General Instructions
The goals of this assignment are getting hands on with some important networking tools and reinforce our understanding of networking from the cybersecurity perspective.
Create and Use a new Branch hw4
We will create a new git branch called hw4 for use in this assignment. The branch you create must exactly match the one I’ve given you for you to receive any credit for this homework.
Prior to creating this new branch make sure your working directory is “clean”, i.e., consistent with the last commit you did when you turned in homework 3. Follow the procedures in GitHub for Classroom Use to create the new branch, i.e., git checkout -b hw4. Review the section on submission for using push with a new branch.
Use README.md for Answers
You will modify the README.md file in your repo to contain the answers to this homework.
Questions
Question 1. (10 pts)
In this problem we are going to use the traceroute tool to try to find all the IP routers (layer 3 switches) between the department server csweb01.csueastbay.edu and a non CSUEB website of your choice. We are also going to get some location information based on IP addresses. You should have an account on the department server. To login use the command ssh csweb01.csueastbay.edu -l yourNetId@ad from a Mac or Linux terminal or from the Git bash shell in Windows. There are other programs you can also use use such as PuTTY on Windows. Your login name is yourNetId@ad (yes your NetId and those extra characters).
1(a)
Use the traceroute program on the department server to find the “hops” to a server of your choice in a foreign country, i.e., outside North America. Show the output here (as text not a screenshots). For example this is my result from kitewest.com.au (you must use a different site).
[qd7373@csweb01 ~]$ traceroute kitewest.com.au --max-hops=60
traceroute to kitewest.com.au (13.228.194.18), 60 hops max, 60 byte packets
1 gateway (172.22.36.254) 0.128 ms 0.094 ms 0.067 ms
2 100.64.80.0 (100.64.80.0) 0.241 ms 0.184 ms 0.137 ms
3 10.74.90.1 (10.74.90.1) 0.375 ms 0.354 ms 0.291 ms
4 ec2-50-112-0-56.us-west-2.compute.amazonaws.com (50.112.0.56) 14.292 ms ec2-34-221-151-87.us-west-2.compute.amazonaws.com (34.221.151.87) 1.848 ms ec2-44-233-117-33.us-west-2.compute.amazonaws.com (44.233.117.33) 2.616 ms
5 100.66.8.126 (100.66.8.126) 14.532 ms 100.65.40.32 (100.65.40.32) 2.431 ms 100.65.48.128 (100.65.48.128) 41.360 ms
6 100.66.10.226 (100.66.10.226) 13.896 ms 100.66.11.22 (100.66.11.22) 7.676 ms 100.66.20.98 (100.66.20.98) 3.167 ms
7 100.66.22.194 (100.66.22.194) 14.035 ms 100.66.26.198 (100.66.26.198) 19.116 ms 100.66.6.31 (100.66.6.31) 20.740 ms
8 100.66.5.185 (100.66.5.185) 20.357 ms 100.66.5.251 (100.66.5.251) 14.291 ms 100.66.5.113 (100.66.5.113) 16.116 ms
9 100.65.14.135 (100.65.14.135) 1.599 ms 100.65.15.137 (100.65.15.137) 1.062 ms 100.66.5.211 (100.66.5.211) 22.661 ms
10 100.95.1.23 (100.95.1.23) 1.037 ms 100.95.1.21 (100.95.1.21) 1.311 ms 100.95.17.5 (100.95.17.5) 1.516 ms
11 100.95.17.27 (100.95.17.27) 1.527 ms 100.100.2.78 (100.100.2.78) 1.571 ms 100.100.2.46 (100.100.2.46) 1.536 ms
12 100.92.37.96 (100.92.37.96) 230.979 ms 100.92.31.176 (100.92.31.176) 230.931 ms 100.100.18.44 (100.100.18.44) 1.544 ms
13 100.92.26.24 (100.92.26.24) 230.466 ms 100.92.31.58 (100.92.31.58) 230.824 ms 100.92.37.76 (100.92.37.76) 230.736 ms
14 100.92.81.139 (100.92.81.139) 230.726 ms 100.92.82.58 (100.92.82.58) 230.726 ms 100.92.81.61 (100.92.81.61) 229.693 ms
