CS671
Cybersecurity Overview
Dr. Greg Bernstein
January 12th, 2022
Costs of Cybercrime
In the News

Recent Recommended Articles
- Leaders section of the print edition under the headline “Broadbandits”: To stop the ransomware pandemic, start with the basics, The Economist, Jun 19, 2021.
- Briefing section: Ransomware highlights the challenges and subtleties of cybersecurity, The Economist, Jun 19, 2021.
Selected Quotes 1
A cloud of secrecy and shame surrounding cyber-attacks amplifies the difficulties. Firms cover them up. The normal incentives for them and their counterparties to mitigate risks do not work well. Many firms neglect the basics, such as two-step authentication. Colonial had not taken even simple precautions.
Selected Quotes 2
The cyber-security industry has plenty of sharks who bamboozle clients. Much of what is sold is little better than “medieval magic amulets”, in the words of one cyber-official.
Selected Major State and Criminal Attacks

Costs of Cybercrime 1
From Center for Strategic and International Studies: Costs of Cybercrime
The Center for Strategic and International Studies (CSIS), in partnership with McAfee, presents The Hidden Costs of Cybercrime. As the global losses from cybercrime approach $1 trillion, this report focuses on the costs of cybercrime that organizations may be less aware of, such as opportunity costs, downtime and damaged staff morale.
Costs of Cybercrime 2
From Center for Strategic and International Studies: Costs of Cybercrime
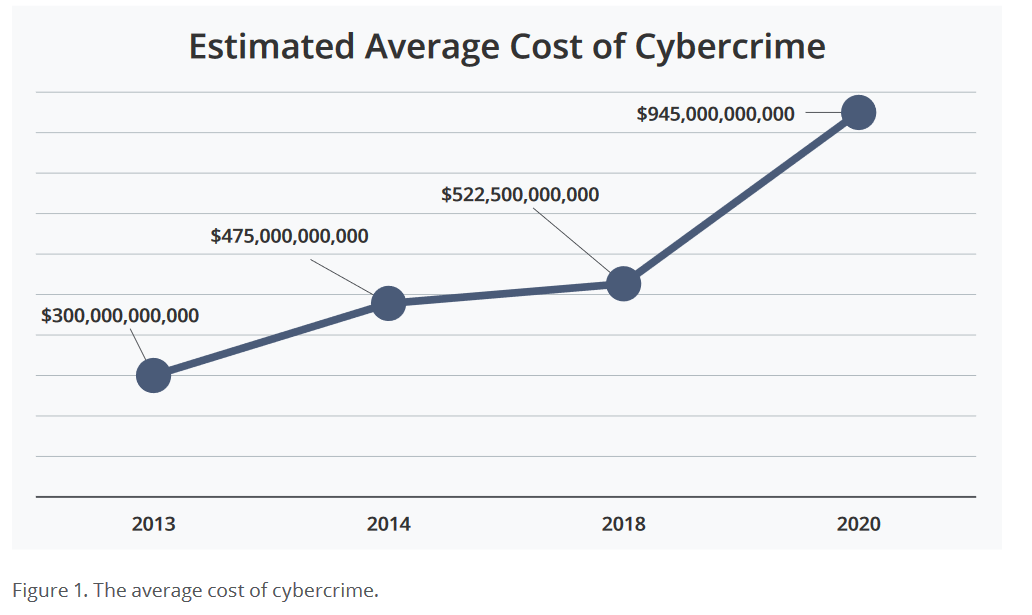
Costs Other Than Cash 1
From Center for Strategic and International Studies: Costs of Cybercrime
- Opportunity costs
- System downtime
- Reduced efficiency
- Brand damage and loss of trust
- IP theft
Costs Other Than Cash 2
From Center for Strategic and International Studies: Costs of Cybercrime
- Incident response costs
- Outside assistance
- Cyber risk insurance
- Damage to employee morale
Most Costly 1
From Center for Strategic and International Studies: Costs of Cybercrime
- Malware and spyware
- Data breaches
- Phishing
- Ransomware
Most Costly 2
From Center for Strategic and International Studies: Costs of Cybercrime
- Financial cybercrime
- Business email compromise
- Cryptocurrency theft
- The use of emerging technical and synthetic media for cybercrime
Questions to Answer 1
- What is Cybercrime? What is actually a criminal act?
