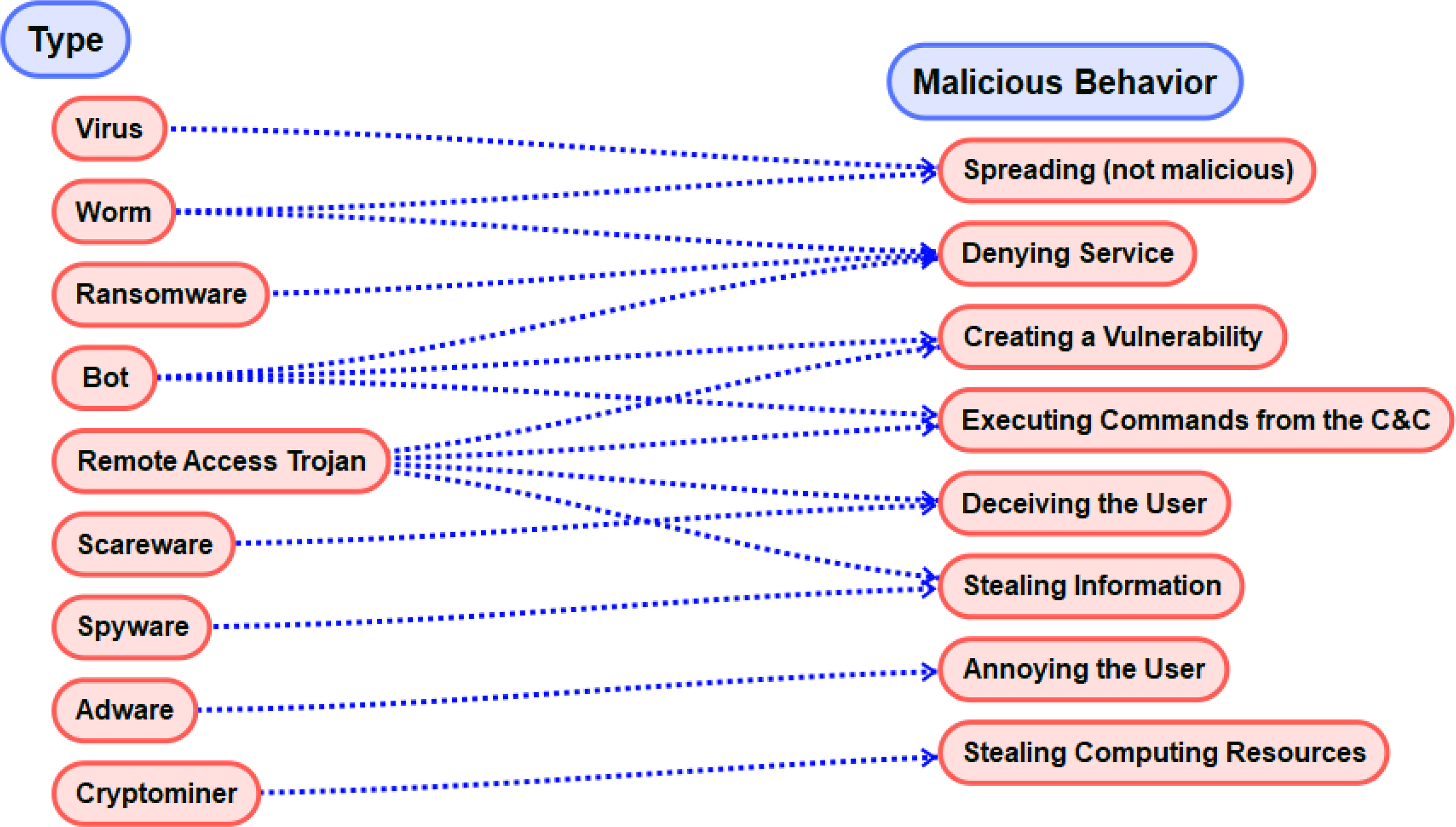
Categorization by Malicious Behavior
Another View
Since there seem to be so many “types” of malware with new varieties emerging relatively frequently we need alternative ways to look at the problem. This way we can come up with more general methods for detection, prevention and removal.