15 100.92.29.94 (100.92.29.94) 230.386 ms 100.92.32.95 (100.92.32.95) 230.711 ms 100.92.82.141 (100.92.82.141) 230.138 ms
16 100.92.35.75 (100.92.35.75) 230.777 ms 100.92.29.86 (100.92.29.86) 230.111 ms 100.92.29.83 (100.92.29.83) 230.231 ms
17 150.222.247.134 (150.222.247.134) 229.951 ms 52.93.132.210 (52.93.132.210) 231.270 ms 100.92.29.83 (100.92.29.83) 230.089 ms
18 100.92.38.73 (100.92.38.73) 232.681 ms 100.91.185.122 (100.91.185.122) 232.657 ms 150.222.242.237 (150.222.242.237) 232.616 ms
19 150.222.242.239 (150.222.242.239) 232.564 ms 100.92.27.52 (100.92.27.52) 230.871 ms 100.91.185.39 (100.91.185.39) 232.497 ms
20 100.92.29.136 (100.92.29.136) 230.863 ms 100.91.181.40 (100.91.181.40) 229.580 ms 100.91.185.109 (100.91.185.109) 230.329 ms
21 * 100.91.55.7 (100.91.55.7) 235.650 ms 100.91.55.55 (100.91.55.55) 235.632 ms
22 150.222.247.134 (150.222.247.134) 230.403 ms 52.93.11.23 (52.93.11.23) 229.916 ms 150.222.247.140 (150.222.247.140) 230.779 ms
23 52.93.11.13 (52.93.11.13) 230.485 ms 52.93.11.1 (52.93.11.1) 232.338 ms 150.222.247.138 (150.222.247.138) 230.697 ms
24 150.222.245.4 (150.222.245.4) 230.445 ms * 150.222.245.6 (150.222.245.6) 233.901 ms
25 203.83.223.194 (203.83.223.194) 233.166 ms 52.93.8.137 (52.93.8.137) 230.156 ms 52.93.10.73 (52.93.10.73) 230.088 ms
26 150.222.3.216 (150.222.3.216) 230.060 ms 150.222.3.192 (150.222.3.192) 230.008 ms 203.83.223.17 (203.83.223.17) 229.941 ms
27 100.65.10.128 (100.65.10.128) 241.320 ms 100.66.4.64 (100.66.4.64) 733.025 ms 52.93.8.40 (52.93.8.40) 230.506 ms
28 * * 100.66.4.236 (100.66.4.236) 448.262 ms
29 100.66.14.219 (100.66.14.219) 231.000 ms 150.222.3.237 (150.222.3.237) 230.368 ms 100.66.11.135 (100.66.11.135) 249.365 ms
30 100.66.8.57 (100.66.8.57) 244.062 ms 100.66.11.5 (100.66.11.5) 245.634 ms 100.66.12.59 (100.66.12.59) 232.651 ms
31 * 100.66.8.243 (100.66.8.243) 250.946 ms *
32 100.65.19.33 (100.65.19.33) 230.293 ms 100.66.4.24 (100.66.4.24) 250.523 ms 100.65.9.192 (100.65.9.192) 256.581 ms
33 100.66.7.224 (100.66.7.224) 248.133 ms * *
34 100.66.11.65 (100.66.11.65) 244.093 ms 100.66.10.175 (100.66.10.175) 432.194 ms 100.66.6.32 (100.66.6.32) 244.561 ms
35 * 100.66.10.217 (100.66.10.217) 252.135 ms *
36 * 100.65.24.65 (100.65.24.65) 231.678 ms *
37 100.65.25.129 (100.65.25.129) 232.367 ms * *
38 * * *
39 * * *1(b)
Read the traceroute documentation by typing the command man traceroute in the terminal. How does traceroute fundamentally work, that is, what IP packet level feature does it “abuse”?
1(c)
Go to the MaxMind demo page and see how well they can locate you. Take a screenshot and show it here. I get something like:
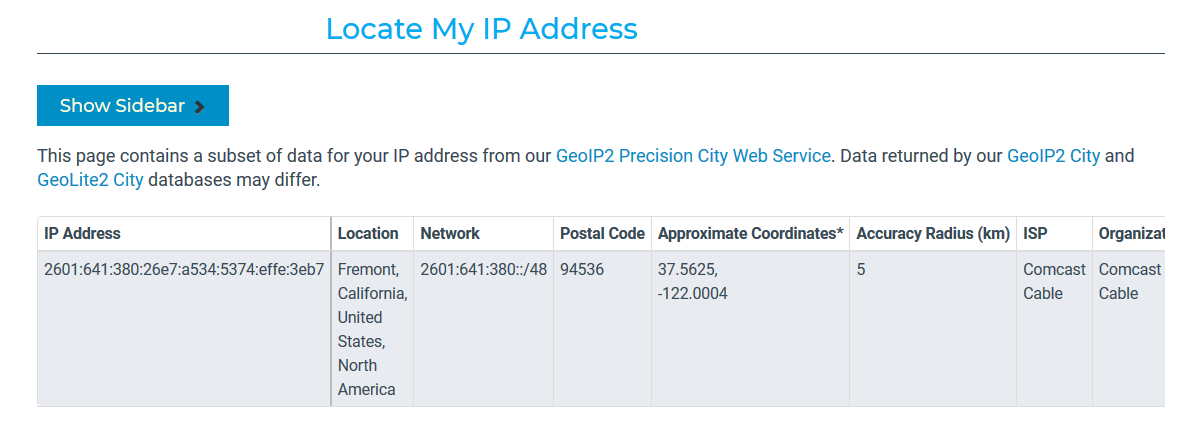
1(d)
Extract a few of the IP addresses from part (a) that are not in the range 100.64.0.0 - 100.127.255.255 (as these are special addresses used by ISPs and will not have location information) and enter them into MaxMind demo to get location information and show it here. Not all IP addresses will have information. I get information such as:
hop 3, ip=50.112.0.56: US Oregon, OR, Boardman, 97818, 45.8491, -119.7143
hop 16, ip=150.222.247.134: US None, None, None, None, 37.751, -97.822
hop 22, ip=52.93.11.13: SG None, None, Singapore, 18, 1.2929, 103.85471(e) Security Implications
As we learned modern networking is made possible by the concept of “multiplexing” (and switching). As you should have seen above, a packet can traverse many hops (switches)to get to its destination. What are the security implications of this with respect to the CIA triangle (relatively short answer, i.e., two to four sentences).
