General Instructions
Listen to Case study EP 79: Dark Basin by class time on January 24th we will have a question and answer session.
The goal of this homework is to get you functioning with git, GitHub, and Markdown as we will be using these tools throughout the course. This homework will take you step by step through establishing your GitHub repository, cloning that repository on your local machine, making edits and additions locally and committing them locally, and pushing changes up to your GitHub repository to share with me and the grader. Note in this class you should never do “pull requests” with GitHub.
In addition we will get hands on with some security tools and start familiar with some cybersecurity terminology. Note: you are allowed to look up definitions online but you should use your own words to describe what you find.
Tips:
- Do not use directory names with spaces in them within your repository!
- Do not use the
#or other “weird” characters in file or directory names! - Do not have directories or files in a repository that only differ only in their capitalization!
- Put your repo in a directory that is relatively easy to get to via a command line.
Use Branch master
We will use the default git master branch, i.e., no branching is required in this homework.
Use README.md for Answers
You will modify the README.md file in your repo to contain the answers to this homework.
Questions
Question 1. (5 pts)
Establishing your GitHub Classroom remote repository.
1(a)
Go to the link for GitHub classroom given out on Blackboard to create your repository for assignments for this class. Take a screen shot of the web page for your repository and save it to the images subdirectory.
Include the screen shot here from above as your solution via Markdown. I got something like this last semester (yours will be different!):
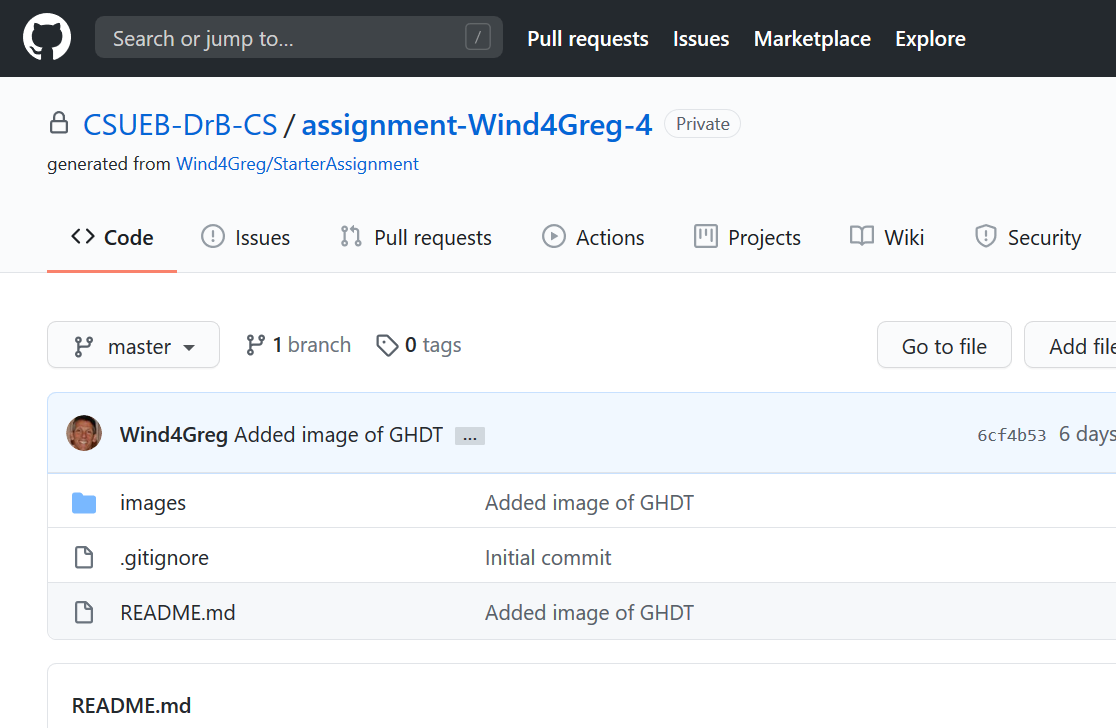
1(b)
Install Git on your local machine if needed. Clone the repository locally on your machine as explained in the class slides. Take a screen shot of the cloned directory in your file manager (you may need to make hidden folders visible to see the .git directory) and save it to the images subdirectory.
