Malware Detection
Dr. Greg Bernstein
March 16th, 2021
Malware Detection
References
STIX version 1 Whitepaper Provides a good overview, STIX 1 was XML STIX 2.x is JSON based. How STIX, TAXII and CybOX Can Help With Standardizing Threat Information Note: CybOX was integrated into STIX 2.
Indicators of Compromise (IOC) 1
Wikipedia: Indicator of Compromise
Indicator of compromise (IoC) in computer forensics is an artifact observed on a network or in an operating system that, with high confidence, indicates a computer intrusion.
Indicators of Compromise (IOC) 2
Wikipedia: Indicator of Compromise
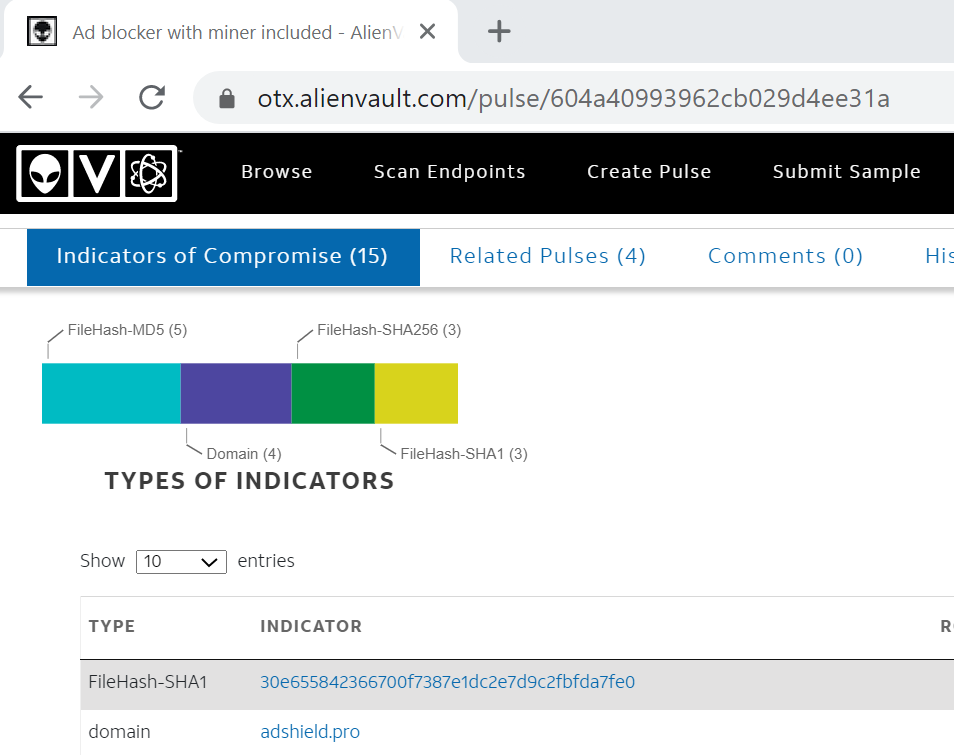
IOC Example 1
From AlienVault: Ad blocker with miner included, IOCs – File Hashes and domains
Cyber Observable Objects 1
Summarized from STIX Version 2.1
6.1 Artifact Object: permits capturing an array of bytes (8-bits), as a base64-encoded string, or linking to a file-like payload.
6.2 Autonomous System (AS) Object
6.3 Directory Object
6.4 Domain Name Object
6.5 Email Address Object
Cyber Observable Objects 2
Summarized from STIX Version 2.1
- 6.6 Email Message Object
- 6.7 File Object
- 6.8 IPv4 Address
- 6.9 IPv6 Address Object
- 6.10 MAC Address Object
Cyber Observable Objects 3
Summarized from STIX Version 2.1
6.11 Mutex Object
6.12 Network Traffic Object: represents arbitrary network traffic that originates from a source and is addressed to a destination. The network traffic MAY or MAY NOT constitute a valid unicast, multicast, or broadcast network connection. This MAY also include traffic that is not established, such as a SYN flood.
