Identity and Access Control
Dr. Greg M. Bernstein
July 2nd, 2021
Identity and Access Control
Readings
From: Authentication, Authorisation & Accountability (AAA) Knowledge Area Issue 1.0, Dieter Gollmann Hamburg University of Technology & Nanyang Technological University Singapore, 2019.
- From Section 3.1 Access Control: 3.1.1, 3.1.2, 3.1.3, 3.1.5, 3.1.8
- Section 3.2 Enforcing Access Control (3.2.2 Important), Section 3.3 is optional
- Section 4 Access Control in Distributed Systems is optional, Section 4.2 Origin-based Policies is of interest for Web application security
- From Section 5 Authentication: 5.1, 5.2, 5.3 (5.3.1, 5.3.2), Section 6 Accountability
References 1
References 2
- Wikipedia: Kerberos
- Wikipedia: Diameter used in 3GPP interfaces, Wikipedia: TACACS, TACACS was used in old Unix systems for terminal access control, TACACS+ is a Cisco protocol for AAA (from 1993).
- Wikipedia: LDAP, OpenLDAP open source LDAP server, ApacheDS™ LDAP and Kerberos server written in Java
- Linux Logging Complete Guide, rsyslog Ubuntu default log system, syslog-ng Another popular log system.
Access Control
From CyBOK AAA Knowledge Area
Access control is “the process of granting or denying specic requests . . .”. This process needs the following inputs
- Who issued the request?
- What is requested?
- Which rules are applicable when deciding on the request?
Requestor
From CyBOK AAA Knowledge Area
- A person
- A machine
- A process or machine on behalf of a person or other machine
Security Policy
From CyBOK AAA Knowledge Area
The term security policy is used both for the general rules within an organization that stipulate how sensitive resources should be protected, and for the rules enforced by IT systems on the resources they manage.
Enforcing Access Control 1
From CyBOK AAA Knowledge Area
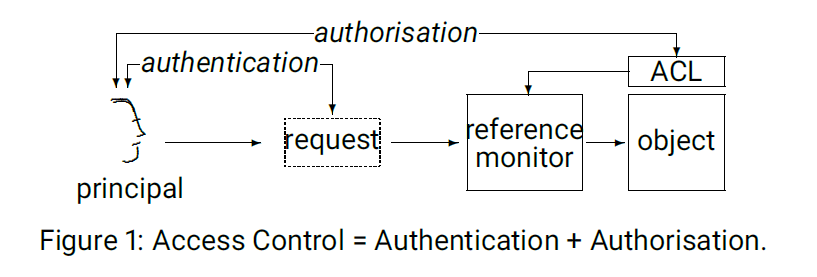
Enforcing Access Control 2
From CyBOK AAA Knowledge Area
- Access Control List (ACL): The rules that indicate what a principal can do with an object
- Reference Monitor: Uses the access control list to enforce the security policy ("authorizes the access)
- Authentication: Determines that the principal is who they claim to be
- Authorization: Sets up the policies/rules that become the ACL
Two Meanings for Authorization
- Setting up the security policy
- Enforcement of the policy on an individual request by a reference monitor
Authorization/Policy Setting
Access Control Terminology
From CyBOK AAA Knowledge Area
- Principal: stands for the active entity in an access request
- Subject: stands for the active entity making a request when a system executes some program.
- Object: is the passive entity in an access request.
Principals and Subjects
From CyBOK AAA Knowledge Area
A subject speaks for a principal when the runtime environment associates the subject with the principal in an unforgeable manner.
The original example for creating a subject that speaks for a principal is user log-in, spawning a process running under the user identity of the person that had been authenticated.
The research literature does not always maintain this distinction between principals and subjects.
Access Rights
Access rights express how a principal may access an object.
Similar terms: Permissions, Privileges
Concept: Access Control Matrix
From Wikipedia: Access Control Matrix, where “Role 1” and “Role 2” are principals and “Asset 1”, “Asset 2”, “File”, “Device” are objects

Core Policies: DAC and MAC
Early policy categories from the defense sector still used today
- Discretionary Access Control (DAC): Owner of resource gets to set access policies
- Mandatory Access Control (MAC): generally access policies set by the system, or in defense by security classification levels. Contemporary examples: Security-Enhanced Linux (SELinux) and Security-Enhanced (SE) Android.
