Data and Systems
Dr. Greg Bernstein
July 23th, 2021
Types of Data
References
Why Data?
From NIST Data Classification Practices Facilitating Data-Centric Security Management
A critical factor for achieving success in any business is the ability to share information and collaborate effectively and efficiently while satisfying the security and privacy requirements for protecting that information.
Data Security
From NIST Data Classification Practices Facilitating Data-Centric Security Management
Data-centric security management necessarily depends on organizations knowing what data they have, what its characteristics are, and what security and privacy requirements it needs to meet so the necessary protections can be achieved.
Traditional Classified Information
From Wikipedia: Classified Information
Classified information is material that a government body deems to be sensitive information that must be protected. Access is restricted by law or regulation to particular groups of people with the necessary security clearance and need to know, and mishandling of the material can incur criminal penalties.
Traditional US Information Classifications
From Wikipedia: Classified Information in the US
The desired degree of secrecy about such information is known as its sensitivity. Sensitivity is based upon a calculation of the damage to national security that the release of the information would cause. The United States has three levels of classification: Confidential, Secret, and Top Secret. Each level of classification indicates an increasing degree of sensitivity.
Traditional US Information Classification Levels
From Wikipedia: Classified Information in the US
- Confidential: information that would “damage” national security if publicly disclosed,
- Secret: unauthorized disclosure would cause “serious damage”
- Top Secret: unauthorized disclosure of which reasonably could be expected to cause “exceptionally grave damage”
Government Security Clearances
From Wikipedia: Security Clearance
A security clearance is a status granted to individuals allowing them access to classified information (state or organizational secrets), after completion of a background check. A clearance by itself is normally not sufficient to gain access; the organization must also determine that the cleared individual needs to know specific information.
Need to Know
From Wikipedia: Classified Information in the US
Having Top Secret clearance does not allow one to view all Top Secret documents. The user of the information must possess the clearance necessary for the sensitivity of the information, as well as a legitimate need to obtain the information. For example, all US military pilots are required to obtain at least a Secret clearance, but they may only access documents directly related to their orders.
Finer Granularity: Code Word
From Wikipedia: Classified Information in the US
However some information is compartmentalized by adding a code word so that only those who have been cleared for each code word can see it. This information is also known as “Sensitive Compartmented Information” (SCI). A document marked SECRET (CODE WORD) could be viewed only by a person with a secret or top secret clearance and that specific code word clearance.
What About My Data 1?
Who needs to know my:
- Academic information (schools attended, grades, classes taken, disciplinary actions, etc..)
- Health information (vaccine status, health conditions, pre-existing conditions, treatments, allergies, etc…)
- Financial information (purchase history, credit history/score, bank balances, investments, loans, defaults, bankruptcy, etc…)
- Employment information (current employer, past employers, whether you are searching for a job, etc…)
- Personal information (name, sex, age, location, computer brand, browser, browsing history)
What About My Data 2?
Who wants to know my information:
- Governments (for legitimate and illegitimate purposes)
- Businesses (advertising, to deliver services and products, etc…)
- Data brokers (to sell to others)
- Criminals (for fraud and abuse)
- Health Care Providers (for treatment, for insurance purposes, etc…)
Modern Data Classification 1
From NIST Data Classification Practices Facilitating Data-Centric Security Management
In the early days of digital computing, data classification was largely associated with the armed forces and defense industry. Classification terms such as TOP SECRET, while well known to the public due to media portrayals, were nearly completely absent outside of certain government and military environments.
Modern Data Classification 2
From NIST Data Classification Practices Facilitating Data-Centric Security Management
A number of forces have come to bear on all organizations that have catapulted data classification and labeling to the forefront and resulted in a sense of urgency regarding establishment of models for use with all data. Laws and regulations such as the California Consumer Privacy Act (CCPA), Children’s Online Privacy Protection Act (COPPA), Fair Credit Reporting Act (FCRA)/Fair and Accurate Credit Transactions Act (FACTA),
Modern Data Classification 3
From NIST Data Classification Practices Facilitating Data-Centric Security Management
Family Educational Rights and Privacy Act (FERPA), General Data Protection Regulation (GDPR), Gramm Leach Bliley Act (GLBA), Health Information Portability and Accountability Act (HIPAA), and Payment Card Industry Data Security Standard (PCI DSS) mandate that data containing certain types of information be handled with specific safeguards.