6.13 Process Object
6.14 Software Object
Cyber Observable Objects 4
Summarized from STIX Version 2.1
- 6.15 URL Object
- 6.16 User Account Object
- 6.17 Windows™ Registry Key Object
- 6.18 X.509 Certificate Object
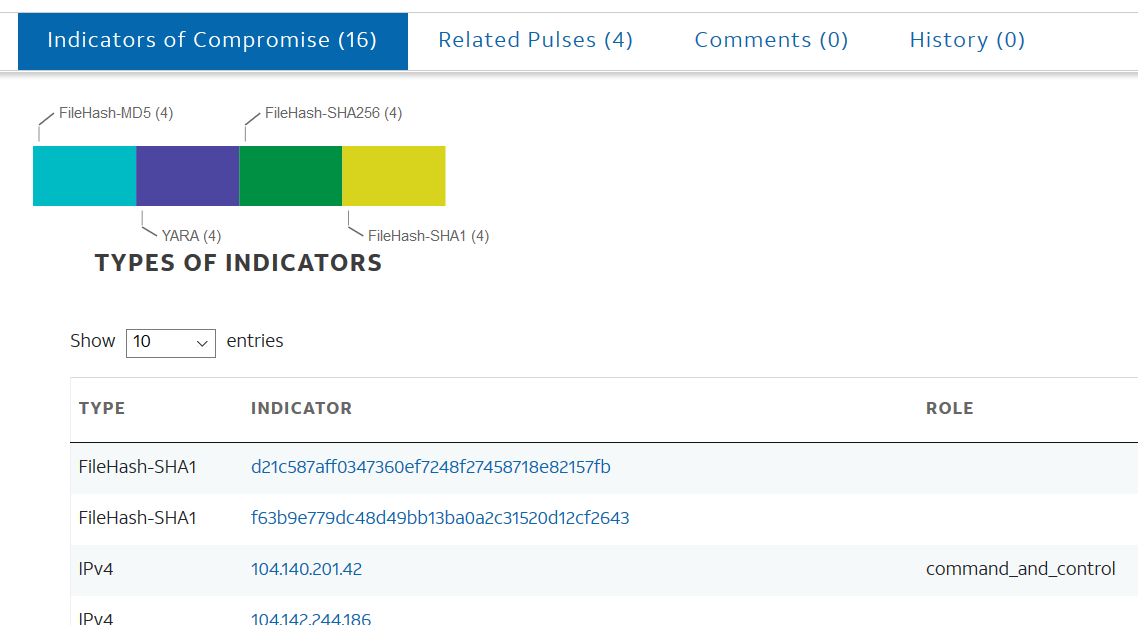
IOC Example 2
From AlienVault: All That for a Coinminer?, IOCs – File Hashes, IP, and YARA rules
Cyber Threat Intelligence (CTI)
From What is Cyber Threat Intelligence?
(Cyber) Threat intelligence is data that is collected, processed, and analyzed to understand a threat actor’s motives, targets, and attack behaviors. Threat intelligence enables us to make faster, more informed, data-backed security decisions and change their behavior from reactive to proactive in the fight against threat actors.