Role Based Access Control
From CyBOK AAA Knowledge Area
- Roles are an intermediate layer between users and the permissions to execute certain operations.
- Users are assigned roles and are authorized to execute the operations linked to their active role.
RBAC Example: Learning Management Systems (LMS)
What are some of the different roles and their associated privileges on your current LMS, e.g., Blackboard?
RBAC Example: Club Website Project
In my CS351 and CS651 courses we build a full stack club app/website
- Who can see club member list
- Who can approve or delete club members
- Who can see, add, delete, club activities
RBAC and ABAC Resources
Attribute Based Access Control
From NIST: Guide to ABAC Definition and Considerations
ABAC is a logical access control methodology where authorization to perform a set of operations is determined by evaluating attributes associated with the subject, object, requested operations, and, in some cases, environment conditions against policy, rules, or relationships that describe the allowable operations for a given set of attributes.
ABAC Example Diagram
RBAC vs. ABAC: Definitions & When to Use

Example Scenarios for ABAC/RBAC 1
RBAC vs. ABAC: Definitions & When to Use
Small workgroups. RBAC is best. Defining work by role is simple when the company is small and the files are few.
Geographically diverse workgroups. ABAC is a good choice. You can define access by employee type, location, and business hours. You could only allow access during business hours for the specific time zone of a branch.
Time-defined workgroups. ABAC is preferred. Some sensitive documents or systems shouldn’t be accessible outside of office hours. An ABAC system allows for time-based rules.
Example Scenarios for ABAC/RBAC 2
RBAC vs. ABAC: Definitions & When to Use
Simply structured workgroups. RBAC is best. Your company is large, but access is defined by the jobs people do.
Creative enterprises. ABAC is ideal because creative companies often use their files in unique ways. Sometimes, everyone needs to see certain documents; other times, only a few people do. Access needs change by the document, not by the roles.
Complicated Access Control Example
NIST: Access Rights Management for the Financial Services Sector
Authorization Systems and Tools
Types of Access Control Systems
- Individual Devices (Computers, Phones, etc…)
- Web Applications and APIs
- WiFi and Network Access Systems
- Network Firewalls
- Single Sign On, Federated Access Control, Delegation
Network Access Control Systems
- Wikipedia: Remote Authentication Dial-In User Service (RADIUS), OpenWRT: Introduction to 802.1X, FreeRADIUS,FreeRADIUS Technical Guide Used in WiFi access control. For larger systems frequently combined with Kerberos.
- Wikipedia: Kerberos also authenticates client and servers. Used in Windows and some Linux distributions.
- Wikipedia: Diameter used in 3GPP interfaces, Wikipedia: TACACS, TACACS was used in old Unix systems for terminal access control
Distributed Systems and Access Controls
- Wikipedia: OpenID, Wikipedia: OAuth access/authentication delegation, e.g. company X with tell company Y that you are who you say you are.
- Wikipedia: Security Assertion Markup Language (SAML) “An important use case that SAML addresses is web-browser single sign-on (SSO)”
- Wikipedia: eXtensible Access Control Markup Language (XACML)
OpenID 1
From Wikipedia: OpenID
OpenID is an open standard and decentralized authentication protocol. Promoted by the non-profit OpenID Foundation, it allows users to be authenticated by cooperating sites (known as relying parties, or RP) using a third-party service, eliminating the need for webmasters to provide their own ad hoc login systems, and allowing users to log into multiple unrelated websites without having to have a separate identity and password for each.
OpenID 2
From Wikipedia: OpenID
As of March 2016, there are over 1 billion OpenID-enabled accounts on the Internet (see below) and approximately 1,100,934 sites have integrated OpenID consumer support: AOL, Flickr, Google, Amazon.com, Canonical, LiveJournal, Microsoft, Mixi, Myspace, Novell, OpenStreetMap,…
Can you think of any privacy implications of using OpenID versus email and password for a website login?
SAML
From Wikipedia: Security Assertion Markup Language (SAML)
Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is an XML-based markup language for security assertions (statements that service providers use to make access-control decisions). An important use case that SAML addresses is web-browser single sign-on (SSO).