- Who is responsible for cybercrime?
- Who do they target? Specific individuals, organizations or “target of opportunity”
Questions to Answer 2
- Why do they do it? (Motivation)
- What are the most common cybercrimes?
- How do they do it? (Major focus of this class)
- How can we stop them? (Major focus of this class)
Course Overview
Issues
- Cybersecurity is a huge topic
- This course has essentially no prerequisites in particular networking
- The field is moving quickly and has many specialties
Approach
- Understand real current cybercrime via case studies
- Learn general principles and concepts
- Learn current industry standard approaches to cybersecurity
- See how these are applied in current situations and environments
Case Studies
We need to be familiar with a reasonable sample of famous and/or recent attacks
- We’ll start with the very well produced and entertaining Darknet Diaries podcast
- Approximately one podcast per week will be assigned for you to listen to
- We will have an interactive Question and Answer session at the beginning of the next class
- The results of these session apply to your class participation grade
Current Case Study List
Why You Need to Learn About Cybersecurity
- Technology developer/manager
- Operator (IT department)
- Defender or Attacker
Course Content
Recommended Topics
Publicly available cybersecurity topic recommendations
- National Cybersecurity Training & Education (NCyTE) Center
- NCyTE Center Knowledge Units – If these don’t show up, click the “Academia” link (not the Employment)
- National Initiative for Cybersecurity Education (NICE)
- SP 800-181 Rev. 1 Workforce Framework for Cybersecurity (NICE Framework)
NCyTE Knowledge Units
From NCyTE Center Knowledge Units
Foundational KU: Basic Cryptography, Cyber Threats, Cybersecurity Foundations, Cybersecurity Principles, Independent/Directed Study/Research, IT Systems Components
Technical Core KU: Basic Cryptography, Basic Networking, Basic Scripting and Programming, Network Defense, Operating Systems Concepts
Non-Technical Core KU: Cyber Threats, Cybersecurity Planning and Management; Policy, Legal, Ethics, and Compliance; Security Program Management, Security Risk Analysis
NCyTE Optional Knowledge Units
Advanced Algorithms, Advanced Cryptography, Advanced Network Technology and Protocols, Algorithms, Analog Telecommunications, Basic Cyber Operations, Cloud Computing, Cyber Crime, Cybersecurity Ethics, Data Administration, Data Structures, Database Management Systems, Databases, Device Forensics, Digital Communications, Digital Forensics, Embedded Systems, Forensic Accounting, Formal Methods, Fraud Prevention and Management, Hardware Reverse Engineering, Hardware/Firmware Security, Host Forensics, IA Architectures, IA Compliance, IA Standards, Independent/Directed Study/Research, Industrial Control Systems, Introduction to Theory of Computation, Intrusion Detection/Prevention Systems, Life-Cycle Security, Linux System Administration, Low Level Programming, Media Forensics, Mobile Technologies, Network Forensics, Network Security Administration, Network Technology and Protocols, Operating Systems Administration, Operating Systems Hardening, Operating Systems Theory, Penetration Testing, Privacy, QA/Functional Testing, Radio Frequency Principles, Secure Programming Practices, Software Assurance, Software Reverse Engineering, Software Security Analysis, Supply Chain Security, Systems Certification and Accreditation, Systems Programming, Systems Security Engineering, Virtualization Technologies, Vulnerability Analysis, Web Application Security, Windows System Administration, Wireless Sensor Networks
NCyTE Cybersecurity Foundations 1
From NCyTE: Cybersecurity Foundations, combined and ordered by me
- Confidentiality, Integrity, Availability, Access, Authentication, Authorization, Non-Repudiation, Privacy; Access Control Models (MAC, DAC, RBAC, Lattice);
- Legal issues; Ethics (Ethics associated with cybersecurity profession)
- Applications of Cryptography and PKI; Data Security (in transmission, at rest, in processing)
NCyTE Cybersecurity Foundations 2
From NCyTE: Cybersecurity Foundations, combined and ordered by me
- Threats and Adversaries (threat actors, malware, natural phenomena); Vulnerabilities and Risk management (include backups and recovery); Common Attacks; Describe potential system attacks and the actors that might perform them.