Modern Data Classification 4
Currently there are NO Standardized mechanisms for communicating data characteristics and protection requirements across systems and organizations.
Modern Data Classification 5
From From NIST Data Classification Practices Facilitating Data-Centric Security Management, May 2021
Standardized mechanisms for communicating data characteristics and protection requirements across systems and organizations are needed to make data-centric security management feasible at scale. The desired approach for this is to define and use data classifications, and this project will examine that approach.
Types of Systems
Overview
We are concerned with a wide variety of systems that can be connected to a network
- IT (Enterprise, Home, Cloud, IoT, Windows, Mac, Linux)
- Mobile (Android, IOS, etc…)
- OT (ICS, Industrial IOT, Critical Infrastructure)
- Legacy
IT Mac
From WildPressure targets the macOS platform, July 7th, 2021
IT Windows
From From Word to Lateral Movement in 1 hour, June 20th, 2021

IT Linux
From Common Vulnerabilities and Exposure (CVE) database Linux
IoT
From Vulnerability Spotlight: Remote code execution vulnerabilities in Cosori smart air fryer
IoT: Obscure Software Issue…
End of news email mostly on SolarWinds hack…
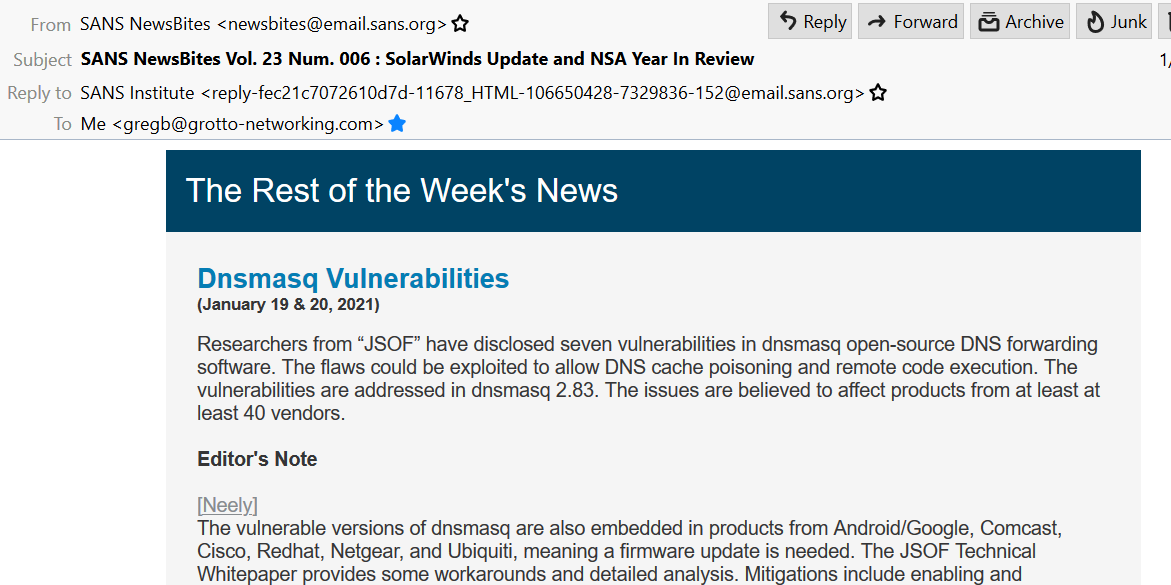
IoT: Impacts…

IoT: Patching my Router
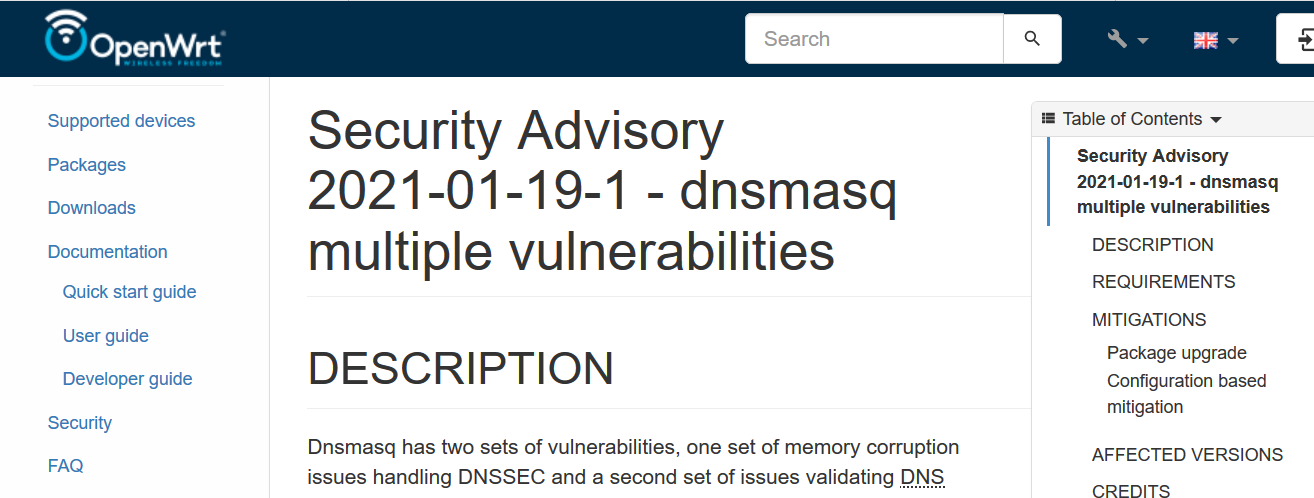
IoT: DNSmasq Vulnerabilities Links
- DNSpooq: Cache Poisoning and RCE in Popular DNS Forwarder dnsmasq, technical white paper.
- The A Register, security blog
- OpenWrt Security Advisory, Report and mitigation procedure.
- An Illustrated Guide to the Kaminsky DNS Vulnerability
Android
From Gustuff banking botnet targets Australia, April 9th, 2019
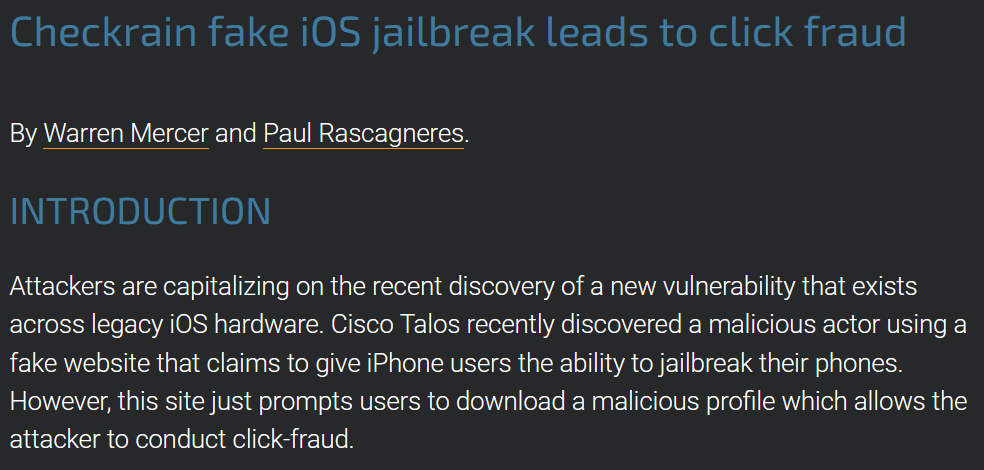
IOS (iPhone)
From Checkrain fake iOS jailbreak leads to click fraud, October 15th, 2019
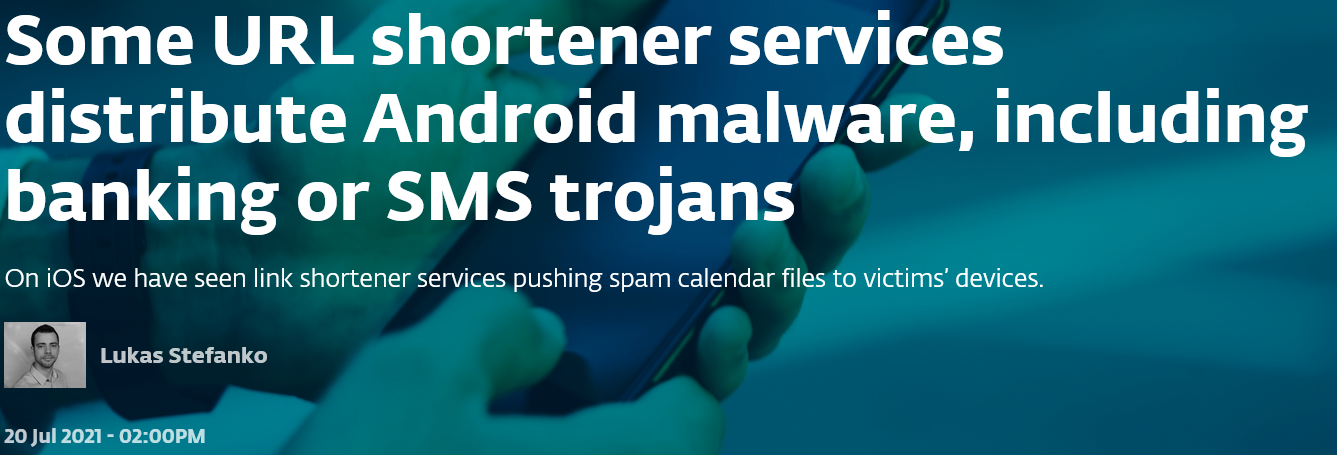
Android and IOS (recent)