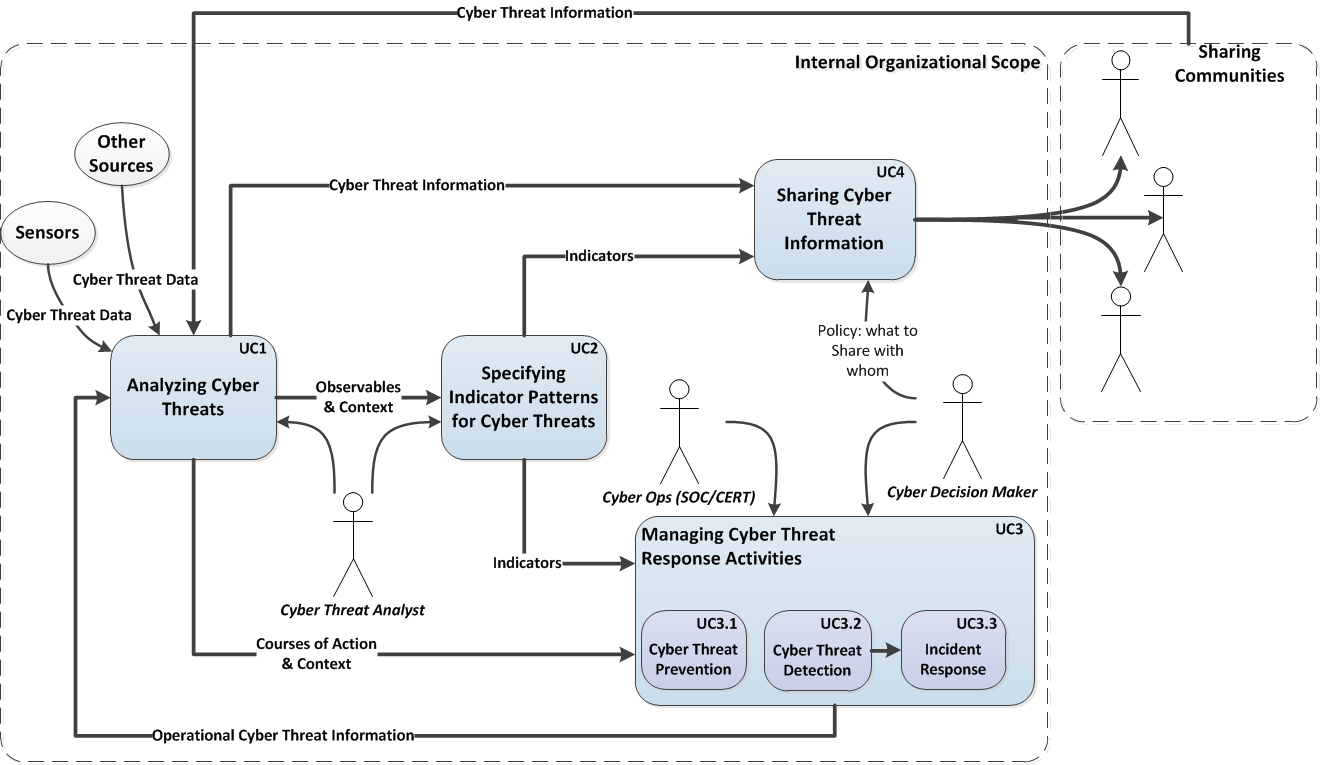
Uses for Cyber Threat Information
From STIX version 1 Whitepaper
Standardizing CTI: STIX
From Cyber Threat Intelligence
Structured Threat Information Expression (STIX™) is a language and serialization format used to exchange cyber threat intelligence (CTI).