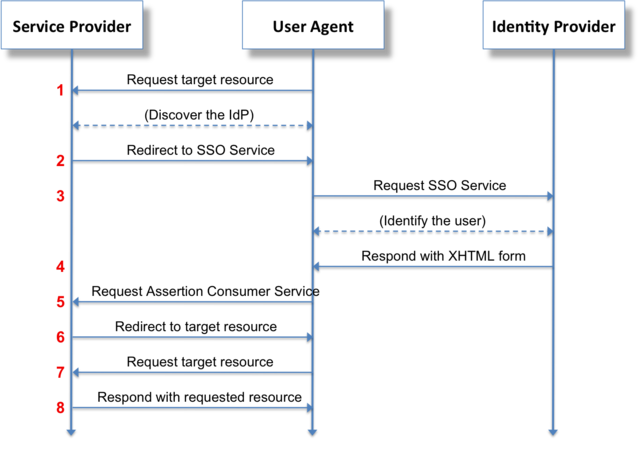
SAML SSO
From Wikipedia: Security Assertion Markup Language (SAML)
XACML
From Wikipedia: eXtensible Access Control Markup Language (XACML)
XACML stands for “eXtensible Access Control Markup Language”. The standard defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies.
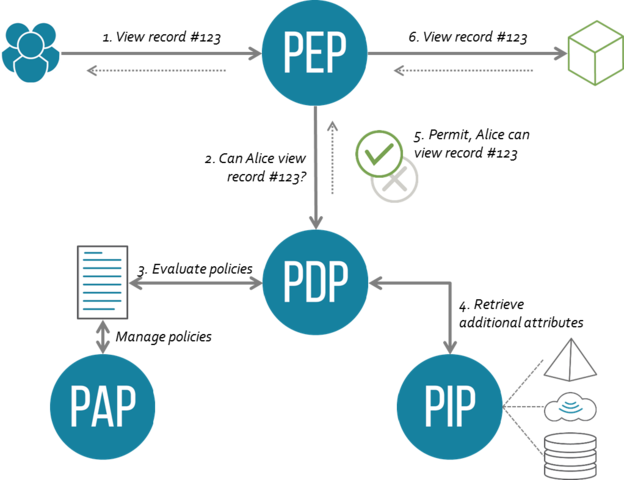
XACML Flow
From Wikipedia: eXtensible Access Control Markup Language (XACML)
- A user sends a request which is intercepted by the Policy Enforcement Point (PEP)
- The PEP converts the request into a XACML authorization request
- The PEP forwards the authorization request to the Policy Decision Point (PDP)
- The PDP evaluates the authorization request against the policies it is configured with. The policies are acquired via the Policy Retrieval Point (PRP) and managed by the Policy Administration Point (PAP). If needed it also retrieves attribute values from underlying Policy Information Points (PIP).
- The PDP reaches a decision (Permit / Deny / NotApplicable / Indeterminate) and returns it to the PEP
XACML Diagram
From Wikipedia: eXtensible Access Control Markup Language (XACML)
Example XACML Product
From Axiomatics
Authentication
Authentication Definition 1
From OWASP:
Authentication is the process of verification that an individual, entity or website is who it claims to be. Authentication in the context of web applications is commonly performed by submitting a user name or ID and one or more items of private information that only a given user should know.
Authentication Definition 2
From Wikipedia
Authentication is the act of verifying a claim of identity.
Authentication: Analog Example
From Wikipedia
When John Doe goes into a bank to make a withdrawal, he tells the bank teller he is John Doe, a claim of identity. The bank teller asks to see a photo ID, so he hands the teller his driver’s license. The bank teller checks the license to make sure it has John Doe printed on it and compares the photograph on the license against the person claiming to be John Doe. If the photo and name match the person, then the teller has authenticated that John Doe is who he claimed to be.
Authentication Information
From Wikipedia: Multi-factor authentication
There are multiple different types of information that can be used for authentication:
- Something you know: things such as a PIN, a password, etc…
- Something you have: a driver’s license or a magnetic swipe card
- Something you are: biometrics, including fingerprints, retina (eye) scans, etc…
Multi-Factor Authentication
From Wikipedia: Multi-factor authentication
Multi-factor authentication is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something only the user knows), possession (something only the user has), and inherence (something only the user is). MFA protects the user from an unknown person trying to access their data such as personal ID details or financial assets.
