General Instructions
The goals of this assignment are to get more familiar with cybersecurity principles, work with security controls and architectures, and get an understanding of VPNs.
Create and Use a new Branch hw12
We will create a new git branch called 12 for use in this assignment. The branch you create must exactly match the one I’ve given you for you to receive any credit for this homework.
Prior to creating this new branch make sure your working directory is “clean”, i.e., consistent with the last commit you did when you turned in homework 11. Follow the procedures in GitHub for Classroom Use to create the new branch, i.e., git checkout -b hw12. Review the section on submission for using push with a new branch.
Use README.md for Answers
You will modify the README.md file in your repo to contain the answers to this homework.
Questions
Question 1. (10 pts) NIST Principles Continued
(a) NIST Principle of Accountability and Traceability
What is the NIST principle of accountability and traceability? See NIST SP800-160v1 appendix F. Use your own words.
(b) NIST Defense in Depth
What is NIST’s definition of defense in depth in your own words. See NIST SP800-160v1 appendix F.
(c) NIST Secure Defaults
See NIST SP800-160v1 appendix F item F.2.5 Secure Defaults. Is NIST’s Secure Defaults principle the same as Salzburg and Schroeder’s “Fail Safe Defaults”? If they are different, explain how they are different? Why might a device or operating system not “ship” with secure defaults?
Question 2. (10 pts)
NIST Controls: for this question you will need to refer to NIST SP 800-53 Rev. 5 Security and Privacy Controls for Information Systems and Organizations.
(a) NIST Control PS-3
Explain the NIST control PS-3 in your own words for use in a commercial organization. Would this control typically be implemented in software? Explain.
(b) NIST Control SR-3(1)
Explain the NIST control SR-3(1) in your own words. Would this control typically be implemented in software? Explain. What part of the CIA triad is this control aimed at protecting?
(c) NIST Control AU-12
Explain the NIST control AU-12 in your own words. Would this control typically be implemented in software? Explain.
(d) NIST Control AC-2(5)
Explain the NIST control AC-2(5) in your own words. Would this control typically be implemented in software? Explain. Which general systems (don’t put down specifics) that you use frequently implement this control?
Question 3. (10 pts)
CIS Controls: for this question you will need to refer to the CIS Controls and to the more detailed PDF document available for free with registration. When asked a question about home consider you and your home a small business/enterprise. Use version 8 of the CIS controls.
(a) Defending Against and Recovery from Ransomware
You are the first dedicated cybersecurity employee at a growing business. Which of the 18 CIS controls would you specifically recommend to protect against ransomware attacks? Explain your top four choices to justify the time and expense to the other company executives.
(b) Controls and Principles
What are CIS control safeguards 12.4 and 12.8? Explain what principle corresponds to these controls? What type(s) of organization would implement these controls?
(c) Home Data Defense
Which of the CIS Control 11: Data Recovery safeguards should you implement for your home (by their recommendations)? Have you implemented any of these? Explain.
Question 4. (10 pts) IDS and Architecture
(a) Terminology
What do the following acronyms mean?:
- IDS
- IPS
- NIDS
- HIDS
(b) Packet Capture
The Suricata IDS/IPS system has a large set of features listed at Suricata: All Features. Does the system support many types of packet capture? If so list a few types that they support. Why is this important in an IDS/IPS system?
(c) Protocol Parsing
The Suricata IDS/IPS system has a large set of features listed at Suricata: All Features. Why does it need so many protocol parsers? Why would new protocol parsers need to be developed? What language do they use for this development? Why?
(d) Zero Trust Architecture
Answer the following questions:
- What is perimeter based security?
- What is “Lateral Movement”?
- What is the fundamental premise of “zero trust models”?
Question 5. (10 pts) VPNs and Tor
(a) VPN Features
What features might a modern VPN provide? How and where might a VPN be used?
(b) VPNs: confidentiality and integrity
Do WireGuard or OpenVPN provide for confidentiality or integrity? If so how?
(c) VPNs and Anonymity
Do OpenVPN or WireGuard provide anonymity? What about NordVPN. Can/should you trust an anonymous VPN provider?
(d) TOR and Anonymity
Can TOR provide anonymity to users of services? What about to servers themselves? Can TOR protect you from fingerprinting. Visit Cover Your Tracks run the test against your browser and take a screenshot of the overall results. I got something like:
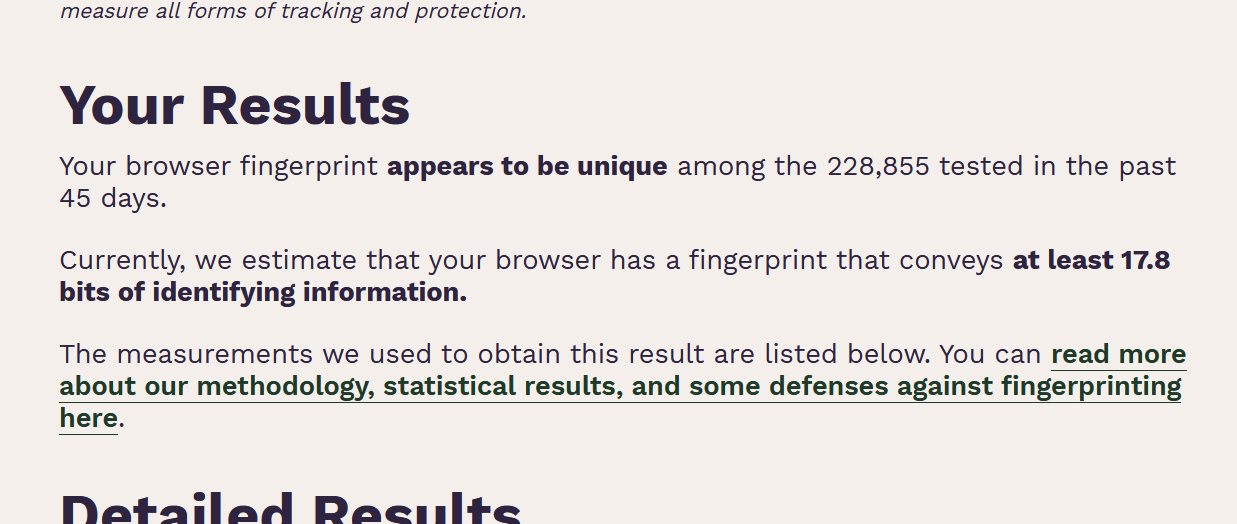 .
.
What fingerprinting technique revealed the most “bits” of information about your system?