General Instructions
The goals of this assignment are to get more familiar with TTPs, vulnerabilities, get hands on with network reconnaissance, and start on cybersecurity principles.
Create and Use a new Branch hw11
We will create a new git branch called hw11 for use in this assignment. The branch you create must exactly match the one I’ve given you for you to receive any credit for this homework.
Prior to creating this new branch make sure your working directory is “clean”, i.e., consistent with the last commit you did when you turned in homework 10. Follow the procedures in GitHub for Classroom Use to create the new branch, i.e., git checkout -b hw11. Review the section on submission for using push with a new branch.
Use README.md for Answers
You will modify the README.md file in your repo to contain the answers to this homework.
Questions
Question 1. (10 pts) TTPs
Understanding TTPs via the Mitre ATT&CK model. Below are three different attack analysis written up by Talos Intelligence. You will read one of these based on the last digit of your NetId
- Masslogger – digits 1-3
- Xanthe Miner – digits 4-6
- Wasted Locker – dgits 7-9
(a) Mitre ATT&CK Items
List the identifiers of the Mitre ATT&CK technique mentioned in the article, i.e., an identifier like: “T1059.003”, or “T1059”. You do not need to explain them here.
(b) Mitre ATT&CK Techniques Explanation
For four of the techniques you listed about provide an explanation of that technique in a way understandable to someone who is taking this class and not a security, windows, Mac, or Linux expert. If the reader cannot understand your explanation you will lose points.
Question 2. (10 pts) CVE and NVD
(a) CVE
Go to the CVE list search page and search for dnsmasq which is a library commonly used in home routers. Show a screenshot of a portion (first couple) of results. Review the first four or so returns. List the “the highest threat from this vulnerability” for each of the first four CVE you found here. In these first four CVEs did you see any mention of an attack that we studied in class? If so what was that attack?
(b) NVD
For one of the CVEs you found in part (a) look up that item in the NIST NVD, see NVD Search page. Show a screenshot of what you see. Show the severity score here. Show the common weakness enumeration here.
Question 3. (10 pts) NMAP Basics
For this question you will need to download NMap and install it on your machine.
(a) Show NMap Running
Take a screenshot of NMap running on your machine, either a GUI version or in a terminal. I show both below:
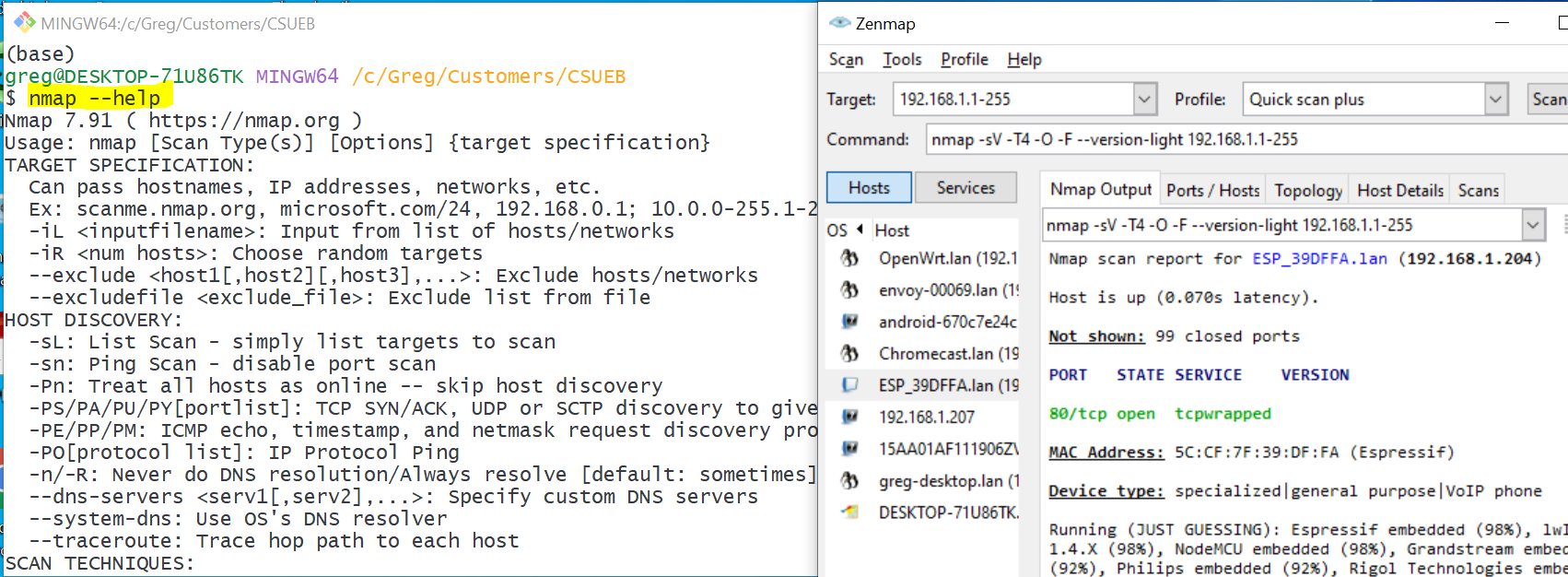
(b) Find the IPv4 Address and Type of your Machine
Different operating systems have different commands to determine the IP address of your machine. In addition a machine can have multiple IP addresses for different purposes. Find the IPv4 address of your machine that is used for communicating with local network. Write that address here. For example my laptop has the address 192.168.1.228.
Is your IPv4 address a Private IPv4 address? For example my address is in the range 192.168.0.0 – 192.168.255.255 so is a private IPv4 address. Write your answer here.
