Cybersecurity and the CIA Triangle
Dr. Greg Bernstein
August 6th, 2021
CIA Triangle
References
Cybok Introduction
FIPS PUB 199 Standards for Security Categorization of Federal Information and Information Systems defines each term and cites laws.
Cybersecurity Definition
From Cybok Introduction
Cybersecurity refers to the protection of information systems (hardware, software and associated infrastructure), the data on them, and the services they provide, from unauthorized access, harm or misuse. This includes harm caused intentionally by the operator of the system, or accidentally, as a result of failing to follow security procedures.
Information Security Definition
From Cybok Introduction, ISO 27000
Preservation of confidentiality, integrity and availability of information.
In addition, other properties, such as authenticity, accountability, non-repudiation, and reliability can also be involved.
C.I.A.
No, not the U.S. Government Agency
- Confidentiality
- Integrity
- Availability
Confidentiality 1
From MDN/NIST:Confidentiality refers to protecting information from being accessed by unauthorized parties. In other words, only the people who are authorized to do so can gain access to sensitive data.
Imagine your bank records. You should be able to access them, of course, and employees at the bank who are helping you with a transaction should be able to access them, but no one else should. A failure to maintain confidentiality means that someone who shouldn’t have access has managed to get it, through intentional behavior or by accident.
Confidentiality 2
From MDN/NIST:
Such a failure of confidentiality, commonly known as a breach, typically cannot be remedied. Once the secret has been revealed, there’s no way to un-reveal it. If your bank records are posted on a public website, everyone can know your bank account number, balance, etc., and that information can’t be erased from their minds, papers, computers, and other places. Nearly all the major security incidents reported in the media today involve major losses of confidentiality.
FIPS CONFIDENTIALITY
From FIPS PUB 199 Standards for Security Categorization of Federal Information and Information Systems
“Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information…” [44 U.S.C., Sec. 3542] A loss of confidentiality is the unauthorized disclosure of information.
Integrity 1
From MDN/NIST:
Integrity refers to ensuring the authenticity of information—that information is not altered, and that the source of the information is genuine. Imagine that you have a website and you sell products on that site. Now imagine that an attacker can shop on your web site and maliciously alter the prices of your products, so that they can buy anything for whatever price they choose. That would be a failure of integrity, because your information—in this case, the price of a product—has been altered and you didn’t authorize this alteration.
Integrity 2
From MDN/NIST:
Another example of a failure of integrity is when you try to connect to a website and a malicious attacker between you and the website redirects your traffic to a different website. In this case, the site you are directed to is not genuine.
Integrity 3
From the CISSP Study Guide
Other concepts, conditions, and aspects of integrity include the following:
- Accuracy: Being correct and precise
- Truthfulness: Being a true reflection of reality
- Authenticity: Being authentic or genuine
- Validity: Being factually or logically sound
Integrity 4
From the CISSP Study Guide
- Nonrepudiation: Not being able to deny having performed an action or activity or being able to verify the origin of a communication or event
- Accountability: Being responsible or obligated for actions and results
- Responsibility: Being in charge or having control over something or someone
- Completeness: Having all needed and necessary components or parts
- Comprehensiveness: Being complete in scope; the full inclusion of all needed elements
Nonrepudiation 1
From the CISSP Study Guide
Nonrepudiation ensures that the subject of an activity or who caused an event cannot deny that the event occurred. Nonrepudiation prevents a subject from claiming not to have sent a message, not to have performed an action, or not to have been the cause of an event.
Nonrepudiation 2
From the CISSP Study Guide
Nonrepudiation is made possible through identification, authentication, authorization, accountability, and auditing. Nonrepudiation can be established using digital certificates, session identifiers, transaction logs, and numerous other transactional and access control mechanisms. A system built without proper enforcement of nonrepudiation does not provide verification that a specific entity performed a certain action. Nonrepudiation is an essential part of accountability. A suspect cannot be held accountable if they can repudiate the claim against them.
FIPS INTEGRITY
From FIPS PUB 199 Standards for Security Categorization of Federal Information and Information Systems
“Guarding against improper information modification or destruction, and includes ensuring information non-repudiation and authenticity…” [44 U.S.C., Sec. 3542] A loss of integrity is the unauthorized modification or destruction of information.
Availability
From Wikipedia
For any information system to serve its purpose, the information must be available when it is needed. This means the computing systems used to store and process the information, the security controls used to protect it, and the communication channels used to access it must be functioning correctly.
Ensuring availability also involves preventing denial-of-service attacks, such as a flood of incoming messages to the target system, essentially forcing it to shut down.
FIPS AVAILABILITY
From FIPS PUB 199 Standards for Security Categorization of Federal Information and Information Systems
“Ensuring timely and reliable access to and use of information…” [44 U.S.C., SEC. 3542] A loss of availability is the disruption of access to or use of information or an information system.
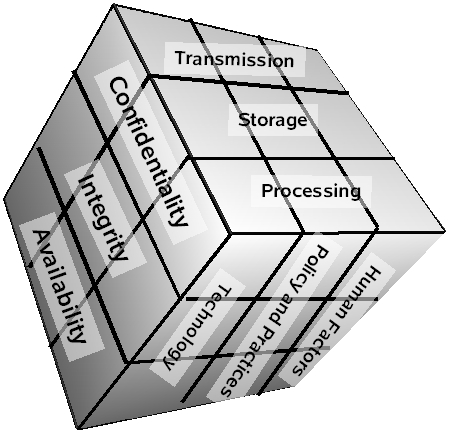
Enhanced Model: Data States
As we will see data is vulnerable in different ways depending on its “state”:
- Data at Rest: Storage
- Data in Transit: Transmission
- Data in Use: Processing
The McCumber Cube
An enhanced model from Wikipedia: McCumber Cube