Stealing Information
From Survey
The most common malicious activity is information theft, whether it’s banking information, classified information, passwords, or access credentials. Such information can be used to access other systems or accounts, steal money or other goods, or damage a company financially, and when it comes to hospitals and governmental agencies, it can even risk lives. In terms of the CIA triad, information theft compromises the confidentiality of data and is mostly associated with RATs and spyware.
Types of Malware Information Theft 1
From Survey
Stealing Credentials: Passwords, as well as other credential types, such as biometric information and authentication certificates.
Keylogging: keylogger malware records every keystroke entered by the user and sends it to its C&C. Keyloggers are primarily used to extract passwords and other types of sensitive information.
Types of Malware Information Theft 2
From Survey
Spying: Spyware collects information about the infected host, users, or the organization. Such information may include proprietary information, data about clients, or personal documents.
Sniffing attack: Sniffer malware steal information as it travels from one machine to another. This is usually done by monitoring the network traffic and extracting data from it.
Creating a Vulnerability
From Survey
Infecting a host with malware is done by exploiting a vulnerability. However, malware sometimes create new vulnerabilities by removing anti-viruses, installing backdoors, changing passwords, changing firewall settings, adding a new privileged user, downgrading software to an older version, and more. These new vulnerabilities can later be used by the attacker to gain access to the victim, even if the original malware was detected and removed. This behavior compromises the integrity of the system and associated with RATs and bots.
Denying service
From Survey
DDoS attacks: DDoS attacks use botnets to generate simultaneous requests from all over the globe.
Access denial attacks: Worms can spread and cause a denial-of-service attack against the network’s infrastructure. Ransomware encrypts files causing a DoS attack against the user’s file system.
Damaging the hardware: Although not common, it is real. Since electronic circuits often contain firmware, it is possible to overwrite it with garbage code and render the device unusable. Such an attack against the BIOS was demonstrated by Win9x.CIH, which prevents the computer from booting after overwriting the BIOS with buggy firmware code.
Executing Commands from a C&C server
From Survey
Executing commands from a command and control (C&C) server: Sometimes malware authors wish to have full control over the infected endpoint. For that purpose, they incorporate a command execution mechanism in the malware that executes commands it receives from the C&C. This behavior compromises the integrity of the system and is mostly associated with bots and RATs.
Deceiving the user
From Survey
Malicious parties can use deception to gain access to restricted subsystems and/or manipulate data for their benefit. This type of behavior is common among financial malware performing phishing attacks to gain access to banking accounts. This behavior compromises the integrity and confidentiality of the system and associated with RATs and scareware. Common deception behaviors include the following: disguising as a benign software, phishing attacks, pretending to be a legitimate user, scaring the user, and man in- the-middle (MITM) attacks.
Annoying the user
From Survey
Malware might annoy the user by showing ads to the user (adware), changing the user’s homepage or default search engine, or defacing Web pages. This type of malware behavior might not be malicious per se, but it still falls within the definition in that it is unwanted by the user, and if the system administrators knew about its existence, they would not allow it to execute. Although this behavior does not compromise any component of the CIA triad it is unwanted by the user and disturbs normal workflow.
Stealing computing resources
From Survey
Cryptominers leverage their victims’ computer resources, causing the infected machines to run abnormally slow, for the sole purpose of generating revenue by selling the mined cryptocurrency. For the most part, cryptominers allow the system to run as normal and don’t interact with the system’s information, apart from performing the computations required to mine cryptocurrencies.