Question 4. (10 pts) NMAP Scans
(a) Quick Scan your own machine
Use either the NMap GUI or the command nmap -T4 -F your_ip_address to scan your own machine from your machine. Take a screenshot. I get:
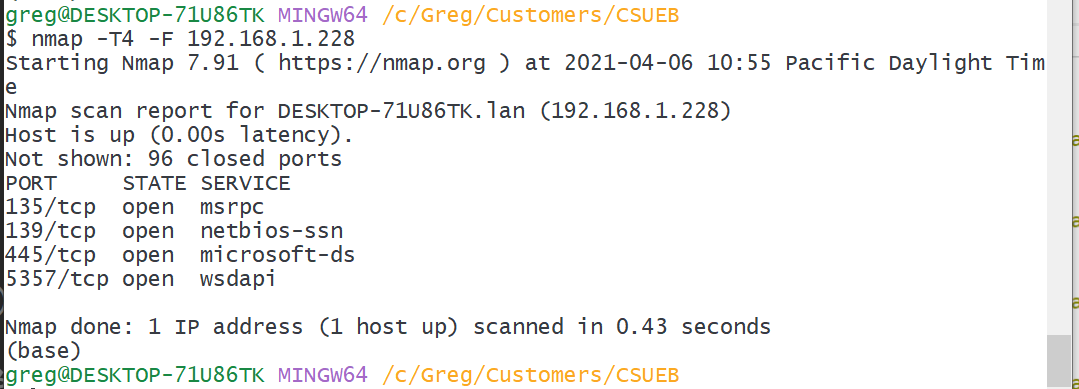
How many open ports did NMap find on your machine? (answer here)
(b) Scan your cell phone
Find the IPv4 address of your cell phone and write it here. You need your cell and computer to be on the same WiFi network for this to work. For example my cell has IP address: 192.168.1.207 on my local network.
Scan your cell phone with an “intense scan” (GUI) or command nmap -T4 -A -v your_ip_address. Take a screenshot of the results. How many open ports did NMap find? Did NMap correctly identify the device/operating system? Can you get device manufacturing information from the MAC address?
I get:
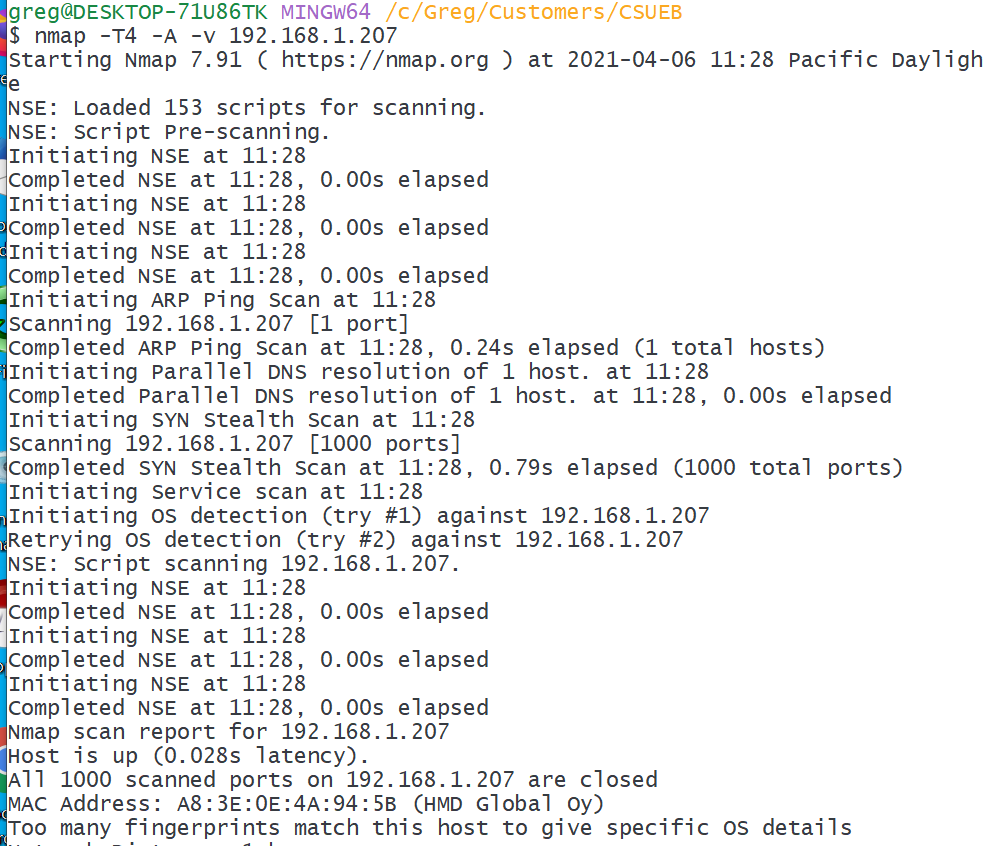
(c) Scan another device or subnetwork
Scan another device on your network or scan for devices on a subnetwork. Please respect others privacy and do not scan devices or networks without permission. Describe what you scanned and how well NMap identified devices here.
See an example of my home network scan and analysis in the course slides Recon: NMap Home Network.
Question 5. (10 pts)
Principles: for this problem you will may want to review the CyBOK introduction, and you will need to look up items in NIST SP 800-160 Vol. 1 Systems Security Engineering: Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems.
(a) Fail-Safe Defaults
In the context of information security and IP addresses/domain names what is “white listing”? What is “black listing”? Explain how these relate to the principle of fail-safe defaults.
(b) Separation of Privilege
Give an example of separation of privilege different from those discussed in class.
(c) NIST Principle of Continuous Protection
What is the NIST principle of continuous protection? See NIST SP800-160v1 appendix F. Use your own words.