Question 2. (10 pts)
Wireshark, Ethernet, ARP, and IP
2(a)
Install Wireshark on a machine that you can use. Start the program and go to the “Capture/Options” screen. This will list the various network interfaces on your machine. Click to show more information about an active external (not loopback) interface. Take a screenshot and write down the IPv4 address of one of your active local interfaces.
I get something like (so my WiFi interfaces IPv4 address is 192.168.1.228)
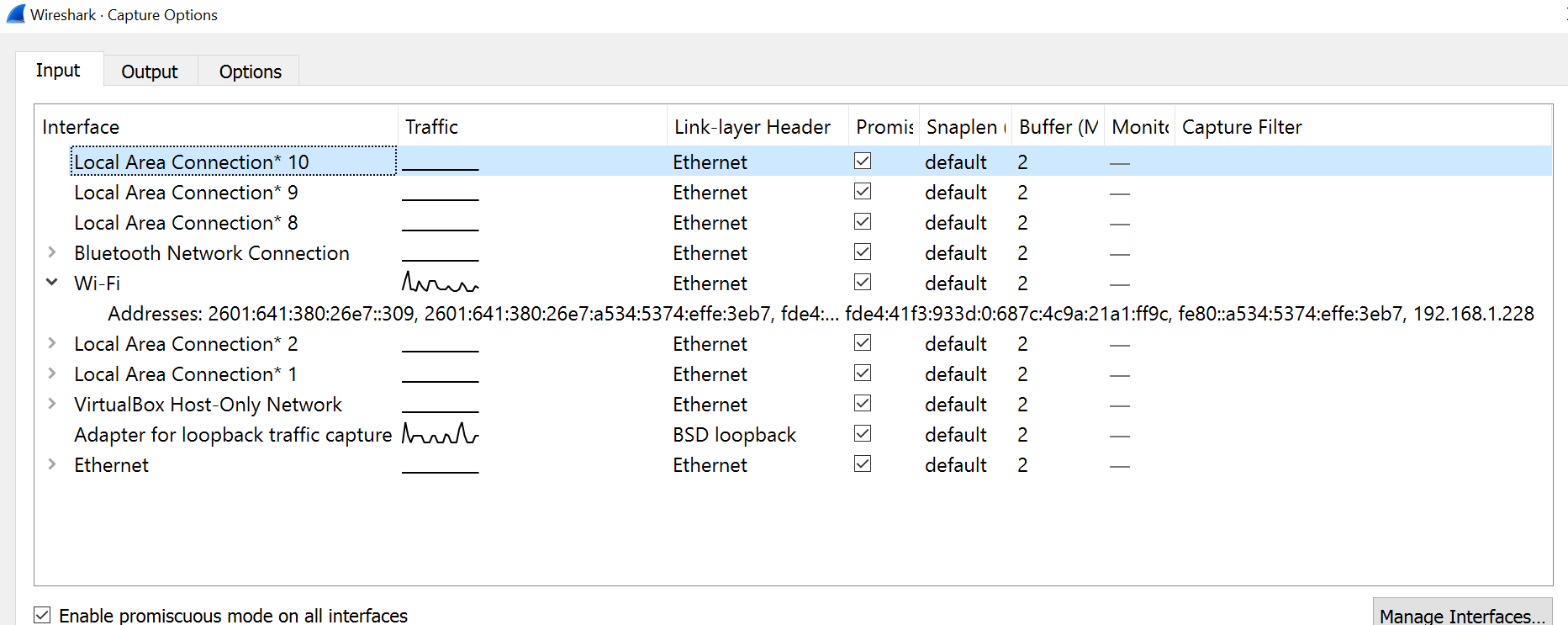
2(b) General Capture
Now perform a “capture” on that active interface. Run it long enough to capture at least 2000 packets. Use your web browser and other net enabled applications to generate traffic if needed. Save the captured packets to a file. Show a screenshot showing the last packets captured. How many packets did you capture and how long did the capture last? (answer here) How large is your capture file (answer here)?