- Security Mechanisms (e.g., Identification/Authentication, Audit); Session Management; Exception Management; Malicious activity detection / forms of attack; Appropriate Countermeasures; Security Models (Bell-La Padula, etc.)
Course Outline 1
- What are we protecting: Data and Systems
- Identity and AAA
- What’s Legal?
- Networking and Security
Course Outline 2
- DoS and Botnets
- Email systems, Phishing, and Social Engineering
- Encryption (symmetric and asymmetric) and Applications
- Malware and Defenses
Course Outline 3
- TTPs (Tactics, Techniques, and Procedures)
- Vulnerabilities
- Security Principles and Risk Assessment
- Controls and Policies
Terminology, Abbreviation, and Acronyms
So many to remember and look up
- Master NIST Cybersecurity Glossary, very complete but was slow when I tested it.
- National Initiative for Cybersecurity Careers and Studies Glossary. Good but not comprehensive.
- SANS Institute Glossary
Not a Programming Class
We may write some small programs to illustrate some core concepts
You may use Python
You may use JavaScript via Node.js (or the browser)
No other languages will be accepted
Hands On: What We Will Do
- Hands on Network Sniffing using WireShark
- Hands on Cryptography with Python
- Hands on Network Scanning with NMap
- Hands on detection with YARA
- Hands on Web Security and Privacy via Browser tools and Tor
Hands On: What We Don’t Have Time For
- Hands on with Pen testing tools
- Hands on with Forensics
- Hands on Malware analysis
The Cybersecurity Certification and Training Business
Training and Certification
- Many companies and organizations have jumped into the cybersecurity training and certification space.
- They make money by administering exams and granting certificates. These certificates may have a expiration date.
- They also make money by selling training to pass their own exams
- EXTREME CAUTION is advised before spending any money in this area
Some Current Reviews of Certifications
Certified Ethical Hacker (CEH) 1
Certified Ethical Hacker (CEH) 2
They offer a lot of different certifications and sell training courses.
- Certified Application Security Engineer - CASE .NET Secure Coding
- Certified Application Security Engineer - CASE Java Secure Coding
- Certified Blockchain Professional - CBP Blockchain
- Certified Chief Information Security Officer - CCISO Executive Management
- Certified Encryption Specialist - ECES Encryption
- Certified Ethical Hacker - CEH Ethical Hacking
- Certified Incident Handler - ECIH Incident Handling
- Certified Network Defender - CND Network Security
- Certified Penetration Testing Professional - CPENT Pen Testing
- Certified Project Management - CPM IT Project Management
- Certified Secure Computer User - CSCU Fundamentals
- Certified SOC Analyst - CSA Incident Handling
- Certified Threat Intelligence Analyst - CTIA Incident Handling
- Computer Hacking Forensics Investigator - CHFI Computer Forensics
- Dark Web Forensics Computer Forensics
- Disaster Recovery Professional - EDRP Disaster Recovery
- Ethical Hacking Core Skills - EHCS Ethical Hacking
- Malware and Memory Forensics Computer Forensics
- Mobile Forensics Computer Forensics
- PHP Security (MicroDegree) Secure Coding
- Python Security (MicroDegree) Secure Coding
- Risk Management Approach and Practices - RM Executive Management
- STORM: Ethical Hacking Core Skills Mobile Security Toolkit
- STORM: Ethical Hacking Intermediate Skills Mobile Security Toolkit
ISC2 Part 1
International Information System Security Certification Consortium
(ISC)^2 – Seems to be a big certification organization in this area. They also sell training.
ISC2 Part 2
Some of ISC^2 certifications
- CISSP – Certified Information Systems Security Professional
- SSCP – Systems Security Certified Practitioner
- CCSP – Certified Cloud Security Professional
- CAP – Certified Authorization Professional
- CSSLP – Certified Secure Software Lifecycle Professional
- HCISPP – HealthCare Information Security and Privacy Practitioner
- CISSP - ISSAP – Information Systems Security Architecture Professional
- CISSP - ISSEP – Information Systems Security Engineering Professional
- CISSP - ISSMP – Information Systems Security Management Professional Associate of (ISC)²