General Instructions
The goal of this homework is to get an idea of the types of data and systems that we want to protect and the fundamental security concepts in the CIA triangle.
In addition we will get hands on with URL parameters and URL shorteners and see how these can be used for good or evil.
Create and Use a new Branch hw2
We will create a new git branch called hw2 for use in this assignment. The branch you create must exactly match the one I’ve given you for you to receive any credit for this homework.
Prior to creating this new branch make sure your working directory is “clean”, i.e., consistent with the last commit you did when you turned in homework 1. Follow the procedures in GitHub for Classroom Use to create the new branch, i.e., git checkout -b hw2. Review the section on submission for using push with a new branch.
Use README.md for Answers
You will modify the README.md file in your repo to contain the answers to this homework.
Questions
Question 1. (10 pts)
URLs and URL shorteners
1(a) URLs and their parts
To understand how phishing and other web scams work you need and understanding of URLs. The website MDN URLs provides a great overview and details. For the following URLs specify the requested parts:
http://www.notFishing.biz/yourBank/ha.html, Scheme/protocol, domain name, pathhttps://www.notReallyFishing.biz:8081/yourMail/ha.html, Scheme/protocol, domain name, porthttps://www.spearFishing.biz:8081/yourCloud?name=GotYou&when=now, Scheme/protocol, domain name, path, parametershttps://www.bulk.biz:8181/yourFriend?name=GotYou&when=now#HereWeAre, Scheme/protocol, domain name, parameters, anchor/segment
1(b) HTTPS Certificates and URLs
To set up a phishing site the “bad actors” will need a domain name for their site. Domain names need to be registered with an “authority” Wikipedia: Domain name registration. What can be done about this? See the the Anti-Phishing Working Group (APWG) Ecrime exchange. (Short answer, i.e., a sentence).
HTTPS certificates are bound to domain names and require a bit of extra effort to obtain. Why would a phishing site want to use HTTPS over HTTP which doesn’t require a certificate? (Short answer, i.e., a sentence).
1(c) Identifying the Target
Given what you learned in the previous sections what parts of a URL could a phisher use to encode identifying information about a target? (short answer, list of appropriate URL parts)
1(d) Encode Your Name and a random color in a URL
Let’s encode via “query parameters” your first and last name in a URL along with a random color of your choice from the list of CSS color names. Then we will run that URL through a URL shortening service of your choice, e.g., bitly.
We are going to visit a site I created at https://cs671.grotto-networking.com. We will specify first, last, and color parameters. For me choosing the color name aqua I would end up with the long URL: https://cs671.grotto-networking.com/?first=Greg&last=Bernstein&color=aqua. Using a URL shortening service I get the link https://bit.ly/35dWj50 which completely hides my name and color information.