Summary of Types and Malicious Behavior
From Survey
More Malware Behaviors
Behavior Taxonomy
From Survey
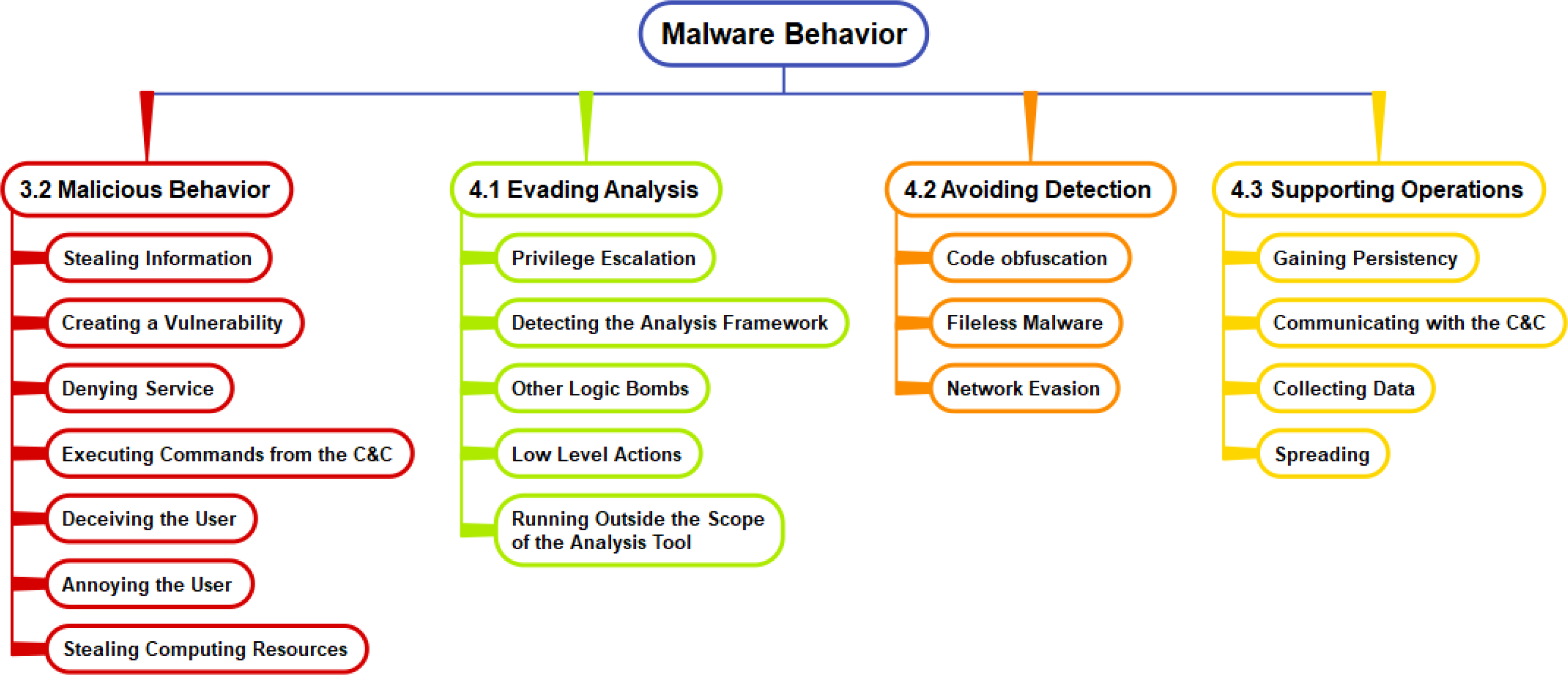
Evasion and Avoidance
We will look into the behaviors associated with analysis evasion and detection avoidance in a separate slide set that discusses detection. Now we will look at some key supporting operations.
Supporting Operations
From Survey
Gaining Persistency
Communicating with the C&C
Collecting data
Spreading
Gaining Persistency
From Survey
Malware needs to find a way to load itself after each reboot. The Windows registry can be used for this purpose, but other techniques are also used, including: shortcut modifications, DLL search order hijacking, subverting the boot process and loading a malicious kernel (such malware is called a bootkit), hardware infection, and others. One method malware use to gain persistency is by adding itself to an Auto-Start Extendibility Point (ASEP), such as the registry startup key inWindows. For example, adding a malicious command to the Run or RunOnce registry keys will cause the computer to execute that command when the system has finished the booting process.
Communicating with the C&C
From Survey
Communication with the C&C includes getting commands from a handler, receiving updates, and sending extracted data. Malware communication is usually covert, enabling malware to bypass detection tools and firewalls.
Collecting data
From Survey
Malware collect data from various sources, including: volatile memory (e.g., passwords, credentials, and cryptographic keys), the file system (e.g., documents), the operating system (e.g., registry values, active processes, system configuration, open windows), user activities (e.g., websites visited, open documents, keystrokes), and the network (e.g., connected printers, open ports on other hosts).
Spreading
From Survey
Spreading methods include sending infecting emails (via attachments or malicious scripts); exploiting vulnerabilities to allow remote execution; file sharing (e.g., P2P file sharing, torrent clients, shared folders); and the use of Bluetooth, USB, and other portable devices.