Include the screen shot here from above as your solution via Markdown. I got something like this last semester (yours will be different):
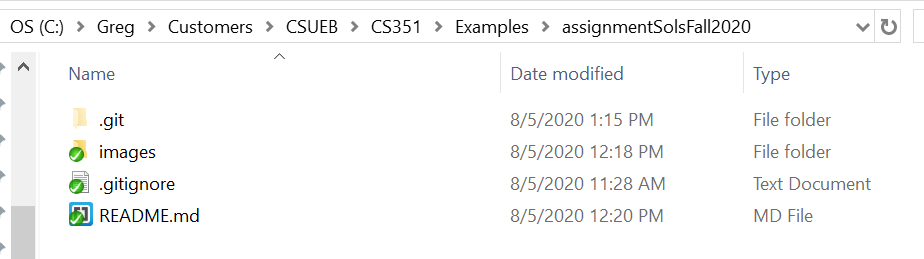
Question 2. (5 pts)
Editing, Committing, and Pushing your local version of README.MD.
2(a)
Edit the local (cloned) version of the README.md file to contain only the following information. Clear out any extra stuff that it may have had at the start. Be sure to fill in your name and NetID with the real values. Leave a blank space in your answer sheet so I know you did this question.
**Your name**
**NetID: yourNetID**
# Homework #1 Solution
## Question 1
## Question 2Commit the changes to your local repository via git.
2(b)
In the images directory delete any sample image files I may have given you. You will want to clear out screen shots from previous assignments as you start a new assignment.