Show the long URL with your name and color information here. (Needs to be a clickable link)
Show the shortened URL you got from a shortener service here. (Needs to be a clickable link)
1(e) Screen Shot
Take a screenshot of the page at cs671.grotto-networking.com after you have visited it with your URL. With my link/URL I get:
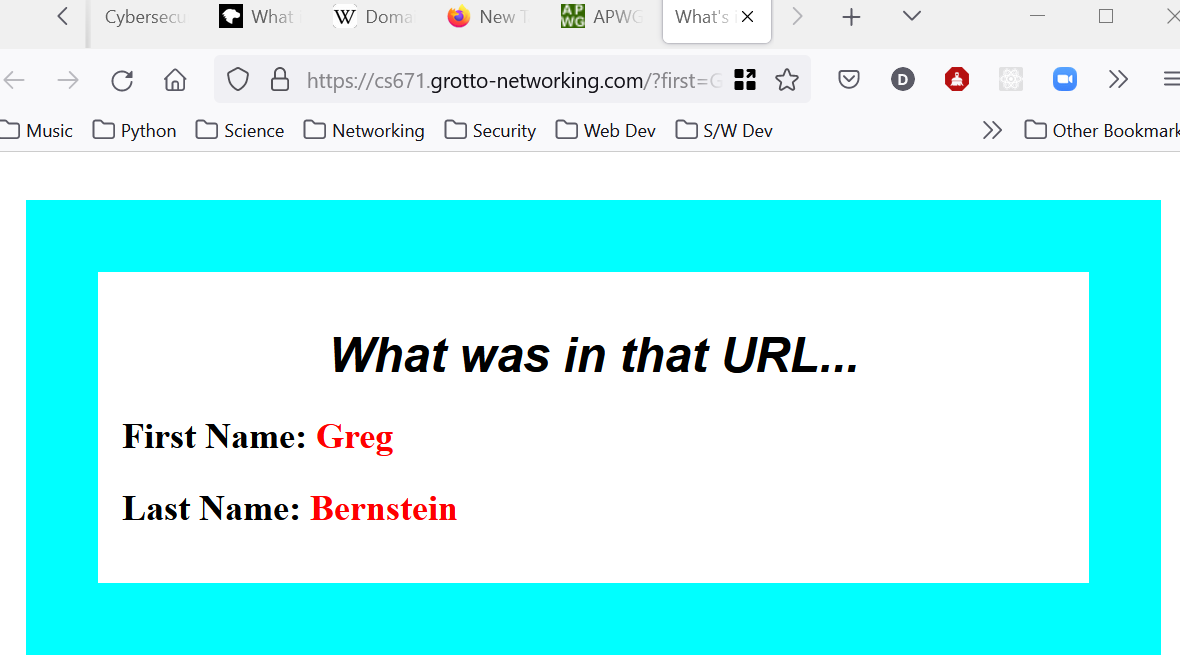
Question 2. (10 pts)
2(a)
Did the slides on Data and Systems show an example of your mobile device being a target? If so reference the attack here. If not explain why not, and indicate your mobile device and operating system here.
2(b)
Compare the classic “need to know” discussed in the slides concerning military classified information with the relatively modern security principle of least privilege. (short answer, i.e., sentence)
If you visit a doctor for a checkup do you think that doctor should have access to your homework scores in this class since the doctor has access to your sensitive health data? How does this relate to “need to know” or “least privilege”? (short answer, i.e., sentence)
2(c)
Read the description of the Fair Credit Reporting Act at the US FTC. Which parts of the CIA triangle is this act primarily concerned with? (short answer, i.e., sentence)
2(d)
Read the description of the Fair and Accurate Credit Transactions Act of 2003 (FACTA) at the US FTC (FACTA). Which part of the CIA triangle would you say this is most concerned with (pick one) and why? (short answer, i.e., sentence)
Question 3. (10 pts)
3(a)
What are some of the reasons IOT devices might be harder to protect from a cybersecurity point of view? (short answer, i.e., sentence)
3(b)
Why might an attacker prefer to gain access to a server as opposed to a laptop? (short answer, i.e., sentence)
3(c)
Why might an attacker target a “gaming machine” with a powerful GPU? (short answer, i.e., sentence)
Question 4. (10 pts)
4(a)
What are the five security functions for critical infrastructure (see slides)? Do you think these are applicable to your systems and data?
4(b)
A data breach is an loss or attack on what part of the CIA triangle?
4(c)
There is an amazingly cute known as as Slow Loris (Wikipedia), much less cute is the slow loris HTTP attack. What part of the CIA triangle is this attack aimed at? (also provide a short explanation, i.e. one sentence).
Question 5. (10 pts)
5(a)
Phishing (email) starts with a loss or attack on which part of the CIA triangle? If that initial attack is successful what parts of the CIA triangle might be attacked next? (explain in one to two sentences).
5(b)
In politics and business there is a concept known as plausible deniability (wikipedia). This represents an attack on which part of the CIA triangle? In particular which sub-category does this attack and why?
5(c)
Cosmic rays (wikipedia) are capable of flipping bits in computer memory. A well documented recent case caught the attention of the gaming world Cosmic Ray Flips Bit, Assists Mario 64 Speedrunner. What parts of the CIA triangle are these evil cosmic rays attacking? Explain. Note: cosmic rays aren’t really evil they are just atomic nuclei and neutrons.