My screenshot looks something like
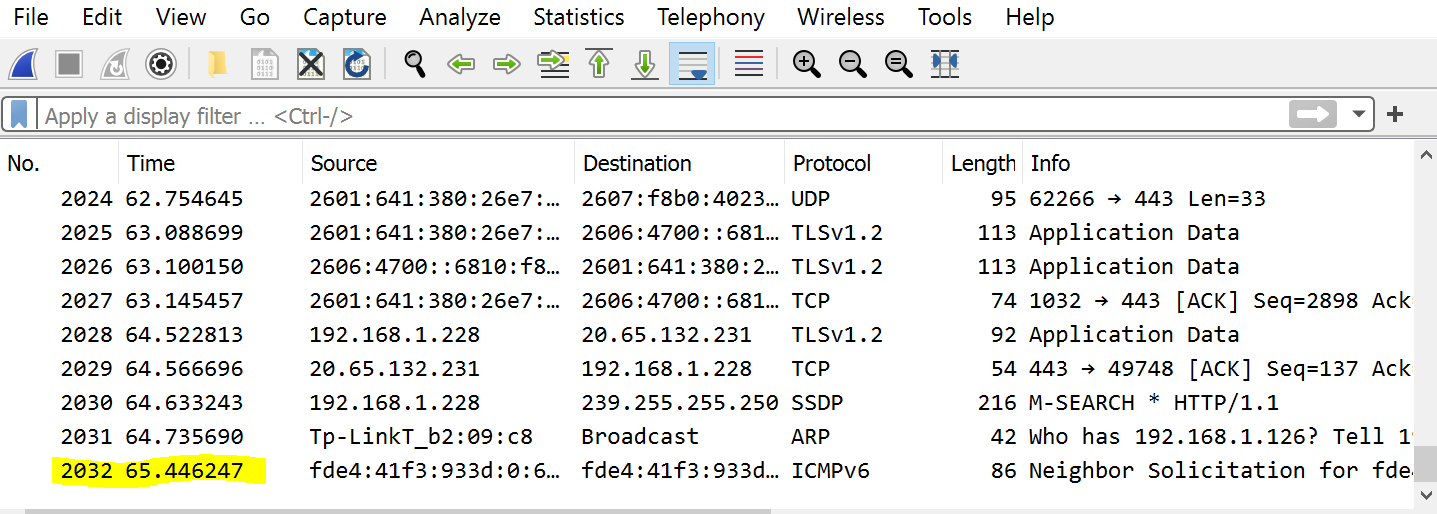
so I captured 2032 packets over 65 seconds approximately. My capture file size was about 1.5MB.
2(c) Ethernet
Now select a packet from the list in Wireshark that originates from your IPv4 address in part (a). Open up the Ethernet information about the packet and show a screenshot here. Write down the source and destination Ethernet addresses here. Did Wireshark figure out the manufacturer of your computers Ethernet interface? How?
My screenshot looks like:
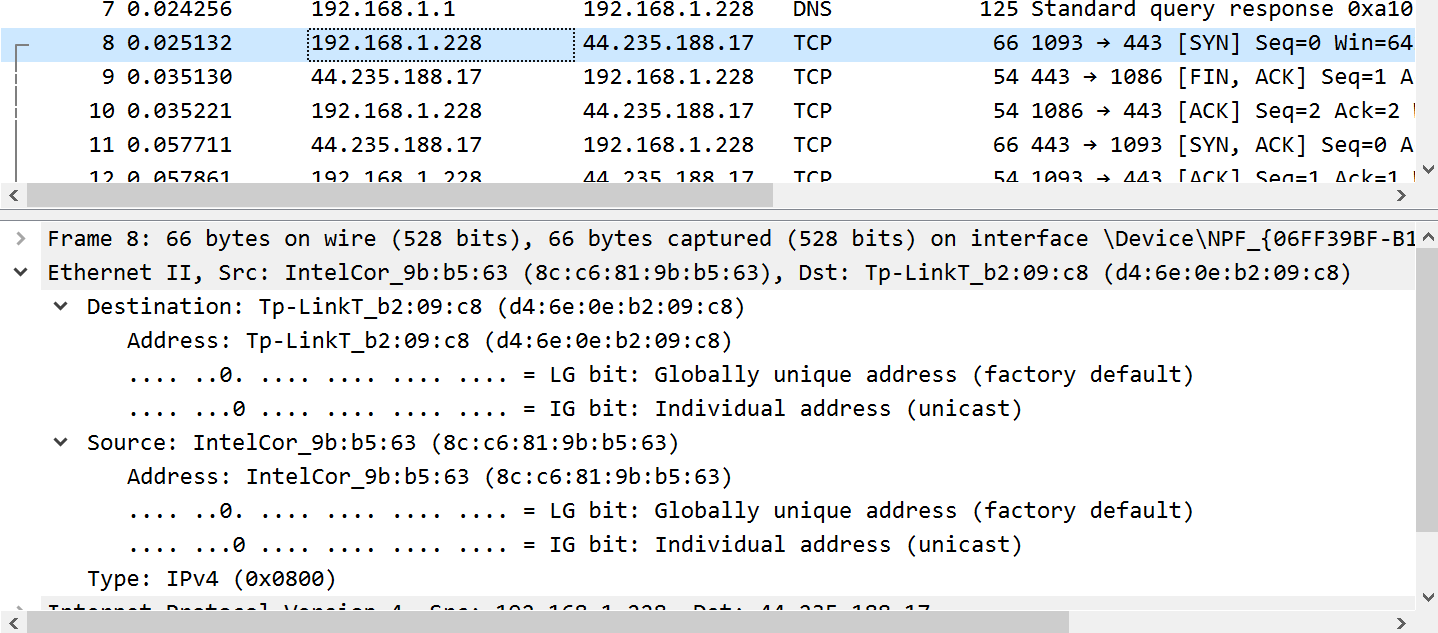
My Ethernet address is 8c:c6:81:9b:b5:63 and Wireshark figured out my interface was made by Intel and was sending to an interface made by TP-Link.