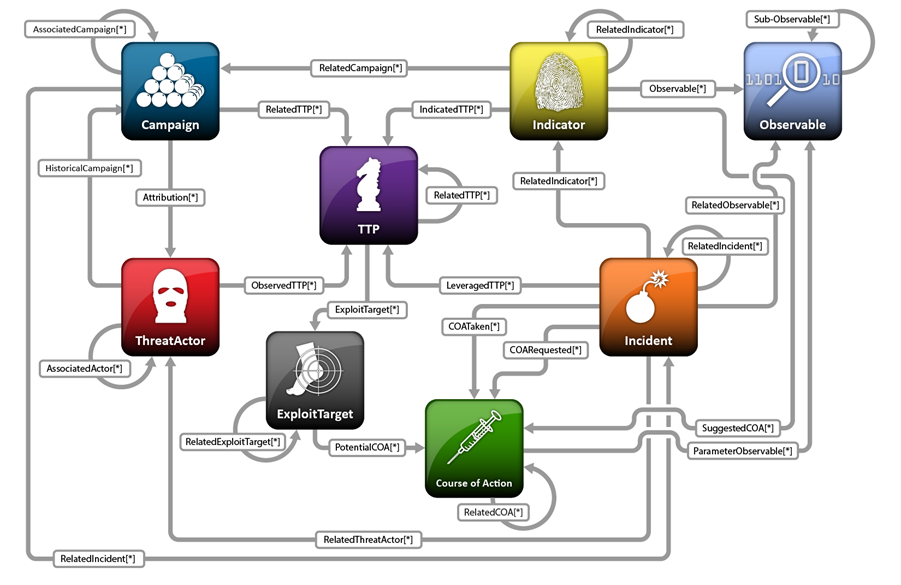
STIX Architecture
From the STIX 1.0 white paper
TAXII
Trusted Automated Exchange of Intelligence Information (TAXII™) is an application layer protocol for the communication of cyber threat information in a simple and scalable manner.
TAXII is a protocol used to exchange cyber threat intelligence (CTI) over HTTPS. TAXII enables organizations to share CTI by defining an API that aligns with common sharing models.
Example STIX Indicators
From AlienVault: Ad blocker with miner included, IOCs – File Hashes and domains
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--9b3c4ff1-726d-4657-92b5-a7a2a3d147ff",
"created": "2021-03-11T16:08:58.000Z",
"modified": "2021-03-11T16:08:58.000Z",
"name": "stack_string",
"description": "SHA1 of 9e989ef2a8d4bc5ba1421143aad59a47\nSHA1 of 9e989ef2a8d4bc5ba1421143aad59a47",
"pattern": "[file:hashes.'SHA-1' = '30e655842366700f7387e1dc2e7d9c2fbfda7fe0']",
"pattern_type": "stix",
"pattern_version": "2.1",
"valid_from": "2021-03-11T16:08:58Z",
"labels": [
"malicious-activity"
]
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--285e6318-8fe3-422d-822c-bd5d11a93182",
"created": "2021-03-11T16:08:58.000Z",
"modified": "2021-03-11T16:08:58.000Z",
"name": "",
"description": "",
"pattern": "[domain_name:value = 'adshield.pro']",
"pattern_type": "stix",
"pattern_version": "2.1",
"valid_from": "2021-03-11T16:08:58Z",
"labels": [
"malicious-activity"
]
},Anti-Virus Software
Definition: Anti-Virus Software
From Wikipedia: Antivirus Software
Antivirus software, or anti-virus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware.
Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other kinds of malware, antivirus software started to provide protection from other computer threats.
Signature Based Virus Detection
From Wikipedia:Signature Based Virus Detection
Traditional antivirus software relies heavily upon signatures to identify malware.
When malware arrives in the hands of an antivirus firm, it is analysed by malware researchers or by dynamic analysis systems. Then, once it is determined to be a malware, a proper signature of the file is extracted and added to the signatures database of the antivirus software.
Open Source AV
“ClamAV® is an open source antivirus engine for detecting trojans, viruses, malware & other malicious threats.”
ClamAV Features 1
From ClamAV Features
- Command-line scanner
- Milter interface for sendmail
- Advanced database updater with support for scripted updates and digital signatures
- Virus database updated multiple times per day
- Built-in support for all standard mail file formats
ClamAV Features 2
From ClamAV Features
- Built-in support for various archive formats, including Zip, RAR, Dmg, Tar, Gzip, Bzip2, OLE2, Cabinet, CHM, BinHex, SIS and others
- Built-in support for ELF executables and Portable Executable files packed with UPX, FSG, Petite, NsPack, wwpack32, MEW, Upack and obfuscated with SUE, Y0da Cryptor and others
- Built-in support for popular document formats including MS Office and MacOffice files, HTML, Flash, RTF and PDF
Example Scan
greg@greg-desktop:~/Downloads$ sudo clamscan -v .