From Some URL shortener services distribute Android malware, including banking or SMS trojans, July 20th, 2021.
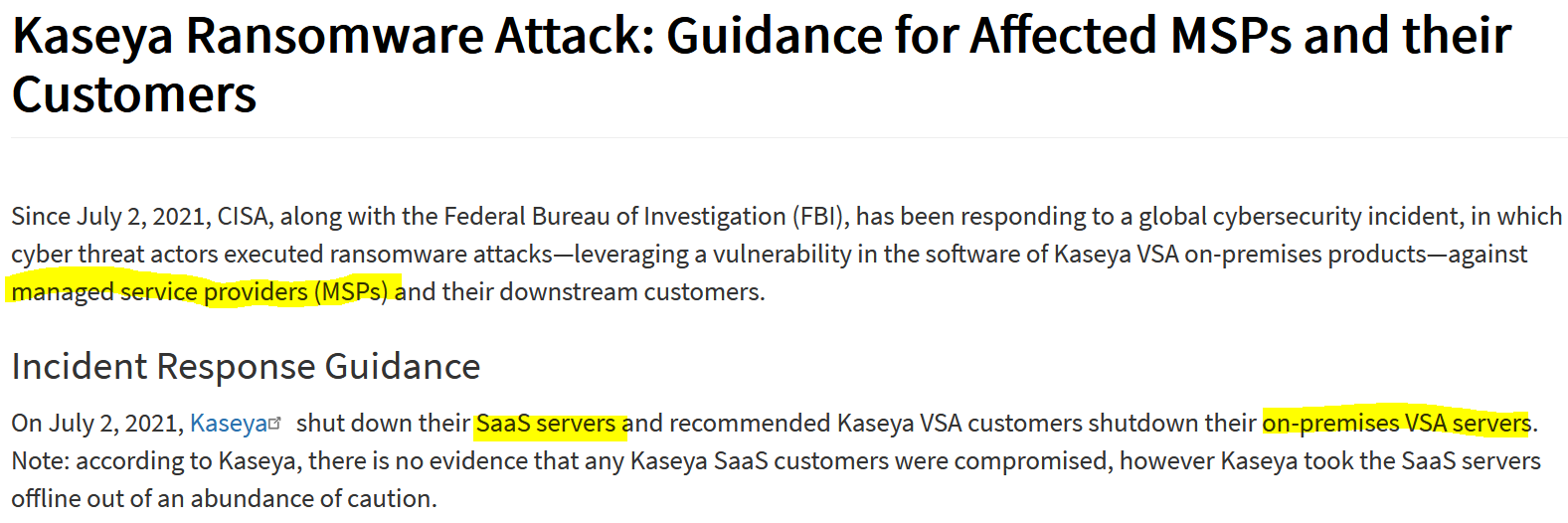
Cloud Related
From Kaseya Ransomware Attack: Guidance for Affected MSPs and their Customers, July 11th, 2021. Kaseya VSA is software for remote management of computers and networks
Operational Technology
From NIST: Operational Technology Security (project)
Operational technology (OT) encompasses a broad range of programmable systems or devices that interact with the physical environment (or manage devices that interact with the physical environment). These systems/devices detect or cause a direct change through the monitoring and/or control of devices, processes, and events. Examples include industrial control systems, building management systems, transportation systems, physical access control systems, physical environment monitoring systems, and physical environment measurement systems.