2(d) ARP and Neighbor Discovery
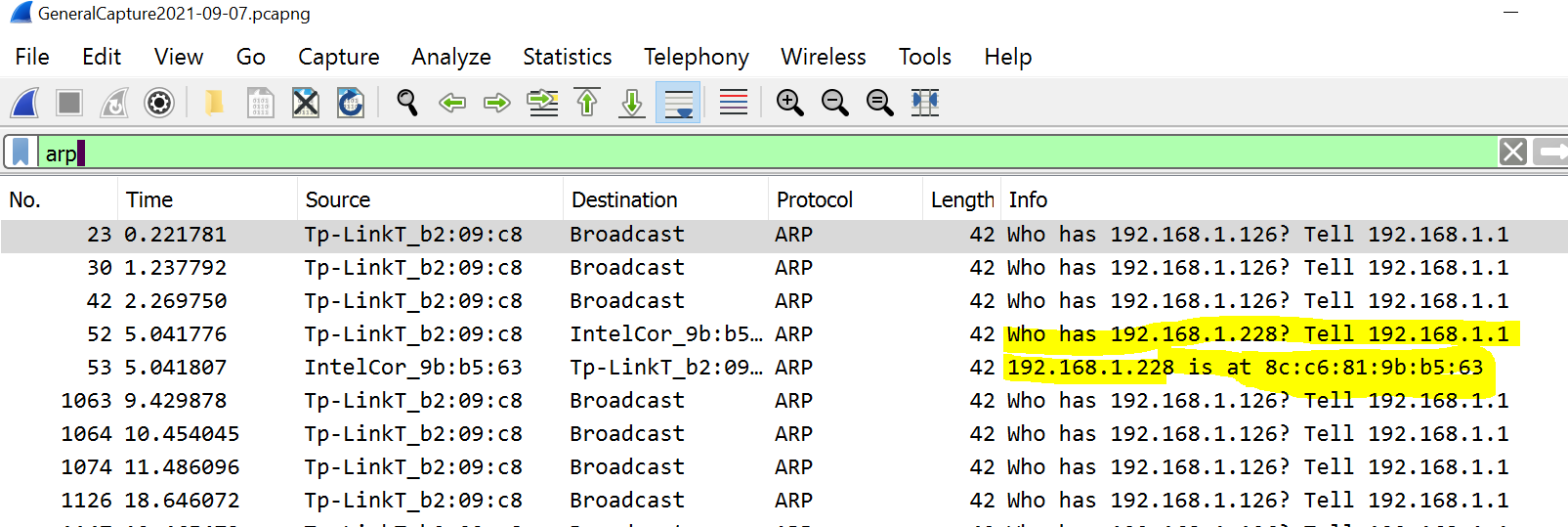
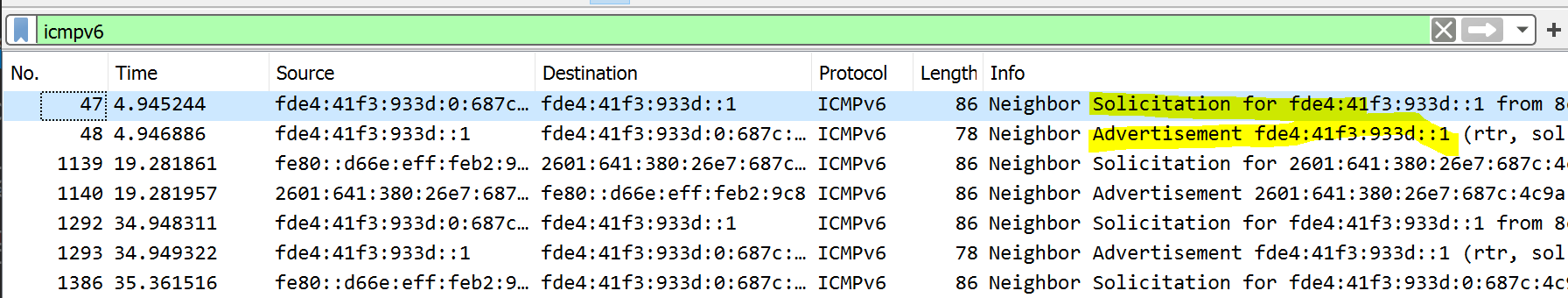
In IPv4 the ARP protocol associates IPv4 addresses with Ethernet addresses. In IPv6 ICMPv6 packets help do this job. Instead of scrolling through 2000 packets or more use a “display” filter of either arp or icmpv6 in Wireshark to just show these types of packets. Take a screenshot of either ARP or ICMPv6 packets only. Give a brief explanation (a sentence or two) of what is happening here.