Scanning /home/greg/Downloads/eicar.com
/home/greg/Downloads/eicar.com: Win.Test.EICAR_HDB-1 FOUND
Scanning /home/greg/Downloads/gpg
/home/greg/Downloads/gpg: OK
Scanning /home/greg/Downloads/en_windows_7_professional_with_sp1_vl_build_x64_dvd_u_677791.iso
/home/greg/Downloads/en_windows_7_professional_with_sp1_vl_build_x64_dvd_u_677791.iso: OK
Scanning /home/greg/Downloads/digikam.pdf
/home/greg/Downloads/digikam.pdf: OK
Scanning /home/greg/Downloads/ubuntu-20.04-desktop-amd64.iso
/home/greg/Downloads/ubuntu-20.04-desktop-amd64.iso: OK
Scanning /home/greg/Downloads/kali-linux-2020.4-vbox-amd64.ova
/home/greg/Downloads/kali-linux-2020.4-vbox-amd64.ova: OK
Scanning /home/greg/Downloads/rsync.deb
/home/greg/Downloads/rsync.deb: OK
Scanning /home/greg/Downloads/digikam-5.3.0-01-x86-64.appimage
/home/greg/Downloads/digikam-5.3.0-01-x86-64.appimage: OK
Scanning /home/greg/Downloads/mimikatz_trunk.zip
/home/greg/Downloads/mimikatz_trunk.zip: Win.Trojan.Mimikatz-6466236-0 FOUND
----------- SCAN SUMMARY -----------
Known viruses: 8508298
Engine version: 0.102.4
Scanned directories: 1
Scanned files: 13
Infected files: 2
Data scanned: 40.23 MB
Data read: 9524.38 MB (ratio 0.00:1)
Time: 21.028 sec (0 m 21 s)Virus Signatures
Proprietary AV signature formats
Clam AV multiple types of signatures: Body-based Signature Content Format, Bytecode Signatures, Signatures based on container metadata, Extended signature format, File hash signatures, Logical signatures, PhishSigs
YARA rules: open source “The pattern matching swiss knife for malware researchers”
YARA
From YARA’s Documentation
YARA is a tool aimed at (but not limited to) helping malware researchers to identify and classify malware samples. With YARA you can create descriptions of malware families (or whatever you want to describe) based on textual or binary patterns.
YARA Links
Signature-Based Detection With YARA June 2015
Hunting with YARA rules and ClamAV February 2017
Awesome YARA GitHub “A curated list of awesome YARA rules, tools, and resources”
YARA Example 1 PE file
// Detect a Portable Executable file
rule is_PE_File
{
strings:
$a = "MZ"
condition:
$a and uint16(0) == 0x5A4D and uint32(uint32(0x3C)) == 0x00004550
}Portable Executable Files
From Wikipedia: Portable Executable
The Portable Executable (PE) format is a file format for executables, object code, DLLs and others used in 32-bit and 64-bit versions of Windows operating systems. The PE format is a data structure that encapsulates the information necessary for the Windows OS loader to manage the wrapped executable code. This includes dynamic library references for linking, API export and import tables, resource management data and thread-local storage (TLS) data. On NT operating systems, the PE format is used for EXE, DLL, SYS (device driver), MUI and other file types.