Open Source MFA Server
From PrivacyID3A
Related Systems
Directories
A directory is a specialized database specifically designed for searching and browsing, in additional to supporting basic lookup and update functions.
Directories vs Databases
Directories tend to contain descriptive, attribute-based information and support sophisticated filtering capabilities. Directories generally do not support complicated transaction or roll-back schemes found in database management systems designed for handling high-volume complex updates. Directory updates are typically simple all-or-nothing changes, if they are allowed at all. Directories are generally tuned to give quick response to high-volume lookup or search operations.
Accountability
Accounting
We use logging and monitoring to determine:
- Who is using the system(s)?
- How are they using the systems?
- Is that use appropriate?
Login Logging Example
Multiple SSH accesses to my Linux server from my Laptop
Jun 28 15:17:52 greg-desktop systemd-logind[1348]: Removed session 6934.
Jun 28 15:18:17 greg-desktop dbus-daemon[1289]: [system] Failed to activate service 'org.bluez': timed out (service_start_timeout=25000ms)
Jun 28 15:18:59 greg-desktop sshd[2431044]: rexec line 15: Deprecated option UsePrivilegeSeparation
Jun 28 15:18:59 greg-desktop sshd[2431044]: rexec line 18: Deprecated option KeyRegenerationInterval
Jun 28 15:18:59 greg-desktop sshd[2431044]: rexec line 19: Deprecated option ServerKeyBits
Jun 28 15:18:59 greg-desktop sshd[2431044]: rexec line 30: Deprecated option RSAAuthentication
Jun 28 15:18:59 greg-desktop sshd[2431044]: rexec line 37: Deprecated option RhostsRSAAuthentication
Jun 28 15:18:59 greg-desktop sshd[2431044]: reprocess config line 30: Deprecated option RSAAuthentication
Jun 28 15:18:59 greg-desktop sshd[2431044]: reprocess config line 37: Deprecated option RhostsRSAAuthentication
Jun 28 15:18:59 greg-desktop sshd[2431044]: Accepted publickey for greg from 192.168.1.228 port 1099 ssh2: RSA SHA256:EkJl4laenV4P0FOvL+wN5FVJY8YH7tEaUai5S+QcPaY
Jun 28 15:18:59 greg-desktop sshd[2431044]: pam_unix(sshd:session): session opened for user greg by (uid=0)
Jun 28 15:18:59 greg-desktop systemd-logind[1348]: New session 6936 of user greg.
Jun 28 15:30:01 greg-desktop CRON[2442746]: pam_unix(cron:session): session opened for user root by (uid=0)
--- log entries not shown
Jun 28 16:17:01 greg-desktop CRON[2492253]: pam_unix(cron:session): session closed for user root
Jun 28 16:18:59 greg-desktop sshd[2431044]: pam_unix(sshd:session): session closed for user greg
---
Jun 28 16:29:48 greg-desktop systemd-logind[1348]: Removed session 6957.