My screenshot for ARP looks like:
My screenshot for ICMPv6 looks like (you only have to show one or the other):
2(d) IP versus Ethernet
If Ethernet packets (frames) contain both source and destination Ethernet addresses why do we need to bother with IP at all? In particular the extra stuff in the IP packet header (the part in addition to the data) just takes up space and wastes network bandwidth. (give your answer in a sentence or two)
Question 3. (10 pts)
Capturing and storing all the traffic seen on a particular interface can take up a lot of space. Wireshark supports capture filtering in addition to the display filtering that we have already used. See Filtering while capturing.
3(a) UDP only capture
Set up Wireshark to only capture UDP packets. Do some network activities so that you capture some packets. Take a screenshot and show it here. If we are doing “UDP” only capture why might Wireshark show other protocols in addition to UDP (short answer here)? For example I get:
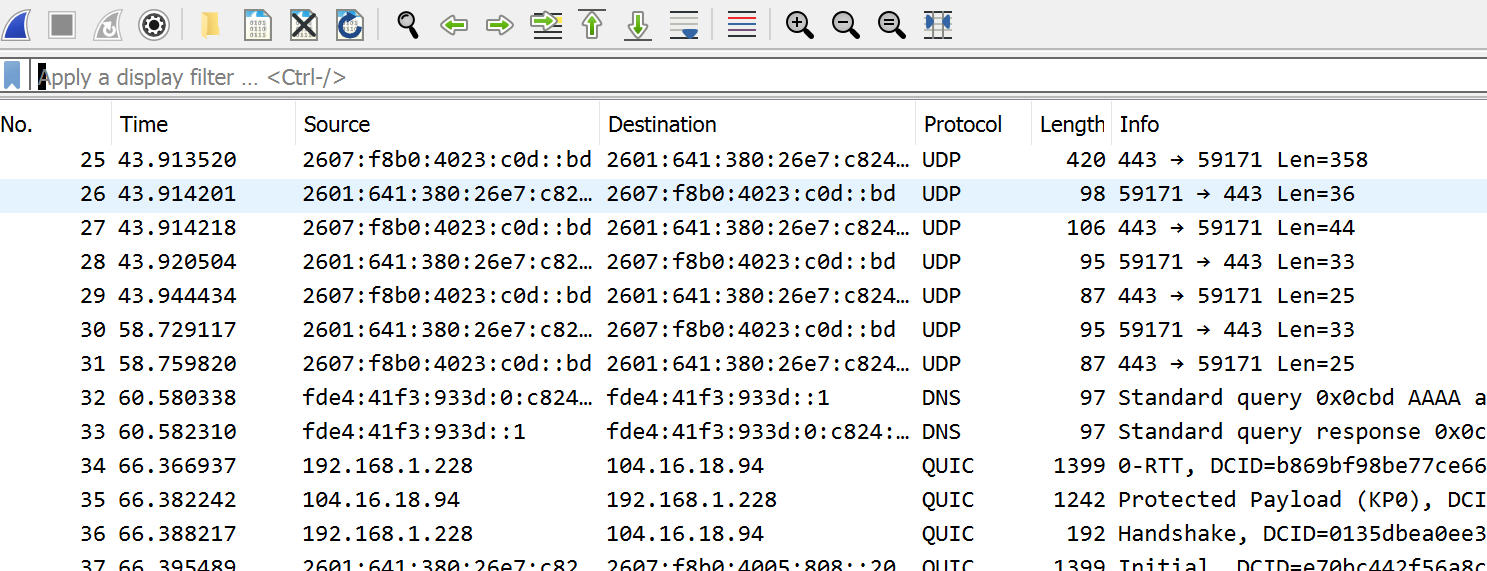 .
.
3(b) TCP only capture
Set up Wireshark to only capture TCP packets. Do some network activities with your browser or other network apps. You are now going to find an example of the “TCP three-way handshake”. See, for example: TCP Three-way handshake. You can use the Wireshark display filter tcp.flags.syn==1 to help you find these but you will want to turn off this filter to show the full three-way handshake. Take a screenshot of the packets involved in the three-way handshake and show it here. If you can highlight the three packets.