PE File Layout
From Wikipedia: Portable Executable

YARA Example 2 Mimikatz
// Obtained from https://otx.alienvault.com/indicator/yara/0af19e8f657b5cad062d9ab247b6fe32f93fc2ff
//
import "pe"
rule mimikatz_1014 {
meta:
description = "exe - file mimikatz.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2021-01-18"
hash1 = "99d8d56435e780352a8362dd5cb3857949c6ff5585e81b287527cd6e52a092c1"
strings:
$x1 = "ERROR kuhl_m_lsadump_getUsersAndSamKey ; kull_m_registry_RegOpenKeyEx SAM Accounts (0x%08x)" fullword wide
$x2 = "ERROR kuhl_m_lsadump_getUsersAndSamKey ; kull_m_registry_RegOpenKeyEx user (%s)" fullword wide
$x3 = "ERROR kuhl_m_lsadump_lsa ; kull_m_process_getVeryBasicModuleInformationsForName (0x%08x)" fullword wide
$x4 = "ERROR kuhl_m_lsadump_getComputerAndSyskey ; kull_m_registry_RegOpenKeyEx LSA KO" fullword wide
$x5 = "ERROR kuhl_m_lsadump_dcsync ; kull_m_rpc_drsr_ProcessGetNCChangesReply" fullword wide
$x6 = "ERROR kuhl_m_lsadump_trust ; kull_m_process_getVeryBasicModuleInformationsForName (0x%08x)" fullword wide
$x7 = "ERROR kuhl_m_lsadump_getUsersAndSamKey ; kuhl_m_lsadump_getSamKey KO" fullword wide
$x8 = "ERROR kuhl_m_lsadump_lsa_getHandle ; OpenProcess (0x%08x)" fullword wide
$x9 = "ERROR kuhl_m_lsadump_netsync ; I_NetServerTrustPasswordsGet (0x%08x)" fullword wide
$x10 = "ERROR kuhl_m_dpapi_chrome ; Input 'Login Data' file needed (/in:\"%%localappdata%%\\Google\\Chrome\\User Data\\Default\\Login Da" wide
$x11 = "ERROR kuhl_m_kernel_processProtect ; Argument /process:program.exe or /pid:processid needed" fullword wide
$x12 = "ERROR kuhl_m_lsadump_getHash ; Unknow SAM_HASH revision (%hu)" fullword wide
$x13 = "ERROR kuhl_m_lsadump_sam ; kull_m_registry_RegOpenKeyEx (SAM) (0x%08x)" fullword wide
$x14 = "ERROR kull_m_rpc_drsr_ProcessGetNCChangesReply_decrypt ; Checksums don't match (C:0x%08x - R:0x%08x)" fullword wide
$x15 = "ERROR kuhl_m_lsadump_enumdomains_users ; /user or /rid is needed" fullword wide
$x16 = "ERROR kuhl_m_lsadump_changentlm ; Argument /oldpassword: or /oldntlm: is needed" fullword wide
$x17 = "livessp.dll" fullword wide /* reversed goodware string 'lld.pssevil' */
$x18 = "ERROR kuhl_m_lsadump_enumdomains_users ; SamLookupNamesInDomain: %08x" fullword wide
$x19 = "ERROR kuhl_m_lsadump_getComputerAndSyskey ; kuhl_m_lsadump_getSyskey KO" fullword wide
$x20 = "ERROR kuhl_m_lsadump_getKeyFromGUID ; kuhl_m_lsadump_LsaRetrievePrivateData: 0x%08x" fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 3000KB and
( pe.imphash() == "a0444dc502edb626311492eb9abac8ec" or 1 of ($x*) )
}Testing AV Software 1
AMTSO is the Anti-Malware Testing Standards Organization "We create objective standards and best practices for testing of anti-malware and related products.
AV-Test “The AV-TEST GmbH is the independent research institute for IT security from Germany.”, “… the AV-TEST Institute regularly makes its latest tests and current research findings available to the public free of charge on its website.”
Principle 1: (AV) Testing must not endanger the public
From AMTSO: The Fundamental Principles of Testing
The public has the right to expect that the development and sale of anti‐malware products, the review of such products and publication of those reviews are all done, fundamentally, to protect them. Thus, the foremost principle of testing anti‐malware products is that neither the products nor the related testing should endanger the public.
Principle 1: (AV) Testing must not endanger the public (cont)
From AMTSO: The Fundamental Principles of Testing