Jun 28 16:30:01 greg-desktop CRON[2505926]: pam_unix(cron:session): session opened for user root by (uid=0)
Jun 28 16:30:01 greg-desktop CRON[2505926]: pam_unix(cron:session): session closed for user root
Jun 28 16:30:05 greg-desktop sshd[2505935]: rexec line 15: Deprecated option UsePrivilegeSeparation
Jun 28 16:30:05 greg-desktop sshd[2505935]: rexec line 18: Deprecated option KeyRegenerationInterval
Jun 28 16:30:05 greg-desktop sshd[2505935]: rexec line 19: Deprecated option ServerKeyBits
Jun 28 16:30:05 greg-desktop sshd[2505935]: rexec line 30: Deprecated option RSAAuthentication
Jun 28 16:30:05 greg-desktop sshd[2505935]: rexec line 37: Deprecated option RhostsRSAAuthentication
Jun 28 16:30:05 greg-desktop sshd[2505935]: reprocess config line 30: Deprecated option RSAAuthentication
Jun 28 16:30:05 greg-desktop sshd[2505935]: reprocess config line 37: Deprecated option RhostsRSAAuthentication
Jun 28 16:30:05 greg-desktop sshd[2505935]: Accepted publickey for greg from 192.168.1.228 port 4637 ssh2: RSA SHA256:EkJl4laenV4P0FOvL+wN5FVJY8YH7tEaUai5S+QcPaY
Jun 28 16:30:05 greg-desktop sshd[2505935]: pam_unix(sshd:session): session opened for user greg by (uid=0)
Jun 28 16:30:05 greg-desktop systemd-logind[1348]: New session 6960 of user greg.Wireless Access Log Example 1
Generated by hostapd on OpenWRT Linux
Dec 21 06:32:45 192.168.1.1 hostapd: wlan0: STA a8:3e:0e:4a:94:5b IEEE 802.11: disassociated due to inactivity
Dec 21 06:32:46 192.168.1.1 hostapd: wlan0: STA a8:3e:0e:4a:94:5b IEEE 802.11: deauthenticated due to inactivity (timer DEAUTH/REMOVE)
Dec 21 07:06:38 192.168.1.1 hostapd: wlan0: STA 9c:b6:d0:93:83:d9 IEEE 802.11: authenticated
Dec 21 07:06:38 192.168.1.1 hostapd: wlan0: STA 9c:b6:d0:93:83:d9 IEEE 802.11: associated (aid 3)
Dec 21 07:06:38 192.168.1.1 hostapd: wlan0: AP-STA-CONNECTED 9c:b6:d0:93:83:d9
Dec 21 07:06:38 192.168.1.1 hostapd: wlan0: STA 9c:b6:d0:93:83:d9 WPA: pairwise key handshake completed (RSN)
Dec 20 23:22:16 192.168.1.1 hostapd: wlan1: STA d8:49:2f:25:68:d6 IEEE 802.11: authenticated
Dec 20 23:22:16 192.168.1.1 hostapd: wlan1: STA d8:49:2f:25:68:d6 IEEE 802.11: associated (aid 6)
Dec 20 23:22:16 192.168.1.1 hostapd: wlan1: AP-STA-POSSIBLE-PSK-MISMATCH d8:49:2f:25:68:d6
Dec 20 23:22:17 192.168.1.1 hostapd: wlan1: AP-STA-POSSIBLE-PSK-MISMATCH d8:49:2f:25:68:d6
Dec 20 23:22:18 192.168.1.1 hostapd: wlan1: AP-STA-POSSIBLE-PSK-MISMATCH d8:49:2f:25:68:d6
Dec 20 23:22:19 192.168.1.1 hostapd: wlan1: AP-STA-POSSIBLE-PSK-MISMATCH d8:49:2f:25:68:d6
Dec 20 23:22:21 192.168.1.1 hostapd: wlan1: STA d8:49:2f:25:68:d6 IEEE 802.11: authenticated
Dec 20 23:22:21 192.168.1.1 hostapd: wlan1: STA d8:49:2f:25:68:d6 IEEE 802.11: associated (aid 6)
Dec 20 23:22:21 192.168.1.1 hostapd: wlan1: AP-STA-POSSIBLE-PSK-MISMATCH d8:49:2f:25:68:d6
Dec 20 23:22:22 192.168.1.1 hostapd: wlan1: AP-STA-POSSIBLE-PSK-MISMATCH d8:49:2f:25:68:d6
Dec 20 23:22:23 192.168.1.1 hostapd: wlan1: AP-STA-POSSIBLE-PSK-MISMATCH d8:49:2f:25:68:d6Wireless Access Log Example 2
Generated by hostapd on OpenWRT Linux
- Two WiFi radios: wlan0 is 5GHz, wlan1 is 2.4GHz
- a8:3e:0e:4a:94:5b Ethernet address for my Nokia cell phone
- 9c:b6:d0:93:83:d9 Ethernet address for a Dell laptop
- Is d8:49:2f:25:68:d6 trying to break into my network? We keep getting a “AP-STA-POSSIBLE-PSK-MISMATCH”
Wireless Access Log Example 3
- PSK: Pre-Shared Key, i.e., my WiFi access password
- Who is d8:49:2f:25:68:d6? Looking up Ethernet address gives Cannon Inc. as the manufacturer
- This was a “misconfigured” wireless printer, i.e., had the wrong WiFi password!
Log Software: rsyslog

Log Software: syslog-ng