I get something like:
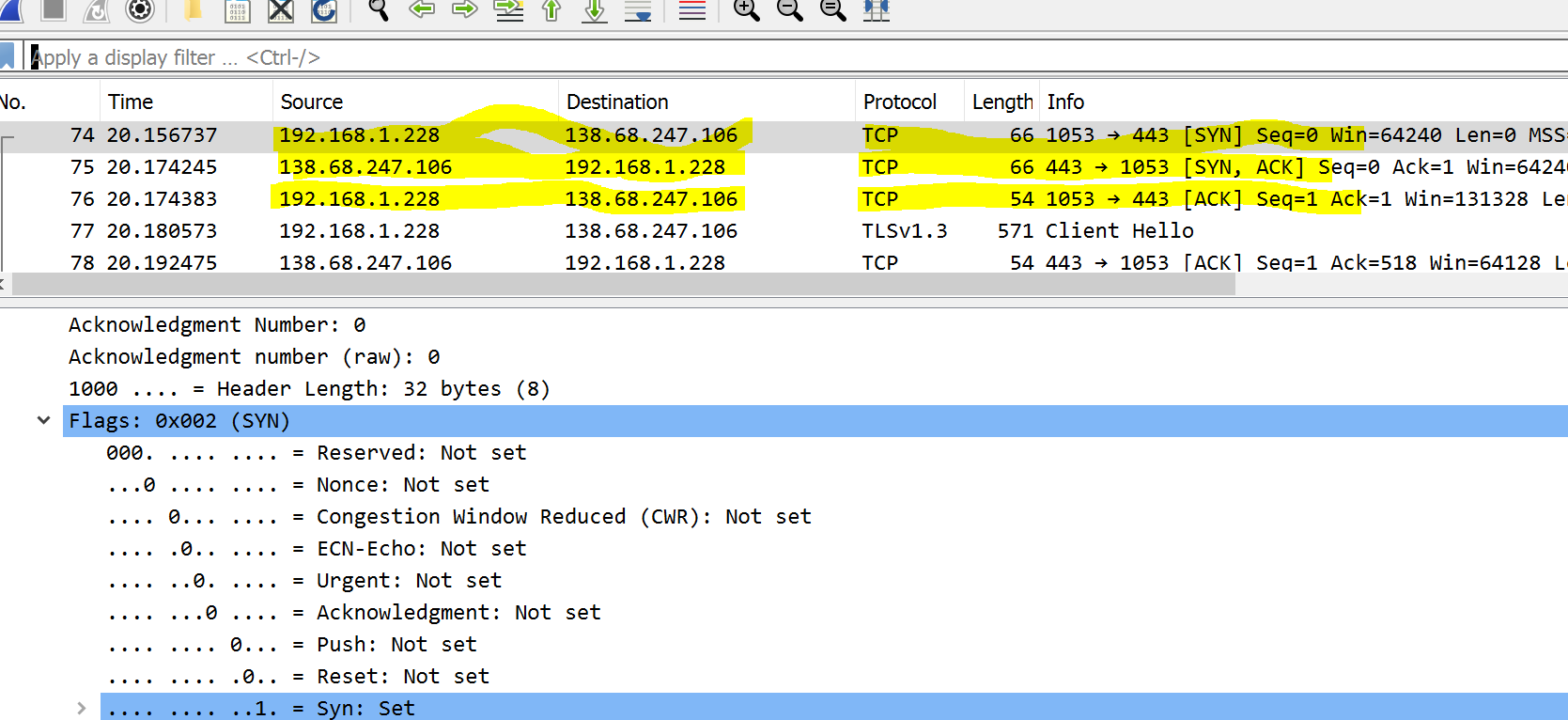
3(c) Why Ports
Under which situation must we use both source and destination UDP/TCP ports? Why? (provide a sentence or two)
Always, can’t tell packets apart otherwise
When two different computers talk to a process on a computer listening on a specific destination port
When two different processes on the same computer need to talk to a process on another computer listening on a specific destination port
Never, ports are over rated
3(d) TCP versus UDP
What functions does TCP offer beyond those provided by UDP? (a sentence or two in your own words)
Question 4. (20 pts)
In this problem you are going to learn how DNS works and understand one type of attack on DNS. Start by reading sections 1. Function, 3. Structure, and 4. Operation from the Wikipedia: DNS article. We will also use the Wikipedia: DNS Record Types as a reference.
4(a)
Now lets see the address resolution mechanism discussed in Wikipedia: Address resolution for either my site or a site of your choosing. To do this we are going to use the Linux tool dig with the trace option. See the article DNS resolution tracing. Login to the department server and run dig +trace to a domain of your choosing. Note you can do this from any Linux machine you like. Show your output here. I get the following (you need to pick a different domain!).
greg@greg-desktop:~$ dig +trace @8.8.8.8 classroom.grotto-networking.com
; <<>> DiG 9.16.1-Ubuntu <<>> +trace @8.8.8.8 classroom.grotto-networking.com
; (1 server found)
;; global options: +cmd
. 66341 IN NS a.root-servers.net.
. 66341 IN NS b.root-servers.net.
. 66341 IN NS c.root-servers.net.
. 66341 IN NS d.root-servers.net.
. 66341 IN NS e.root-servers.net.
. 66341 IN NS f.root-servers.net.
. 66341 IN NS g.root-servers.net.
. 66341 IN NS h.root-servers.net.
. 66341 IN NS i.root-servers.net.
. 66341 IN NS j.root-servers.net.
. 66341 IN NS k.root-servers.net.
. 66341 IN NS l.root-servers.net.
. 66341 IN NS m.root-servers.net.