Commit the changes to your local repository. Take a screen shot of the command line after you’ve done the above and issued the command git log. Include the screen shot from above as your solution via Markdown.
I got something like this last semester:
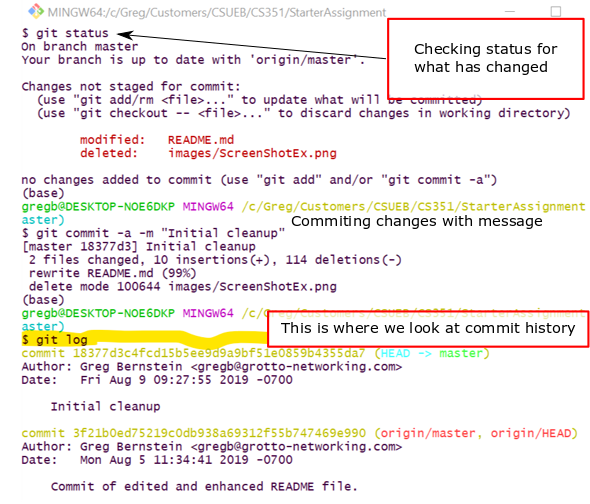
2(c)
Push your local changes up to your GitHub repository with the command: git push. Take a screenshot of the Web page of your GitHub repository that shows part of your rendered README.md file, i.e., something like
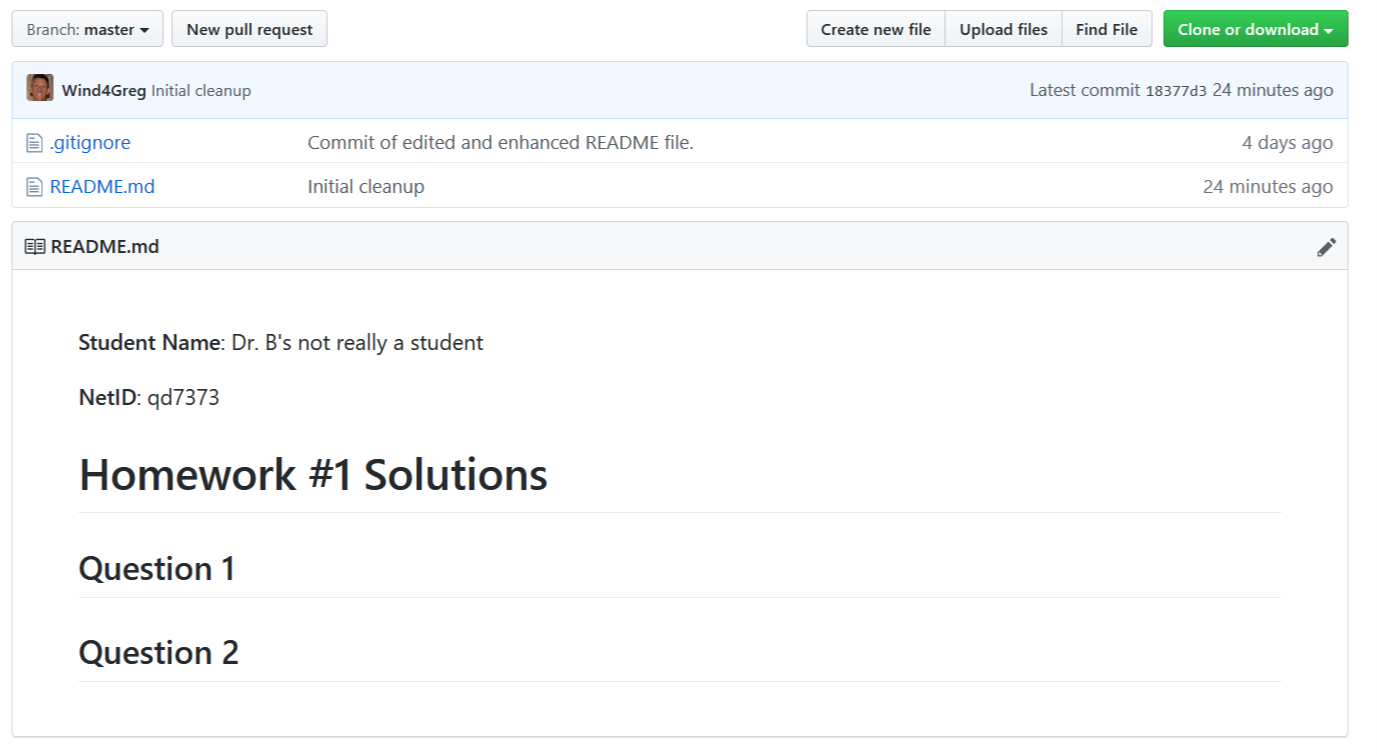
Include the screen shot from above as your solution via Markdown.
Question 3. (10 pts)
Practical Security: We will cover “identity and access management” (IAM) in a few weeks when we discuss access management in this question we will look at a couple personal and practical security aspects of this security subject.
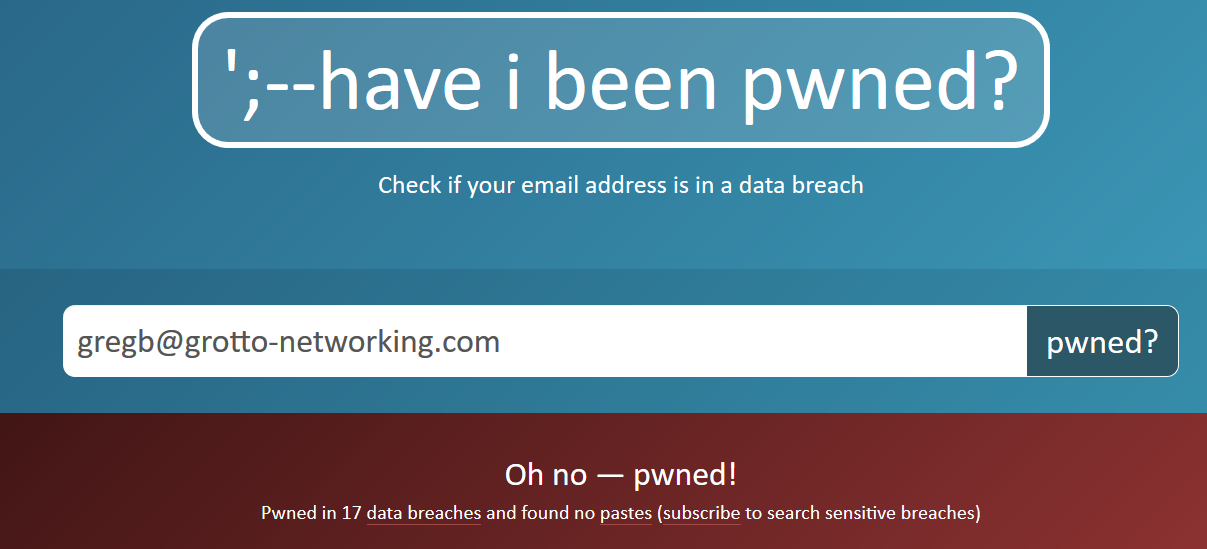
3(a) Have you been Pwnd?