Industrial Control Systems: Def 1
From SP 800-82 Rev. 2 Guide to Industrial Control Systems (ICS) Security
Industrial control system (ICS) is a general term that encompasses several types of control systems, including supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS), and other control system configurations such as Programmable Logic Controllers (PLC) often found in the industrial sectors and critical infrastructures.
Industrial Control Systems: Def 2
From SP 800-82 Rev. 2 Guide to Industrial Control Systems (ICS) Security
An ICS consists of combinations of control components (e.g., electrical, mechanical, hydraulic, pneumatic) that act together to achieve an industrial objective (e.g., manufacturing, transportation of matter or energy).
Industrial Control Systems: Who/Where
From SP 800-82 Rev. 2 Guide to Industrial Control Systems (ICS) Security
ICS control industrial processes are typically used in electrical, water and wastewater, oil and natural gas, chemical, transportation, pharmaceutical, pulp and paper, food and beverage, and discrete manufacturing (e.g., automotive, aerospace, and durable goods) industries.
Industrial Control Systems: Evolution
From SP 800-82 Rev. 2 Guide to Industrial Control Systems (ICS) Security
Initially, ICS had little resemblance to traditional information technology (IT) systems in that ICS were isolated systems running proprietary control protocols using specialized hardware and software. Many ICS components were in physically secured areas and the components were not connected to IT networks or systems. Widely available, low-cost Internet Protocol (IP) devices are now replacing proprietary solutions, which increases the possibility of cybersecurity vulnerabilities and incidents.
Select Famous ICS Attacks
From History of Industrial Control System Cyber Incidents 2018
| Year | Name | Description |
|---|---|---|
| 2000 | Maroochy Water | caused the release of more than 265,000 gallons of untreated sewage |
| 2010 | Stuxnet | Attack on Iranian centrifuges |
| 2012 | Shamoon | Target large energy companies in the Middle East |
| 2013 | New York Dam | a cyber-attack on the Bowman Dam in NY |
| 2017 | NotPetya | Malware that targeted the Ukraine |
| 2017 | TRITON | Industrial safety systems in the Middle East |
Critical Infrastructure
Critical Infrastructure: Definition
Framework for Improving Critical Infrastructure Cybersecurity Version 1.1
Critical infrastructure is defined in the U.S. Patriot Act of 20015 as “systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters.”