. 66341 IN RRSIG NS 8 0 518400 20210214170000 20210201160000 42351 . cNctac4tDPXhsemoAC/TY7ZI4LsBNt4ms0xcky9DJNeA6RD1RPyBABAC JPNDlsEO1xgpUUHWOAO/2wTgXv4tD/lK2kO4HrCajJqd7YccU3ac7zVQ kKdinLEHPoblvPCLGD5FO+h9XgYmh4ksAGQneGFH9ECsTacnTwz4GfvH ZhB7mtCk4/WjljUwMN3jQVGguu30Wwuny3Rm5KO4DTEwqt+st+sxVtHk q3gm6ikmk8dpmcAA/jbU39Mrx/C3UNVoV2j1M+fBhV7aOqi51gQGdVA4 UbzGrI3wwMyUyy8G17cbhADxgnh+W2Z9zHaexyYyaZyHC7t6pHrB8jgz Prm4KQ==
;; Received 525 bytes from 8.8.8.8#53(8.8.8.8) in 9 ms
com. 172800 IN NS c.gtld-servers.net.
com. 172800 IN NS l.gtld-servers.net.
com. 172800 IN NS m.gtld-servers.net.
com. 172800 IN NS e.gtld-servers.net.
com. 172800 IN NS g.gtld-servers.net.
com. 172800 IN NS a.gtld-servers.net.
com. 172800 IN NS k.gtld-servers.net.
com. 172800 IN NS d.gtld-servers.net.
com. 172800 IN NS j.gtld-servers.net.
com. 172800 IN NS b.gtld-servers.net.
com. 172800 IN NS h.gtld-servers.net.
com. 172800 IN NS i.gtld-servers.net.
com. 172800 IN NS f.gtld-servers.net.
com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766
com. 86400 IN RRSIG DS 8 1 86400 20210214220000 20210201210000 42351 . MpHua4R3FiyaE9yATh6wl2x4w+6J423Q5eapWeDlBhSjvxBQ3h+GxC5Z irme97RpPOxuij5IKjopAgfKh3oh5FAqxSro6ZB+7CIDmIJs6KzWo3mf iePLnOAjDgeBlEgyegE6JTPFJUtJHrzp7ChxPBTAJf4P08Unz1v0HaB9 JFlGh0KJoqymReXd6F7+yz4GuL9Pr85yH5Wa3qyGa0VmGveO6J7xYEWJ TryFqzU0Qe6Sm8npYtjQbq0wp3zzhb+T4c5YLJnql/o55kGhJNH2uTRn F+EzR6nKBHgQVCOBOVO2oLlc2NzILQNYTpQH282x5thsKHaaHuLBw8tM O9QeLw==
;; Received 1191 bytes from 2001:dc3::35#53(m.root-servers.net) in 15 ms
grotto-networking.com. 172800 IN NS ns1.digitalocean.com.
grotto-networking.com. 172800 IN NS ns2.digitalocean.com.
grotto-networking.com. 172800 IN NS ns3.digitalocean.com.
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q1GIN43N1ARRC9OSM6QPQR81H5M9A NS SOA RRSIG DNSKEY NSEC3PARAM
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20210205054045 20210129043045 58540 com. EH5YllUVHii00WmEGefJmO4b3orus0uDJ5fgR9v0DJ+HJHT8VcAx0a/b mRuKolppJoeUb6AfsgSX662TS3X7e+wIsGiEj6ejSuMJ09HF++F72LJM vR2SeUxTsZKhQUVgLtoJkqrmy98jC4LZvExthVNj5yYD70a3Ns/Qf3SL ata0PRkKXKVNkUAF9w7S3FfAhV1dx7glwst7uOwbbGwrKA==
0BHSA5082JTUJE4JIPEQ8FH3LFJK2CM1.com. 86400 IN NSEC3 1 1 0 - 0BHT06MAEARNC3D1ODDOGDQUE9NH9ETH NS DS RRSIG
0BHSA5082JTUJE4JIPEQ8FH3LFJK2CM1.com. 86400 IN RRSIG NSEC3 8 2 86400 20210207075336 20210131064336 58540 com. JkzcmOlBHzNx19Z41y0E4JX50Ovq7IhCRLNkIn0ZS9Yko7scLQZpoFi2 D3RfT0EUflBXz7IiW9I3pj+gRBZaWZW0QxTl/B+9gyNPE9cHfS/2v1FC H7FUBQ2/6hYT8dIbM7D9Z+eLEdOkRvKq7BXXyZJkwrFxxJweVJSZ2/eh SvrRztTgoAmqZxIPOWmycmNAiuA51GOeAuklgo5a6Enifw==
;; Received 808 bytes from 2001:502:8cc::30#53(h.gtld-servers.net) in 11 ms
classroom.grotto-networking.com. 3600 IN A 138.68.247.106
;; Received 76 bytes from 173.245.58.51#53(ns1.digitalocean.com) in 16 ms4(b)
What are the IP addresses (and domain names if available) of the name servers involved in resolving the domain you looked up in part (a)? A more in depth walk through of DNS resolution can be found here (which will also teach us about DNS attacks).
4(c)
My listing in part (a) shows several different DNS record types. What are the NS, DS, RRSIG, and A records for?
4(d)
Now review the more detailed explanation of DNS resolution in DNS vulnerability. Answer the following. Why does DNS servers use caches? Is the DNS time to live information the same as the time to live information we see in the IP packet header? What units are they measured in?
4(e)
From Cache poisoning, what is the difference between DNS cache poisoning and phishing? Which seems more dangerous?