Visit the website have i been pwned? and input one or more of your email addresses until you find one that has been part of a breach. If none of your emails haven’t been reported in a breach don’t feel too confident, these are only the breaches made public. Take a screenshot of your results
3(b) Credential Stuffing
What is credential stuffing? Given my results in part (a) should I be concerned with credential stuffing. What is the “credential” that is being referred to here?
3(c) Avoiding Credential Stuffing
Provide a response for each question below.
Who is responsible for preventing credential stuffing?
Are you doing currently doing anything to prevent the stuffing of your credentials?
If not you should (but are not required to) install and use a password manager tool. I currently use the free, open source, cross platform KeePassXC. This is currently recommended by the EFF and they provide a How to: Use KeePassXC.
Provide a partial screenshot of your password manager solution here (without showing any sensitive data!!!) or write a paragraph explaining why you think you are safer without such software.
Question 4. (10 pts)
4(a) The White and the Black
Why do we care what color hat (figuratively) a hacker wears? In particular, in the context of cybersecurity, what is meant by a white hat versus a black hat hacker? Note that this is common cybersecurity terminology not an indication of fashion preference.
4(b) The Red and the Blue
Another very strange bit of terminology in cybersecurity has to do with team colors. In the world of sports, e.g., football, cricket, ruby, etc…, teams can have a wide variety of colors and it is not unusual for teams to have a combination of colors, e.g., the San Francisco Giants baseball team uses orange and black. In cybersecurity there are two team colors: the red team and the blue team. How are the red and blue teams different? What do they do? Note: In general business there is a separate notion of red team which is different from that in cybersecurity.
4(c) Kiddies and APTs
In the context of cybersecurity what is a “script kiddie”? In the context of cybersecurity what is an APT? How could a defender tell the difference between a script kiddie and an APT? Might one masquerade as another?
Question 5. (10 pts)
5(a) Classified Data (Government)
In the US government classified information levels what criteria determines if information is considered confidential, secret, or top secret?
In addition to a security clearance what else do you need to have to access “classified information”?
Why are codewords used along with a security level such as secret?
5(b) Classified Data (Yours)
What set of rules/laws govern how I should handle your homework scores, test scores, attendance, etc… in this class?
What set of rules/laws govern how your health care provider shares information about visits to your doctor, current medicines you might be taking, chronic illnesses, or pre-existing conditions?
If I run a website in California are there any rules/laws that I need to know about concerning how I treat “web logs”. What about if citizens of the EU (European Union) visit my website?
5(c) System Types IT vs. OT
How does operational technology (OT) differ from general information technology (IT)? Use the NIST definition of OT from the course notes.
How does OT as a category compare with that of industrial control system (ICS)? Where are ICS used? Why are ICS systems coming under attack now when they didn’t before?
Does critical infrastructure always involve ICS? If not give an example of a critical infrastructure sector that does not use ICS.