Critical Infrastructure: Who
Framework for Improving Critical Infrastructure Cybersecurity Version 1.1
The critical infrastructure community includes public and private owners and operators,and other entities with a role in securing the Nation’s infrastructure. Members of each critical infrastructure sector perform functions that are supported by the broad category of technology,
Critical Infrastructure: What
Framework for Improving Critical Infrastructure Cybersecurity Version 1.1
Selected Critical Sectors
From NIST: Critical Infrastructure Resources
| Sector | Sector | Sector |
|---|---|---|
| CHEMICAL | CRITICAL MANUFACTURING | DAMS |
| DEFENSE INDUSTRIAL | EMERGENCY SERVICES | ENERGY |
| FINANCIAL SERVICES | FOOD AND AGRICULTURAL | GOVERNMENT FACILITIES |
| HEALTHCARE AND PUBLIC HEALTH | INFORMATION TECHNOLOGY | NUCLEAR |
| TRANSPORTATION SYSTEMS |
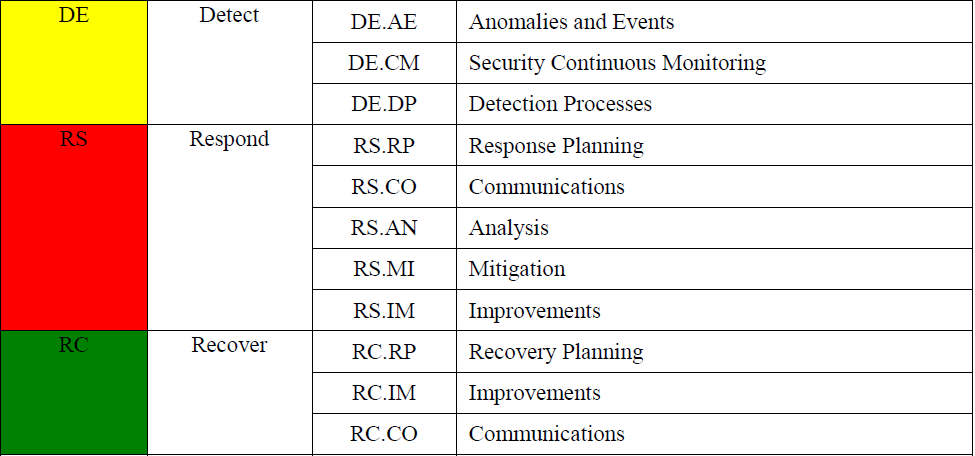
Security Functions for Critical Infrastructure
- Identify
- Protect
- Detect
- Respond
- Recover
Securing Critical Infrastructure Categories 1
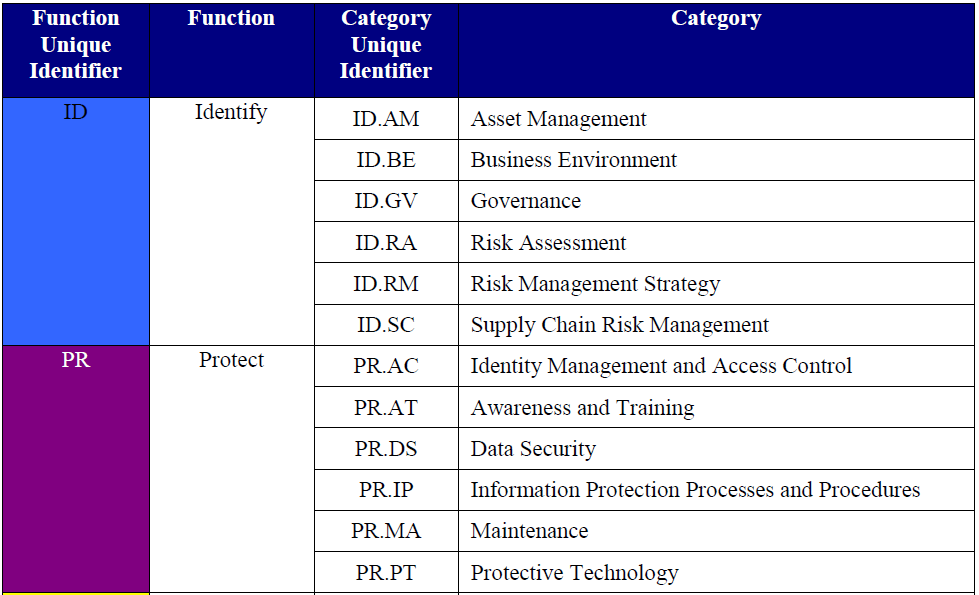
Securing Critical Infrastructure Categories 2